Given two integers as user inputs that represent the number of drinks to buy and the number of bottles to restock, create a VendingMachine object that performs the following operations: Purchases input number of drinks Restocks input number of bottles Reports inventory The VendingMachine is found in VendingMachine. Java. A VendingMachine's initial inventory is 20 drinks. Ex: If the input is:
Answers
To create a VendingMachine object in Java that performs the operations of purchasing drinks, restocking bottles, and reporting inventory based on user input, we can define a class called VendingMachine with methods for each operation.
First, we need to define the initial inventory of the VendingMachine, which is 20 drinks. We can do this by declaring a private integer variable called inventory and initializing it to 20 in the constructor of the VendingMachine class.
Next, we can define a method called purchaseDrinks(int numDrinks) that takes an integer argument representing the number of drinks to purchase. Inside this method, we can subtract the input number of drinks from the inventory and return a string message indicating the number of drinks purchased and the remaining inventory.
Similarly, we can define a method called restockBottles(int numBottles) that takes an integer argument representing the number of bottles to restock. Inside this method, we can add the input number of bottles to the inventory and return a string message indicating the number of bottles restocked and the updated inventory.
Finally, we can define a method called reportInventory() that returns the current inventory of the VendingMachine as an integer value.
With these methods defined, we can create a VendingMachine object in the main method of our program, prompt the user for input using a Scanner object, and call the appropriate methods based on the user's input to perform the desired operations on the VendingMachine object.
To learn more about Java programming, visit:
https://brainly.com/question/25458754
#SPJ11
Related Questions
After selecting the heading and opening the Style dialog box, Jemima now wants to open the Modify Style dialog box. How does she do this?
Answers
Answer:
The answer is given below
Explanation:
They are many different styles present in Microsoft word so as to fit the taste of the user. If the user is not satisfied with the style list presented in Microsoft word, the user can decide to modify the style to fit his/her requirement.
In office 16, to modify a style, on the home menu, navigate to the style gallery and right click on the style you wish to modify. Right click on modify and the modify style dialog box would open, and the user can make changes to the font size, spacing, paragraph e.t.c.
By clicking the heading one-drop down arrow
Computerized spreadsheets that consider in combination both the
risk that different situations will occur and the consequences if
they do are called _________________.
Answers
Both answers are correct
The given statement refers to computerized spreadsheets that consider in combination both the risk that different situations will occur and the consequences if they do which are called decision tables.
A decision table is a form of decision aid. It is a tool for portraying and evaluating decision logic. A decision table is a grid that contains one or more columns and two or more rows. In the table, each row specifies one rule, and each column represents a condition that is true or false. The advantage of using a decision table is that it simplifies the decision-making process. Decision tables can be used to analyze and manage complex business logic.
In conclusion, computerized spreadsheets that consider in combination both the risk that different situations will occur and the consequences if they do are called decision tables. Decision tables can help simplify the decision-making process and can be used to analyze and manage complex business logic.
To know more about spreadsheets visit:
https://brainly.com/question/31511720
#SPJ11
Which Annotation tool provides the ability to convert the mouse icon when giving a presentation to better focus the
audience attention?
O Arrow
0 Ink Color
O Eraser
O Laser Pointer
Answers
Answer:
Laser Pointer
Explanation:
How are console apps displayed?
a) In a window form.
b) In the Command Prompt.
c) Console apps have no output to
display.
d) It depends.
Answers
The Command Prompt displays console apps. Some consumers simply favour console-based programmes, while some businesses continue to employ legacy console programmes for critical data processing operations.
A console application is a software application that is intended to be used through a text-only computer interface, such as a text terminal, the command-line interface of some operating systems (Unix, DOS, etc.), or the text-based user interface found in the majority of graphical user interface (GUI) operating systems, such as the Windows Console in Microsoft Windows, the Terminal in macOS, and xterm in Unix.
Modern programming environments, including Visual Studio and the.NET Framework on Microsoft Windows, nevertheless support the creation of console programmes. By eliminating the complexity of a graphical user interface(GUI), it makes learning a new programming language easier.
To learn more about Command Prompt click here:
brainly.com/question/29491045
#SPJ4
Write any four causes of cyber crime
Answers
The Victim Deserves It
Self-loathing
It Becomes an Addiction
during cr image extraction, what is the device used to collect light emitted by storage plate phosphors?
Answers
The device used to collect light emitted by storage plate phosphors during CR (Computed Radiography) image extraction is called a photomultiplier tube (PMT).
A photomultiplier tube is a highly sensitive electronic device that converts light into an electrical signal. In the context of CR image extraction, when the storage plate is exposed to X-rays, the phosphor crystals on the plate get excited and store energy. When the plate is scanned with a laser, the stored energy is released as light. The photomultiplier tube is positioned to collect this emitted light and convert it into an electrical signal.
The electrical signal produced by the PMT is then amplified, digitized, and processed to reconstruct the X-ray image stored on the storage plate. The high sensitivity and efficiency of photomultiplier tubes make them suitable for capturing and converting the low-intensity light emitted by the phosphors into a usable electronic signal for image extraction in CR systems.
Learn more about Computed Radiography here:
https://brainly.com/question/10128598
#SPJ11
What type of route has a network address with a subnet mask that is less than the classful equivalent?
Answers
A network address with a subnet mask that is less than the classful equivalent refers to a subnetting technique known as Variable Length Subnet Masking (VLSM).
Suppose we have a class B network address, 172.16.0.0, which has a default subnet mask. This means that the network can accommodate up to 65,534 hosts say we want to divide this network into two subnets: one with 500 hosts and another with 1000 hosts.
In conclusion, a network address with a subnet mask that is less than the classful equivalent refers to the practice of using VLSM to divide a network into subnets with varying subnet masks based on the desired number of hosts in each subnet. This allows us to utilize the available IP address space more effectively.
To know more about equivalent visit:
https://brainly.com/question/25197597
#SPJ11
an analyst saw an alert indicating that a host was beaconing to a malicious network, but discovered the incident was outdated and no compromised occurred. this alert is an example of a ...
Answers
The alert indicating that a host was beaconing to a malicious network, but the incident was outdated and no compromise occurred, is an example of a false positive.
A false positive occurs when an alert or alarm is triggered by a security tool or system, indicating the presence of a security threat or attack, but the alert is not actually caused by a security breach.
False positives can occur for various reasons, such as misconfigurations, software bugs, or outdated threat intelligence. False positives can be costly as they can lead to unnecessary investigations, consume resources, and create a sense of alert fatigue among security analysts. Therefore, it is essential to minimize false positives and optimize the performance of security tools and systems by tuning their parameters, updating threat intelligence, and conducting regular testing and validation.
Learn more about network here:
https://brainly.com/question/29350844
#SPJ11
What are the Key Process Areas for CNNi Level 2?
Answers
The Key Process Areas (KPAs) for CNNi Level 2 are as follows: 1. News-gathering 2. Storytelling 3. Delivery 4. Technical Production 5. Teamwork 6. Communication 7. Planning and Organization 8. Initiative 9. Professionalism 10. Personal Development
The Key Process Areas (KPAs) are general categories of abilities and accomplishments that all journalists at CNN International should have, regardless of their specialty or role. KPAs are intended to outline a range of abilities that a CNNi journalist should have at each level. The ten KPAs at Level 2, as previously noted, are News-gathering, Storytelling, Delivery, Technical Production, Teamwork, Communication, Planning and Organization, Initiative, Professionalism, and Personal Development.
KPAs, in general, are used to evaluate a journalist's professional growth and advancement potential. They represent a framework of anticipated behaviors and actions that journalists should demonstrate in order to advance to the next level.
Learn more about KPA's: https://brainly.com/question/9940533
#SPJ11
For the execution of a successful information strategy, staff synchronization _____. (Select all that apply.) relies on informed commander's guidance begins at the execution phase of operations requires cross-talk and cross-representation breaks down staff planning into clearly defined major subsets integrates products does not impact actions, words, and images
Answers
For the execution of a successful information strategy, staff synchronization relies on informed commander's guidance.
What is the above about?A successful information strategy, staff synchronization is one that depends on informed commander's guidance.
And as such, if one say that For the execution of a successful information strategy, staff synchronization relies on informed commander's guidance. it is a true statement.
Learn more about information strategy from
https://brainly.com/question/8368767
#SPJ1
HELP ME ⚠️‼️⚠️‼️ DUE IN EXACTLY 27 MINUTES
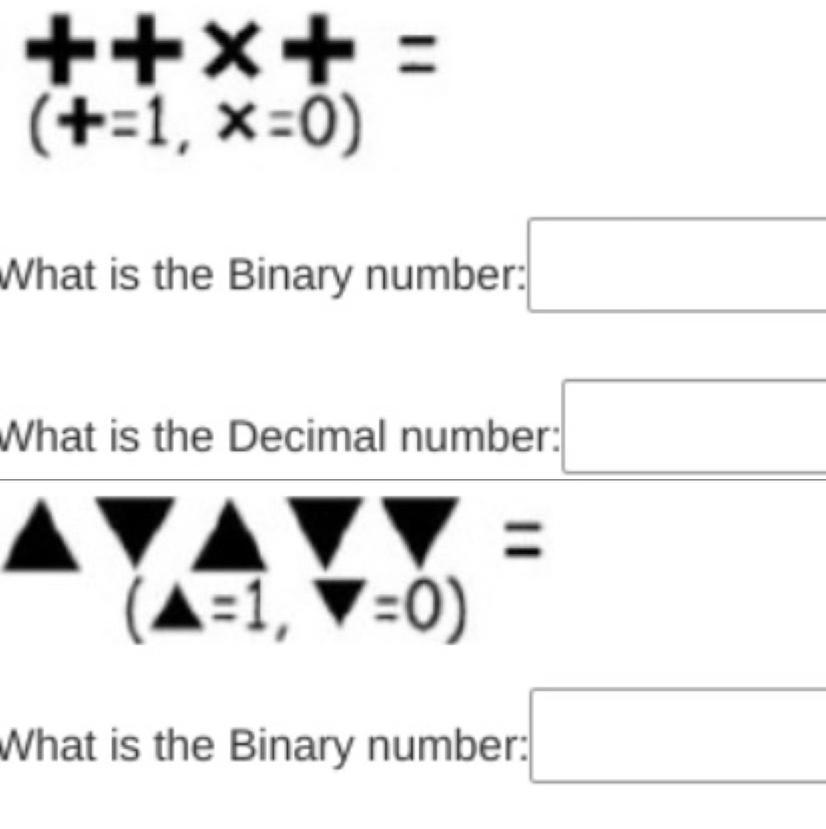
Answers
Answer:
the binary for the first one is 1101
and the binary for the second one is 10100
Explanation:
43. What are the three major ways of authenticating users? What are the pros and cons of each approach?
Answers
The three major ways of authenticating users are:Password-based authentication,Two-factor authentication,Public key infrastructure (PKI) authentication.
Password-based authentication: This is the most common form of authentication, where a user provides a username and a password to prove their identity. The password is compared to the stored password for that user, and if it matches, the user is authenticated.
Pros:
It is easy to implement and use.
It is familiar to most users.
It can be used in various systems and applications.
Cons:
Passwords can be guessed or stolen.
Users tend to use weak passwords, reuse passwords across multiple accounts, and write them down, making them vulnerable to attacks.
Passwords can be intercepted during transmission, if the communication is not properly secured.
Two-factor authentication (2FA): In this method, the user is required to provide two different forms of authentication to prove their identity. This can be a combination of something the user knows (such as a password), something the user has (such as a token or a smart card), or something the user is (such as biometric data).
Pros:
It adds an extra layer of security to the authentication process.
It is more difficult to bypass or circumvent than password-based authentication.
It can prevent unauthorized access even if the password is compromised.
Cons:
It can be more difficult and expensive to implement and maintain.
It can be inconvenient for users to carry and use the additional authentication factor.
Some 2FA methods (such as SMS-based authentication) can be vulnerable to attacks.
Public key infrastructure (PKI) authentication: This method uses digital certificates and a public key infrastructure to authenticate users. Each user has a public-private key pair, and a certificate authority (CA) issues digital certificates that link the user's identity to their public key.
Pros:
It provides strong authentication and encryption capabilities.
It can be used in a wide range of applications, such as secure email, web browsing, and e-commerce.
It can be used for non-repudiation (i.e., to prove that a user sent a message or made a transaction).
Cons:
It can be complex to set up and manage.
It requires a trusted third party (the CA) to issue and manage the digital certificates.
It can be vulnerable to attacks if the private key is compromised.
Overall, each authentication method has its own strengths and weaknesses, and the appropriate method depends on the level of security required, the usability needs, and the specific context of the system or application. It is often recommended to use a combination of different authentication methods to achieve a higher level of security.
Learn more about Two-factor authentication here:https://brainly.com/question/28398310
#SPJ11
Does any body like animal jam
Answers
Answer:
Yep!
Explanation:
Complete the sentence describing computer languages.
a______level language uses zeros and ones.
the answer choice is low, middle, or high.
Answers
Answer:
A low level language uses zeros and ones.
Explanation:
Edge 2022
"A high-level programming language is a programming language that uses instructions that are close to everyday English. The lowest level language is instructions composed of zeros and ones."
The complete sentence describing computer languages is :
A low level language uses zeros and ones.
What is binary number?In digital electronics and mathematics, a binary number is defined as a number expressed in the form of base 2 numeral system. Binary number contains only two digits i.e. 1 and 0.
A high-level programming language use instructions to give command to computer.
The low level language use instructions consisting of zeros and ones.
Thus, A low level language uses zeros and ones.
Learn more about binary number.
https://brainly.com/question/8649831
#SPJ2
WHERE DO I GO TO DO THIS AND WHAT DO I WRITE?????
Write a pseudocode plan for your program.
Write the code for your program.
Test your program. Run it at least three times with different inputs.
Save your program as a .txt file for you cannot upload a .py file.
Evaluate your project using this rubric.
What to Submit
Submit the .txt file holding your program.
Answers
You can just look up "python ide online" on google and paste this code:
n = -1
count = 0
while n < 0:
n = int(input("We're checking to see if a number is prime or not! Enter a positive number: "))
if n % 2 == 0:
if n == 2:
print("{} is a prime number".format(n))
else:
print("{} is not a prime number".format(n))
else:
for x in range(n, 1, -1):
if n % x == 0:
count += 1
if count > 1 or n == 1:
print("{} is not a prime number".format(n))
else:
print("{} is a prime number".format(n))
I've written some code that checks to see if a number entered by the user is a prime number or not.
Sorry, but I'm not too good with pseudocode plans and all that. I hope this helps.
Answer:
import math
print("Let's solve ax² + bx + c = 0")
a = int(float(input('Enter a value for a: ')))
b = int(float(input('Enter a value for b: ')))
c = int(float(input('Enter a value for c: ')))
D = b*b-4*a*c
if (D<0):
print("Sorry, this equation has no solutions.")
elif (a == 0):
if (b == 0):
if (c == 0):
print("Every value of x is a solution")
else:
print("Sorry, this equation has no solutions")
else:
x = -c/b
print("The one solution is x={:.3g}".format(x))
elif (D==0):
x = (-b + math.sqrt(D)) / (2*a)
print("The one solution is x={:.3g}".format(x))
else:
x1 = (-b + math.sqrt(D)) / (2*a)
x2 = (-b - math.sqrt(D)) / (2*a)
print("This equation has two solutions: x={:.3g} or x={:.3g}".format(x1, x2))
Explanation:
Above is another little program to use the quadratic formula.
Main function of Ubuntu
Answers
Answer:
Ubuntu includes thousands of pieces of software, starting with the Linux kernel version 5.4 and GNOME 3.28, and covering every standard desktop application from word processing and spreadsheet applications to internet access applications, web server software, email software, programming languages and tools
Explanation:
Answer:
Explanation:
It is a free OS
Why is it important to take precautions such as turning off a computer and discharging electricity before
opening the case on a computer?
O The case requires battery operation only when being opened.
O The case is locked until the computer is unplugged.
/
O Memory will be lost if the case is removed while connected to electricity.
O The internal components are static sensitive.
Answers
The reason why is it important to take precautions such as turning off a computer and discharging electricity before opening the case on a computer is: "The internal components are static sensitive." (Option D)
What is the rationale for the above response?It is important to take precautions such as turning off a computer and discharging electricity before opening the case on a computer because the internal components of a computer are sensitive to static electricity.
Static electricity can build up in the body or in clothing and can cause a discharge of electricity when in contact with sensitive electronic components. This discharge can damage or destroy the components, leading to the malfunctioning or failure of the computer.
By turning off the computer and discharging any residual electricity, the risk of a static discharge is minimized.
Learn more about static sensitive at:
https://brainly.com/question/18354578
#SPJ1
What is an "Expert System"?
If you can’t answer pls leave It
Answers
Answer:
program that use artifical intelligents
Explanation:
Expert system, a computer program that uses artificial-intelligence methods to solve problems within a specialized domain that ordinarily requires human expertise.
A filename ________ is a short sequence of characters that appear at the end of a filename preceded by a period.
Answers
A filename extension is a short sequence of characters that appear at the end of a filename preceded by a period. This extension is used to identify the file type and the program needed to open the file.
Extensions help users to easily identify and access files of a specific type. For example, a file with a . docx extension is a Word document, while a file with a . jpg extension is an image file. The extension also allows operating systems to associate files with the appropriate programs, making it easy to open files with just a double-click.
Extensions play an important role in file management and organization. They provide valuable information about the type of file and how it should be opened, making it easy for users to quickly locate and access the files they need.
To know more about filename extension visit:
https://brainly.com/question/21419607
#SPJ11
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
Drag each label to the correct location on the image.
Match the different types of mounting techniques with their definitions.
uses triangular pockets
to hold the corners of a
photograph to the mount
board
uses wet glue to stick
the print to a mount
board
uses a heat-activated
adhesive to permanently
stick the photograph to
a rigid backing board
uses different patterns
of tape to create hinges,
which attach the print to
a mount board
dry mount
photo corners
Answers
Answer: uses a heat activated.... the answer is dry mount
Use triangular pockets to hold the corners....the answer is photo corners
Use different patterns of tape.....hinge mount
Uses wet glue to stick the print....wet mount
Explanation: I got this right on a post test
The matchup of the mounting techniques are:
uses a heat activated- dry mountUse triangular pockets to hold the corners- photo corners Use different patterns of tape-h/in/ge mountUses wet glue to stick the print- wet mountWhat is the mounting techniquesMounting could be a handle by which a computer's working framework makes records and registries on a capacity gadget (such as difficult drive, CD-ROM, or organize share) accessible for clients to get to through the computer's record system.
There are diverse sorts of strategies in mounting craftsmanship work, exhibition hall mounting and dry mounting. Gallery mounting is authentic and reversible and dry mounting is authentic (in most cases) and non-reversible.
Read more about mounting techniques here:
https://brainly.com/question/20258766
Which of the following type of servers would be ideal candidates to install and utilize Windows 2016 Nano Server? (Choose all that apply.)
O Hyper-V server
O DNS server
O Web serverO All above
Answers
All of the options are correct.
Windows 2016 Nano Server is a lightweight version of the Windows Server operating system that is designed to be used in a variety of scenarios, including as a virtualization host, a file server, or a domain controller. It is optimized for use in cloud environments and can be deployed remotely using standard tools such as Windows PowerShell or Remote Server Administration Tools (RSAT).
Based on the options you provided, all of the following types of servers would be ideal candidates for installing and utilizing Windows 2016 Nano Server:
Hyper-V server: Nano Server can be used as a virtualization host, running Hyper-V to host virtual machines.DNS server: Nano Server can be used as a domain name system (DNS) server, providing name resolution services to clients on the network.Web server: Nano Server can be used as a web server, hosting websites and web applications.Therefore, the correct answer is "All above."
What is the value of x after the following
int x = 5;
x++;
x++;
x+=x++;
A)14
B)10
C)13
D)15
Answers
Answer:
Option D: 15 is the right answer
Explanation:
Initially, the value of x is 5
Note- x++ is a post-increment operator which means the value is first used in the expression and then increment.
After executing the x++, the value of x is 6
similarly again executing the next line and right now the value of x is 7
At last the value of x is 15.
For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


4.3.7: Positive, Zero, or Negative - Codehs.
Question/Test Case:
Write a program that asks the user for a number. Report whether that number is positive, zero, or negative.
Problem/Error:
File "main.py", line 5
if number < 0:
^
SyntaxError: invalid syntax
My code:
print("Enter a number to see if it's positive, negative, or zero!")
number = int(input("Enter a number: ")
if number < 0:
print(str(number) + "That number is negative!")
elif number > 0:
print(str(number) + "That number is positive!")
else number == 0:
print(str(number) + "That number is zero!")
Answers
The program is an illustration of the if conditional statement.
Conditional statements are statements whose execution is dependent on its truth value.
The program in Python where comments are used to explain each line is as follows:
#This gets input for the number
number = int(input("Enter a number: "))
#This checks for negative numbers
if number < 0:
print("Negative!")
#This checks for positive numbers
elif number > 0:
print("Positive!")
#Otherwise, the number is zero
else:
print("Zero!")
Read more about similar programs at:
https://brainly.com/question/20475581
all of the following are critically important components to obtain good seo results except for _____________.
Answers
All of the following are critically important components to obtain good SEO results except for poor content.
What is SEO? SEO stands for "Search Engine Optimization," which is the process of optimizing a website for search engines. The purpose of this method is to increase the visibility of the website in search engine results pages (SERP). It aids in attracting organic (unpaid) traffic to your website. It's critical to remember that SEO isn't just about search engines. It's also about enhancing your website's user experience, as well as the perception of search engines.
Poor content is not a critically important component to obtain good SEO results. It is instead an essential factor that can adversely affect your SEO performance. Creating high-quality, engaging, and informative content is critical for successful SEO. Poor quality content can lead to a higher bounce rate, low engagement rate, and a poor user experience, all of which can negatively impact your website's SEO.
To know more about SEO visit:
brainly.com/question/31657595
#SPJ11
Your development team is working on a game, and one of your colleagues, Amanda, comes up with a brilliant new feature. However, your team project manager says there isn't enough time to implement Amanda's idea. What are some ways that you could incorporate this feature while still following your project manager's instructions? (In other words, what are some ways that you have seen video games add in new features after the original game has been released?)
Answers
Answer:
updates or patchs
Explanation:
Describe Barry Boehm's conclusions about Agile and plan-driven methods from the Boehm 2002 reading.
____
Answers
Barry Boehm's 2002 report examines the conflict between plan-driven methods and agile methods in software development. Boehm claims that both approaches have advantages and disadvantages that are dependent on the type of project being undertaken.
Hybrid model: A hybrid model that combines aspects of both agile and plan-driven models, tailored to fit the specific requirements of the project. Boehm acknowledges that this approach is the most flexible and is appropriate for most projects.
Agile methods for early phases: Utilize agile methods in the project's early phases to ensure a shared understanding of stakeholder needs and better alignment with business goals.
Rapid application development: Utilize agile methods to rapidly prototype a software solution in a plan-driven framework. Boehm notes that this approach is suitable for projects with high process uncertainty and tight time constraints.
Boehm concludes that agile methods and plan-driven methods should be used together. The advantages and disadvantages of each approach will be balanced by employing hybrid models that are tailored to fit the specific requirements of the project. This hybrid approach maximizes the benefits of both models and results in a more efficient and effective software development process.
To know more about models visit:
https://brainly.com/question/32196451
#SPJ11
what is the largest decimal expression that can be stored in a byte
Answers
Get the radius as an input from the user. notice that we need the constant pi, which is roughly 3.14. conveniently, the math module has pi defined for us as math.pi. use it to compute the area.
Answers
The Python code snippet prompts the user for the radius of a circle, utilizes the constant pi from the math module, and calculates the area of the circle using the formula pi * radius².
A Python code snippet that prompts the user for the radius, then calculates and displays the area of a circle using the given radius and the constant pi is:
import math
# Prompt the user for the radius
radius = float(input("Enter the radius of the circle: "))
# Calculate the area of the circle
area = math.pi * (radius ** 2)
# Display the result
print("The area of the circle is:", area)
In this code, we import the math module, which provides the value of pi (math.pi). We then use the input() function to get the radius from the user as a string, convert it to a floating-point number using float(), and store it in the radius variable.
Next, we calculate the area of the circle using the formula pi * radius² and store the result in the area variable.
Finally, we use the print() function to display the computed area to the user.
To learn more about radius: https://brainly.com/question/27696929
#SPJ11