G you must write a python script name laplace_equal_segments. Py that will create the linear system of equations 7. You will solve the problem using the linear algebra function solve in scipy. Your program should
Answers
The Python code for the laplace_equal_segments.py script that creates the linear system of equations 7 and solves it using the linear algebra function solve in scipy is given below:
import numpy as np
from scipy.linalg import solve
def laplace_equal_segments(n):
"""
Solves the Laplace equation on the unit interval with n equal segments using the method of finite differences.
"""
# Create a (n+1)x(n+1) matrix A
A = np.zeros((n+1, n+1))
for i in range(1, n):
A[i, i] = -2.0
A[i, i-1] = 1.0
A[i, i+1] = 1.0
A[0, 0] = A[n, n] = 1.0
# Create a (n+1)x1 vector b
b = np.zeros(n+1)
b[0] = b[n] = 0.0
# Solve the linear system Ax = b
x = solve(A, b)
return x
Explanation:
The function laplace_equal_segments(n) takes an integer n as input, which is the number of equal segments we want to divide the unit interval into. The function creates a (n+1)x(n+1) matrix A using finite differences to discretize the Laplace equation on the unit interval, and then creates a (n+1)x1 vector b with boundary conditions. Finally, it solves the linear system Ax = b using the solve function from scipy.linalg, and returns the solution vector x. To use the function, simply call laplace_equal_segments(n) with your desired value of n. For example, to solve the Laplace equation with 10 equal segments, you would call laplace_equal_segments(10).
To know more about the Laplace equation click here:
https://brainly.com/question/31401711
#SPJ11
Related Questions
Select the correct answer.
Which relationship is possible when two tables share the same primary key?
А.
one-to-one
B.
one-to-many
C.
many-to-one
D.
many-to-many
Answers
Answer:
Many-to-one
Explanation:
Many-to-one relationships is possible when two tables share the same primary key it is because one entity contains values that refer to another entity that has unique values. It often enforced by primary key relationships, and the relationships typically are between fact and dimension tables and between levels in a hierarchy.
Design 16: 1 Multiplexer using 8: 1 Multiplexer constructed using 4:1 Multiplexer constructed using 2:1 Multiplexer. b. Give the Internal structure of 2:1 Multiplexer using SOP, POS, NAND, NOR logic gates. d. Write the verilog code for Multiplexer in different styles and Verify the results using the truth table and show the output waveform. e. Show the steps and procedure in the tool used.
Answers
For the internal structure of a 2:1 multiplexer, we can use SOP (Sum of Products), POS (Product of Sums), NAND, or NOR logic gates. Each of these methods has its own gate-level representation.
To design a 16:1 multiplexer, we can use smaller multiplexers in a hierarchical manner. We can start by using four 2:1 multiplexers to construct a 4:1 multiplexer. Then, we can use two of these 4:1 multiplexers to construct an 8:1 multiplexer. Finally, we can use two of these 8:1 multiplexers to build a 16:1 multiplexer.
For the internal structure of a 2:1 multiplexer, we can use SOP (Sum of Products), POS (Product of Sums), NAND, or NOR logic gates. Each of these methods has its own gate-level representation.
To write a Verilog code for a multiplexer, you can use different styles such as behavioral, dataflow, or structural. The code will vary depending on the style chosen.
To verify the results, you can use a truth table to compare the expected output with the actual output. You can also simulate the code in a hardware description language (HDL) tool and observe the waveform output.
Please let me know if you need further assistance with any specific step or concept.
To know more about multiplexer visit:
https://brainly.com/question/33277473
#SPJ11
A site has been issued the ip address of 192. 168. 10. 0/24. The largest network contained 100 hosts and was given the lowest numbered network number possible. The second largest network has 60 hosts. If it is given the next network number, what network number and mask will be assigned to the second largest network?
Answers
The network number and mask assigned to the second largest network would be 192.168.10.128/26.
The site has been assigned the IP address of 192.168.10.0/24, which means that it has been allocated 256 IP addresses, ranging from 192.168.10.0 to 192.168.10.255.
The largest network contained 100 hosts, so it requires 7 bits for the host part of the address (2^7 - 2 = 126 usable hosts). This leaves 24 - 7 = 17 bits for the network part of the address, which gives us 2^17 = 131,072 possible network addresses. The lowest numbered network number possible for this network size is 192.168.10.0/25 (subnet mask of 255.255.255.128).
The second largest network has 60 hosts, so it requires 6 bits for the host part of the address (2^6 - 2 = 62 usable hosts). This leaves 24 - 6 = 18 bits for the network part of the address, which gives us 2^18 = 262,144 possible network addresses. The next network number would be 192.168.10.128/26 (subnet mask of 255.255.255.192).
Therefore, the network number and mask assigned to the second largest network would be 192.168.10.128/26.
To learn more about network number
https://brainly.com/question/29506804
#SPJ11
All dogs = 199999990158161231
A = B
B = C
C = D
Please help this question makes 0 sense but my teacher asked me it so I gotta figure it out
Answers
Answer:
C=D cause d spells dogs jk I really dont know
Answer:
B
Explanation:
Queries are a very useful object in a database, please explain why.
Answers
Answer:
they tell the producer what to do to make their website better
Explanation:
HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!
Express the diagram in the form of a logic statement. [2]
P = ________________________
3. (a) Complete the truth table below for the logic circuit which is made up of NAND gates only.
![HELPPPPPPPPPPPPPPPPPPPPPPPPPPPPPPP!!!Express the diagram in the form of a logic statement. [2] P = ________________________3.](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/NoE1DnieovxjZViB66UnB8fBINlICMCx.jpeg)
Answers
Answer:
different or difference between Dot-matrix and Daisy-wheel printer
Which of the following statements would you use to creat a vector of ints named ages with an initial size of 20 elements?
a. vector int(20);
b. vector<20> ages(int);
c. vector<20> int(ages);
d. vector ages(20);
Answers
To create a vector of ints named ages with an initial size of 20 elements, the correct statement to use would be option d. The syntax for this statement would be "vector ages(20);".
"Vector" specifies the data type of the vector, "ages" is the name of the vector, and "(20)" indicates the initial size of the vector. Option a creates a vector of ints with no name and no initial size. Option b is not a valid statement.
Attempting to create a vector of 20 elements using the vector named "ages", which does not exist yet.
because it creates a vector of ints named "ages" with an initial size of 20 elements. The "vector" syntax specifies the data type of the vector as int, and the "(20)" indicates the initial size of the vector.
To know more about vector visit:
https://brainly.com/question/7205645
#SPJ11
How can IT help in the new product development process? (Explain
in 3 paragraphs)
Answers
Information technology (IT) plays a crucial role in the new product development process, providing significant advantages and support throughout various stages.
1. Data Analysis and Market Research: IT enables extensive data collection and analysis, empowering organizations to gain valuable insights into customer preferences, market trends, and competitor offerings.
With the help of IT tools and software, companies can conduct comprehensive market research, perform customer surveys, analyze social media data, and track online consumer behavior.
2. Collaboration and Communication: IT facilitates seamless collaboration and communication among cross-functional teams involved in the new product development process.
Through project management software, cloud-based document-sharing platforms, and virtual communication tools, teams can collaborate effectively regardless of their geographical locations.
3. Prototyping and Simulation: IT enables the creation of virtual prototypes and simulations, saving time and costs associated with physical prototyping.
Computer-aided design (CAD) software allows product designers to create detailed and realistic digital prototypes, facilitating quick iterations and improvements.
In conclusion, IT plays a critical role in the new product development process by enabling data-driven decision-making, fostering collaboration among teams, and facilitating virtual prototyping and simulation.
Know more about Information technology:
https://brainly.com/question/32169924
#SPJ4
In the cases of int, byte, long, short (In Java) Can you give the heirachy in ascending order?
Answers
Answer:
Byte Short Int Long
Explanation:
Byte's 8 bit, short's 16, int's 32, and long's 65.
1. In a packet-switched network, messages will be split into smaller packets, and these packets will be transmitted into the network. Consider the source sends a message 5 Mbits long to a destination. Suppose each link in the figure is 10 Mbps. Ignore propagation, queuing, and processing delays. (a) Consider sending the message from source to destination without message segmentation. Find the duration to move the message from the source host to the first packet switch? Keeping in mind that each switch uses store-and-forward packet switching, execute the total time to move the message from source host to destination host? (6 marks) (b) Now, suppose that the message is segmented into 400 packets, each 20 kilobits long. Execute how long it takes to move the first packet from the source host to the first switch. When the first packet is sent from the first switch to the second switch, the second packet is sent from the source host to the first switch. Discover when the second packet will be fully received at the first switch. (6 marks)
Answers
In a packet-switched network, without message segmentation, the time to move the entire 5 Mbit message from the source host to the first packet switch is determined by the link capacity of 10 Mbps. It takes 5 milliseconds to transmit the message.
When the message is segmented into 400 packets, each 20 kilobits long, the time to move the first packet from the source host to the first switch is still 5 milliseconds. The second packet will be fully received at the first switch when the first packet is being sent from the first switch to the second switch, resulting in no additional delay.
(a) Without message segmentation, the time to move the entire 5 Mbit message from the source host to the first packet switch can be calculated using the formula: Time = Message Size / Link Capacity. Here, the message size is 5 Mbits and the link capacity is 10 Mbps. Thus, the time to move the message is 5 milliseconds.
Since each switch in store-and-forward packet switching requires the complete packet to be received before forwarding, the total time to move the message from the source host to the destination host would also be 5 milliseconds, assuming there are no propagation, queuing, and processing delays.
(b) When the message is segmented into 400 packets, each 20 kilobits long, the time to move the first packet from the source host to the first switch remains the same as before, 5 milliseconds. This is because the link capacity and the packet size remain unchanged.
As for the second packet, it will be fully received at the first switch when the first packet is being sent from the first switch to the second switch. Since the link capacity is greater than the packet size, there is no additional delay for the second packet. This is because the transmission of the first packet does not affect the reception of subsequent packets as long as the link capacity is sufficient to handle the packet size.
Learn more about packet-switched network here :
https://brainly.com/question/30756385
#SPJ11
The standard format rules for a professional letter should be followed.
True
False
Answers
Question #2
Multiple Choice
What is the index of 7 in this list?
[5, 6, 10, 7, 3, 2.5]
O7
04
02
03
Answers
Answer:
3
Explanation:
Given set - [ 5, 6, 10, 7, 3, 2.5 ]
Index - 0, 1 , 2, 3, 4, 5
∴ we get
Index of element 7 is 3.
Reason -
The method index( ) returns the lowest index in the list where the element searched for appears.
Femke went to a computer lab and connected her laptop to the WiFi network. She later received an email from the lab administrator warning that the WiFi network was in fact a rogue access point.
Which of the following could have occurred while she was connected to the rogue access point?
Answers
Femke may have experienced several consequences while connected to the rogue access point.
Could Femke have encountered any issues while connected to the rogue access point?When Femke connected her laptop to the rogue access point in the computer lab, she exposed herself to potential security risks. Rogue access points are unauthorized and can be set up by malicious actors to deceive users into connecting to them. Once connected, the attacker can intercept network traffic, steal sensitive information, and even launch various attacks on the connected devices.
The dangers of rogue access points, which can lead to unauthorized access and compromise the security of users and their devices. Attackers can eavesdrop on communications, perform man-in-the-middle attacks, and distribute malware. It is crucial to be vigilant when connecting to Wi-Fi networks and ensure they are authorized and secure.
Learn more about access point
brainly.com/question/29346507
#SPJ11
Is MOOC's potentially harmful to copyright? Why or why not ?
Answers
Answer:
Fair-use exceptions to traditional copyright protection face challenges as well, given a MOOC's potential for global reach. Nonetheless, fair use and MOOCs are not mutually exclusive ideas. MOOCs remain an experiment...
language form comprises which of the following elements? question 25 options: a) syntax b) pragmatics c) semantics d) meaning making
Answers
Syntax (grammar) is the set of language components that are included under "form" as syntax is the set of rules that are used to describe and explain the ways in which words are related in a sentence.
What is Grammar?
It is the structure and system of a language, or of languages in general, which is usually thought to include syntax and morphology.
Grammar is a language's system. Grammar is sometimes referred to as a language's "rules," but no language has rules*. When we say "rules," we mean that someone created the rules first and then spoke the language, as if it were a new game.
However, languages did not begin in this manner. Languages evolved from people making sounds into words, phrases, and sentences. There is no universal language. Every language evolves over time. What we call "grammar" is simply a snapshot of a language at a specific point in time.
What Is Syntax?
In English, syntax refers to the arrangement of words and phrases in a specific order. It is possible to change the meaning of an entire sentence by changing the position of just one word. Every language has its own set of rules for which words go where, and skilled writers can bend these rules to make sentences sound more poignant or poetic.
To learn more about Syntax, visit: https://brainly.com/question/831003
#SPJ4
How do u kiss someone and not feel werid about it afterwards
Answers
Answer: just don't kiss someone
Explanation: easy, but if you do then just leave. duh
WILL GIVE BRAINLIEST, JAVA PROGRAMMING PLS HELP
Here is the prompt:
The code provided is intended to use a while loop to print the first 9 multiples of an integer entered by the user. For example if the user enters 5, the program should print the numbers 5, 10, 15.,... up to 45, one per line. Debug the code so it functions as described.
Here is the code:
Scanner scan = new Scanner(System.in);
int num = scan.nextInt();
int fac = 1;
while(fac < 9){
System.out.println(num*fac);
fac++;
System.out.println(num*fac);
}
}
}
Answers
Answer:
import java.util.Scanner;
public class Main {
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
int num = scan.nextInt();
int fac = 1;
while(fac <= 9){
System.out.println(num*fac);
fac++;
}
}
}
Explanation:
Hello, I tried out your program, and I just wanted to point out some little issues :)
You need to import the java.util.Scanner in order to use Scanners :)
Also, (not sure if you just didn't copy the stuff at the start) but you need the public class and the public static void main.
Last of all, since you're printing out all of the first 9 multiples, the 9th is included, so you use <= instead of <.
I have sent you the right code above ^^ :)
Please mark brainliest if this has helped you.
Debugging a code involves locating and fixing the errors/bugs in the code.
The error in the code is that, the following print statement is repeated twice
System.out.println(num*fac);
The correction is to remove the first appearance of
System.out.println(num*fac);
So, the corrected code is as follows
Scanner scan = new Scanner(System.in);
int num = scan.nextInt();
int fac = 1;
while(fac < 9){
System.out.println(num*fac);
fac++;
}
Read more about debugging at:
https://brainly.com/question/23527739
To convert a binary number into its hexadecimal form: AStart by grouping the digits into 4-bit groups BStart by grouping the digits into 6-bit groups CStart by grouping the digits into 8-bit groups DStart by grouping the digits into 2-bit groups
Answers
Answer:
The answer is "Option A"
Explanation:
The Hexa-decimal numeric method has become one of the forms of numerical definitions refer to a base value of 16. There are only 16 symbols and the numerical value was used that are from 0 to 9 and A to F, in which from 0 to 9 has 10 numbers, and from A to F has 6 numbers, which is equal to 16 bits.
In the hexadecimal, only two separate hex digit is used for each nibble (or group of 4-bits), it will join by the 8-bit binary number.
Robert and Anne, a married couple filing jointly, have an adjusted gross income of $68,676. They claim two exemptions, and can deduct $3,752 for charitable donations, $3,375 for interest on their mortgage, and $959 from city income tax. If the standard deduction for a married couple filing jointly is $8,350 and exemptions are worth $3,650 apiece, what is their total taxable income?
Answers
Answer:
the answer is B
Explanation:
Just took the test
The total taxable income of Robert and Anne, who file jointly as a married couple, is $53,026.
Data and Calculations:Adjusted gross income of Robert and Anne = $68,676
Claimable Exemptions:
Charitable donations = $3,752
Mortgage interest = $3,375
City income tax = $959
Standard Exemptions:
Standard deduction for married couple = $8,350
Exemptions = $3,650 per couple
Taxable income:Adjusted gross income $68,676
Standard deductions (8,350)
Exemptions (7,300) ($3,650 x 2)
Taxable income = $53,026
Thus, the total taxable income of Robert and Anne, who file jointly as a married couple, is $53,026.
Learn more about taxable income https://brainly.com/question/10137785
You have a network address of 220.16.22.0 and have selected 255.255.255.224 as the subnet mask value. How many possible subnets are there
Answers
The selected subnet mask value of 255.255.255.224 means that there are 5 bits used for the subnet portion of the address. This gives a total of 2^5 or 32 possible subnets.
To determine the number of possible subnets:To determine the number of possible subnets with a network address of 220.16.22.0 and a subnet mask of 255.255.255.224, follow these steps:
1. Convert the subnet mask to binary: 255.255.255.224 is 11111111.11111111.11111111.11100000 in binary.
2. Count the number of consecutive 1s in the subnet mask: There are 27 consecutive 1s.
3. Calculate the number of subnet bits: Subtract the number of consecutive 1s from the total number of bits (32 bits for an IPv4 address). 32 - 27 = 5 subnet bits.
4. Calculate the number of possible subnets: Use the formula 2^n, where n is the number of subnet bits. 2^5 = 32 possible subnets.
So, with a network address of 220.16.22.0 and a subnet mask of 255.255.255.224, there are 32 possible subnets.
To know more about Subnet mask.
visit:
https://brainly.com/question/31539525
#SPJ11
Answer please in order

Answers
Answer:
analogue; discrete; sampled; sample rate; bit depth; bit rate; quality; larger; file size.
Explanation:
Sound are mechanical waves that are highly dependent on matter for their propagation and transmission.
Generally, it travels faster through solids than it does through either liquids or gases.
Sound is a continuously varying, or analogue value. To record sound onto a computer it must be turned into a digital, or discrete variable. To do this, the sound is sampled at regular intervals; the number of times this is done per second is called the sample rate. The quality of the sound depends on the number of bits stored each time - the bit depth. The number of bits stored for each second of sound is the bit rate and is calculated by multiplying these two values (sample rate and bit depth) together - kilobits per seconds (kbps). The higher these values, the better the quality of the sound stored, but also the larger the file size.
to reverse the last change you made in a presentation file you click the undo button on the quick access toolbar true or false?
Answers
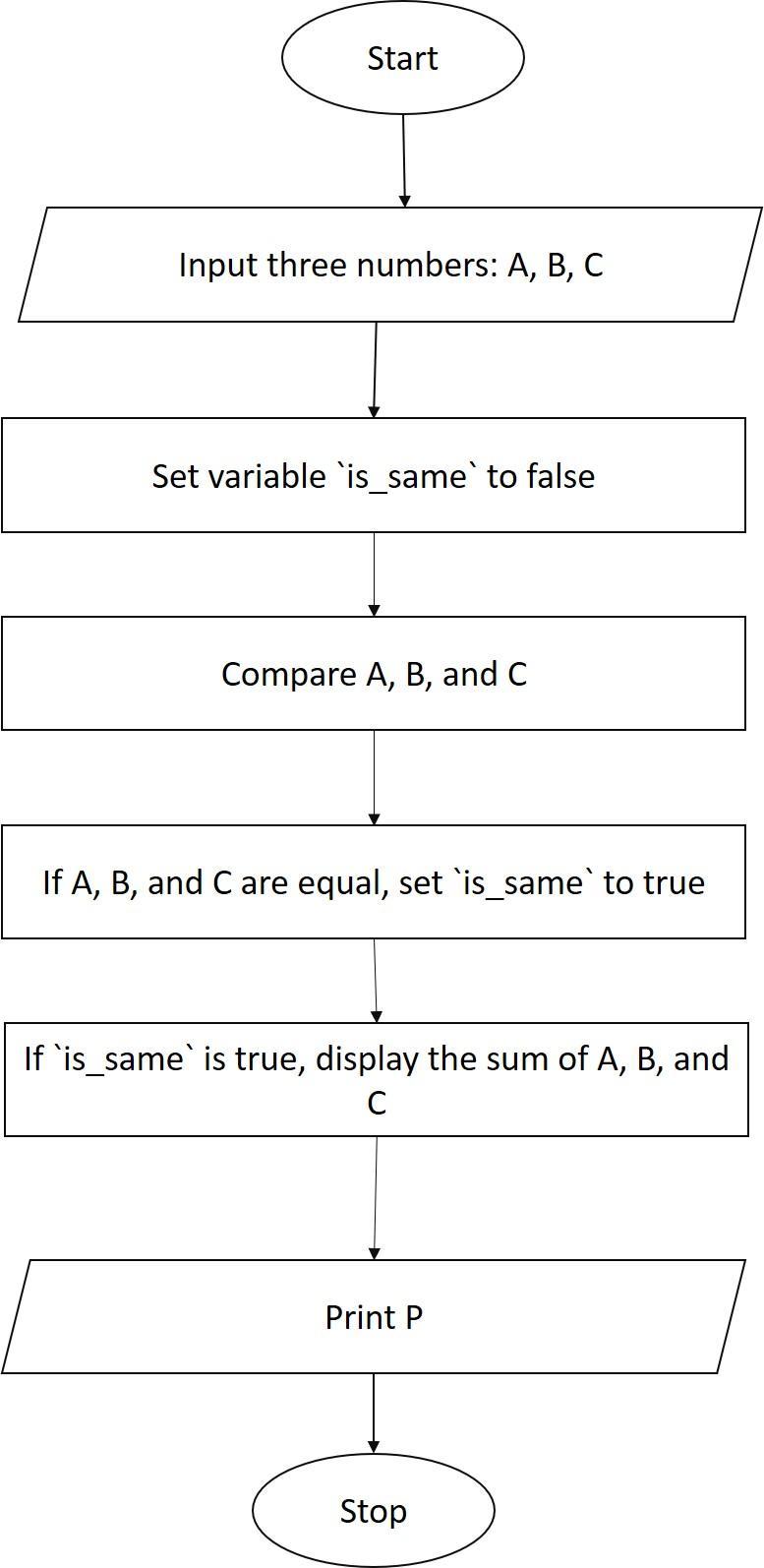
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
Any aesthetic pomodoro timer apps you know? That are free* Something similar to pomofocus.io -> however I cannot download it as an app, just an extension ;(
Answers
Answer:
hi! i personally have never used a focus timer app but after looking for some, it seems like a great idea:) attached i have some apps i found!
Explanation:


May I Ask for Quick Assistance?
1: Emails should be written in the same way as regular letters, with the same etiquette expected: True False
2: It is good to ask questions in a live class, even when online: True False
3: What element should be included in a professional email?
A: Picture
B: Emoji
C: Textism
D: Clear subject line
6: What is NOT an example of nonverbal communication?
A: Angry Tone of Voice
B: Sending a Formal Email
C: Nervous Body Language
D: Maintaining eye contact
7: Textisms serve the same function as ellipses: True False
Answers
Answer:
1. True
2. True
3. B
6. A
7. Idk
2.true
3.D
6.C
7.false
Hope it help! I may not be 100% correct but I hope this is good!
research suggests that people are happier when they are supported by a network of ______.
Answers
Research suggests that people are happier when they are supported by a network of social connections. Social connections refer to the relationships that people have with family, friends, colleagues, and other individuals in their community.
These connections provide emotional, social, and practical support to individuals, which contributes to their overall happiness and well-being. Studies have shown that social connections are crucial for mental health and emotional resilience. Having a strong social network can help individuals cope with stress, overcome challenges, and feel a sense of belonging and purpose. Additionally, social connections can help individuals feel more positive emotions, such as joy, gratitude, and contentment.
On the other hand, social isolation and loneliness can have negative impacts on mental health and overall well-being. Lack of social connections can increase the risk of depression, anxiety, and other mental health issues. Therefore, it is important for individuals to cultivate and maintain their social connections, whether it be through joining social clubs, volunteering, or simply spending more time with loved ones. In summary, having a network of social connections is crucial for happiness and well-being. Social connections provide emotional, social, and practical support, which contributes to individuals' overall mental health and resilience. It is important for individuals to prioritize building and maintaining their social connections to promote their own happiness and well-being.
Learn more about social network here-
https://brainly.com/question/28269149
#SPJ11
What is the most important part of a state?
Answers
The most important part of a State is; Sovereignty
State SovereigntyThe most important part of the state is Sovereignty followed by other elements like population, government, and territory.
The reason for Sovereignty as the most important and most exclusive part of a state is because it is the basis upon which the state regulates all aspects of the life of the people living in that state.
Read more about State Sovereignty at; https://brainly.com/question/7226587
A page can have a high Needs Met rating even if it is not related to the topic of the query.
True
False
Answers
Using Ocean Data View, Im confused on how to do this?
Mixing of two water bodies
The next data set is stored in the SAVE folder, and contains hydrographic and nutrient data from the South Atlantic Ventilation Experiment in the file SAVE.var. The following questions are related to a combination of two legs (LG5 & LG6) to form a North-South transect. It is best to answer these parts using the SECTION view (F11). To change the variable that is plotted in SECTION view for the default dataset, right-click the mouse, and choose a new z value.
When two water bodies mix, the resulting water has temperature and salinity properties that are exactly proportional to ratio of the original two water bodies.
The proportion of water type II is
a *100% (a+b)
Remember, the distance between two points on a graph is equal to the square root of the difference in salinities of the two points squared plus the difference in temperature of the two points squared (Pythagoras’ theorem).
Using information obtained from the North- South section given in the default dataset of Ocean Data View , find a representative value for the temperature and salinity of both North Atlantic Deep Water and Antarctic Deep Water. Then find a location in which you think the two water bodies might be mixing, and record the temperature and salinity measured at this location. Finally, work out the proportion of Antartic Deep Water in the water sampled at your mixing location.
Answers
To determine the proportion of Antarctic Deep Water in the mixed water sample, you need to find representative values for the temperature and salinity of both North Atlantic Deep Water and Antarctic Deep Water. Then, identify a location where these two water bodies might be mixing and record the measured temperature and salinity at that location.
To begin, you'll need to examine the North-South section provided in the default dataset of Ocean Data View. By analyzing the temperature and salinity profiles along the transect, you can identify regions where the characteristics of North Atlantic Deep Water and Antarctic Deep Water are present.
Once you have determined representative values for the temperature and salinity of both water bodies, you can search for a location where these two water masses might be mixing. This mixing zone would likely exhibit intermediate temperature and salinity values compared to the original water bodies.
By recording the temperature and salinity measurements at the identified mixing location, you can then apply the given proportion formula: a * 100% / (a + b), where 'a' represents the proportion of Antarctic Deep Water and 'b' represents the proportion of North Atlantic Deep Water. This calculation will yield the proportion of Antarctic Deep Water in the sampled mixed water.
Remember to consider the distance between data points using the Pythagorean theorem, which takes into account both the difference in salinities and the difference in temperatures.
Learn more about Antarctic
brainly.com/question/32049453
#SPJ11
You carried out a PERT analysis of a very large activity-event network using only slightly skewed or symmetric beta distribution models for the activity durations. Your analysis yields a mean duration of 56.2 time units for the critical path with a variance of 3.4. What is your best estimate of the probability of successful project completion in 57 time units or less? Provide your answer as a number between 0 and 1 with 3 decimals (3 digits after the decimal point, for example: 0.123).
Answers
PERT (Program Evaluation and Review Technique) is a network analysis technique commonly used in project management.
It is particularly useful when there is a high level of uncertainty surrounding the duration of individual project activities. PERT uses probabilistic time estimates, which are duration estimates based on using optimistic, most likely, and pessimistic estimates of activity durations, or a three-point estimate.
These estimates help to identify the likelihood of meeting project deadlines and can assist project managers in developing effective project schedules and resource allocation plans. Overall, PERT is an important tool for managing complex projects with uncertain activity durations.
To know more about project management, refer to the link:
brainly.com/question/4475646#
#SPJ4