How to fix "the action cannot be completed because the file is open in another program"?
Answers
If you receive the error message "The action cannot be completed because the file is open in another program," it means that the file you are trying to modify or delete is currently in use by another program. Here are some steps you can take to resolve this issue:
1. Close the program that is using the file: The first step is to determine which program is using the file and close it. If you are unsure which program is using the file, restart your computer, and then try to modify or delete the file.
2. Use Task Manager to end the program: If you are unable to determine which program is using the file, you can use Task Manager to end the program. To do this, press Ctrl + Shift + Esc to open Task Manager, then find the program in the list of running processes, right-click on it, and select End Task.
3. Rename the file: If you are unable to modify or delete the file, you can try renaming it. Right-click on the file, select Rename, and change the file name. This should allow you to modify or delete the file.
4. Use a file unlocker tool: If the above steps do not work, you can use a file unlocker tool such as Unlocker or FileASSASSIN to unlock the file. These tools can help you to identify which program is using the file and allow you to unlock and delete it.
If none of these steps work, it may be that the file is being used by a system process, in which case you may need to restart your computer in safe mode to modify or delete the file.
Related Questions
Can't find the right year for this. (Attachment)

Answers
Where is a Pivot Table inserted?
a. Next to the last column of data in your worksheet
b. Below the last row of data in your worksheet
c. It depends on whether you select to insert the Pivot Table in the current worksheet or a new worksheet
d. Above the first row of data in your worksheet
Answers
The Create PivotTable dialog box will prompt you to create a Pivot Table on an Existing Worksheet if you insert one on a data-filled worksheet. One of the options in the Create PivotTable dialog box is this one.
Utilized in spreadsheet applications like Excel, OpenOffice.org Calc, and Ggle Sheets is a data summarization tool called a pivot table. Sorting, counting, and totaling data in a table are its primary uses. In order to create a report, you can summarize the data in a variety of ways using a pivot table.
The dialog box for "Create PivotTable":
In Excel, a new pivot table can be created using the dialog box labeled "Create PivotTable."
Learn more about PivotTable at
brainly.com/question/18410166
#SPJ4
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
How to fix "an error occurred inside the server which prevented it from fulfilling the request"?
Answers
If you are experiencing an error that says "an error occurred inside the server which prevented it from fulfilling the request". It is important to take the necessary steps to troubleshoot the issue.
Troubleshooting 'An Error Occurred Inside the Server Which Prevented It From Fulfilling the RequestCheck the server logs for errors.Check the web server configuration for any errors.Check the application code for any errors.Check the database for any errors.Check the network for any errors.Check the server resources for any errors.Check the server environment for any errors.Restart the server to see if the issue is resolved.Contact the server administrator for further assistance.If the problem still persists, contact the server administrator for further assistance. Taking the necessary steps to troubleshoot the issue can help to ensure that the server is running optimally, and that requests are fulfilled without any errors.
Learn more about programming: https://brainly.com/question/26497128
#SPJ4
This tool lets you insert text anywhere in your document. O Cut О сору O Drag O Paste
Answers
Answer:
Drag or paste (im not 100% sure tho)
Explanation:
Which of the following best describes a benefit of a distributed network over a centralized network?
Group of answer choices
They are cheap to set up because they require less infrastructure than centralized networks
All messages have to travel through the same part of the network, allowing for easier monitoring
When one part of the network fails, messages can still get through
Centralized networks provide easier communication routes
Answers
The best description of a benefit of a distributed network over a centralized network is: When one part of the network fails, messages can still get through. Distributed networks offer increased reliability due to their lack of dependency on a single central point.
This allows for better fault tolerance, ensuring that communication can continue even if certain parts of the network face issues. In contrast, centralized networks have a single point of failure, which can lead to a complete shutdown of the network when that point is compromised.
A benefit of a distributed network over a centralized network is that they are generally cheaper to set up as they require less infrastructure. This is because the network is spread out over multiple nodes rather than relying on a central hub. Additionally, if one part of the network fails, messages can still get through as there are multiple paths for data to travel. This makes distributed networks more reliable and resilient than centralized networks. In a centralized network, all messages have to travel through the same part of the network, which can make it easier to monitor but also makes it vulnerable to congestion and potential failures.
Overall, the decentralized nature of distributed networks allows for greater flexibility and adaptability, making them a more effective solution for many organizations.
Learn more about network here:
https://brainly.com/question/15332165
#SPJ11
Which document would be best created using Word Online?ANIMATIONGRAPHRESUMESPREADSHEET
Answers
Answer:
resume
Explanation:
PLZ HELP What is the problem with this program?
name = "Jenny"
name = input("What is your name?")
A.
the variable name has to begin with a capital letter
B.
input should be output
C.
the first line should be omitted because the second line defines the variable
D.
the variable needs to begin with a number to distinguish it from other variables
Answers
Answer:
B
Explanation:
the answer is B imput should be output
Answer: I think the answer is (C)
I'm doing the exam rn and that what i think
Explanation:
list any four e-commerce website
Answers
Answer:
Amazon. Founded in the US in 1994, Amazon started as an online bookstore that later diversified to products including media, electronics, apparel, furniture, food, toys, and jewelry.
eBay. ...
Walmart. ...
Etsy. ...
Home Depot. ...
Target. ...
Best Buy. ...
Wayfair.
Answer:
I'm sorry is this a question?
how can i help?
Explanation:
Who should NOT apply for financial aid?
Students who will attend college part-time
Students whose annual family income is over $100,000
Students who will attend community college
All students should apply for financial aid
Answers
Answer: wealthy students should, not a must, apply for it. Not every student.
to center data in a cell, click the ____ button on the ribbon.
Answers
To center data in a cell, click the center button on the ribbon.
Data in a cell can be aligned either horizontally or vertically .
For the horizontal alignments, we have
against the left border, against the right border, and in the centre.For the vertical alignments, we have
against the top border, against the bottom border, and in the middle.To center data, the following steps should be followed.
1.Click the cell where you want to center the data.
2. Click "Home," then the small arrow in the bottom corner of the "Alignment" area of the ribbon.
3.Click the drop-down box next to "Horizontal" and choose "Center." Do also for the "Vertical.
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
the term ""____"" is used to label any condition in which one or more optional relationships exist.
Answers
Any situation in which there are one or more optional relationships is referred to as optionality.
What kind of connection occurs when two things are linked?When an association is kept within just one entity, there is a unary relationship. When two entities are connected, a binary connection exists. When three things are linked, there is a ternary relationship.
What is the name of the relationship when an association is kept within a single entity?Relationship with a unary structure: Association is preserved inside a single unit. There is a connection between instances of the same entity set in a recursive relationship. Two entities are linked in a binary connection. In a ternary relationship, three things are linked.
To know more about linked visit:-
https://brainly.com/question/14057804
#SPJ4
Which of the following units of measurement is equal to the font size for the current font?a. a pixelb. a pointc. an emd. a percentage
Answers
The unit of measurement that is equal to the font size for the current font depends on the type of unit that is being used for the font size. If the font size is being measured in pixels, then the unit of measurement that is equal to the font size for the current font is a pixel.
Similarly, if the font size is being measured in points, then the unit of measurement that is equal to the font size for the current font is a point. If the font size is being measured in ems, then the unit of measurement that is equal to the font size for the current font is an em. Finally, if the font size is being measured in percentages, then the unit of measurement that is equal to the font size for the current font is a percentage.
Therefore, the answer to the question "Which of the following units of measurement is equal to the font size for the current font?" can vary depending on the type of unit that is being used for the font size.
Know more about Units of Measurements here:
https://brainly.com/question/14026238
#SPJ11
Which of the following configurations offers the most secure ICS/Enterprise network environment?
Question 2 options:
Segregated networks
Defense-in-Depth networks
Segmented networks
Firewalled networks
Answers
Out of the following configurations, the Defense-in-Depth network configuration offers the most secure ICS/Enterprise network environment. So second option is the correct answer.
The Defense-in-Depth network configuration is the most secure network configuration for an ICS/Enterprise network environment. Defense-in-Depth is a type of cybersecurity architecture that employs multiple layers of defense mechanisms.
Each layer provides an added level of protection to the network infrastructure, making it more challenging for hackers to penetrate the system.
The Defense-in-Depth architecture employs the following three key elements:
Prevention: To keep the attacker from gaining entry to the system.Detection: If an attacker breaches the system, it must be detected as quickly as possible.Mitigation: Take steps to lessen the effects of a successful attack by the attacker.The Defense-in-Depth architecture requires the implementation of several security layers, such as firewalls, intrusion detection systems, and security policies. The organization's security is increased by employing several layers of security, making it challenging for attackers to get access to the network.
So, the correct answer is second option: Defense-in-Depth networks.
To learn more about network: https://brainly.com/question/8118353
#SPJ11
*
Which of the following variable names are invalid?
123LookAtMe
Look_at_me
LookAtMe123
All of these are valid
Answers
Answer:
I think they're all valid but the validility depends on the website your using the usernames on.
Explanation:
True/False : the oem version of windows 10 can only be installed on a new pc for resale.
Answers
The OEM version of Windows 10 can be installed on a new PC for resale, as well as on an existing PC for system builders who assemble their own PCs for personal use. The answer is False.
However, it cannot be transferred to another PC once it is installed. The OEM version is designed for manufacturers and system builders who purchase licenses in bulk, and it typically comes with fewer features and less support than the retail version of Windows 10. The license key for the OEM version is also tied to the hardware of the computer it is installed on, so it cannot be transferred to a different PC.
It is important to note that using the OEM version of Windows 10 for personal use may not be in compliance with Microsoft's licensing agreement, and could potentially result in legal consequences. It is recommended to purchase the retail version of Windows 10 for personal use, as it provides more flexibility and support.
To know more about Windows 10 visit:
https://brainly.com/question/30754735
#SPJ11
What is a file path?
Answers
Answer:
Similarly, in the computer world, a path defines the location of a file or folder in a computer's file system. Paths are also called "directory paths" because they often include one or more directories that describe the path to the file or folder. A path can either be relative or absolute.
(Brainliest please)
Briefly summarize the policy issue of how cotton subsidies in the U.S. have historically influenced cotton production in developing countries, particularly the "Cotton 4" countries. In your response, address how these subsidies have influenced exports by "Cotton 4" countries based on the trade distortions we have learned about in class and based on your reading of the case study.
2. Briefly explain the 2014 WTO Dispute Settlement of the Cotton case between the United States and Brazil, and the changes that resulted from it.
Answers
Cotton subsidies in the U.S. have historically influenced cotton production in developing countries, particularly the "Cotton 4" countries. These subsidies have created trade distortions that impact the exports of the "Cotton 4" countries.
The policy issue of cotton subsidies in the U.S. has had a significant impact on cotton production in developing countries, specifically the "Cotton 4" countries (Benin, Burkina Faso, Chad, and Mali). The subsidies provided to U.S. cotton farmers have resulted in overproduction and lower global prices for cotton. This has made it difficult for cotton farmers in the "Cotton 4" countries to compete in the global market.
The subsidies in the U.S. create trade distortions by artificially lowering the price of cotton. This leads to an increase in U.S. cotton exports, as their cotton becomes more competitive due to the lower prices. However, the lower global cotton prices negatively affect the "Cotton 4" countries, as their cotton exports become less competitive in the global market.
In 2014, a dispute settlement was reached at the World Trade Organization (WTO) between the United States and Brazil regarding the cotton case. The United States was found to be providing trade-distorting subsidies to its cotton farmers, which violated WTO rules. As a result, the United States agreed to make changes to its cotton subsidy program.
The changes resulting from the WTO dispute settlement included reducing direct payments to cotton farmers, implementing a new insurance program, and increasing funding for market development activities. These changes aimed to reduce the trade distortions caused by the subsidies and create a more level playing field for cotton producers worldwide.
Overall, the policy issue of cotton subsidies in the U.S. has had a significant impact on cotton production in developing countries, particularly the "Cotton 4" countries. The WTO dispute settlement in 2014 brought about changes to the U.S. cotton subsidy program, aiming to address the trade distortions caused by these subsidies.
To know more about policy refer to:
https://brainly.com/question/26055567
#SPJ11
You compared each letter in the correct word to the letter guessed. Assume the correct word is "cloud." Finish the code to compare the guessed letter to the "u" in "cloud."
if guess == correct[4]
if guess == correct{4}
if guess == correct[3]
if guess == correct{3}
Answers
Answer:
if guess == correct[3]:
Explanation:
Its was correct
You compared each letter in the correct word to the letter guessed the correct word is "cloud." Finish the code to compare the guessed letter to the "u" in "cloud." is option c. it is if guess == correct[3].
What is code ?Coding method is the use of the programming language to get the laptop to act as desired. Each line of the code is a hard and fast of commands for the laptop.
The correct word is "cloud." Finish the code to compare the guessed letter to the "u" in "cloud" is if guess == correct.
Read more about the code:
https://brainly.com/question/19344465
#SPJ2
Which programming languages are the best choices for desktop applications? Select 3 options.
Java
C
Python
Visual Basic
HTML
Answers
We are currently living in the __________, an era characterized by the production, distribution, and control of information as the primary economic driver.
A. Cloud Age
B. Information Age
C. Nerd Age
D. Computer Age
E. Tech Age
Answers
We are currently living in the Information Age, an era characterized by the production, distribution, and control of information as the primary economic driver.
The widespread usage of digital technology, such as computers, the internet, and mobile devices, is what is known as the information age, sometimes known as the digital age or the computer age. The advent of the information economy, the expansion of e-commerce, and the creation of new channels for social contact and communication are just a few examples of how the Information Age has significantly altered the way we work and live.
Learn more about Digital Age here:
https://brainly.com/question/30917682
#SPJ11
Where are methods listed in a UML class diagram showing three parts?
in the top third of the diagram
in the middle third of the diagram
in the bottom third of the diagram
anywhere in the diagram a lowercase m is shown
Answers
Answer:
the bottom third
Explanation:
Check out the exampe below.
swim() would be an example of a method.

Write any 5 activities that help to remove bad events from the society?
Answers
Answer:
1. Awareness program
2. Education
3. women empowerment
Find the maximum number of paths between any two vertices of a
tree.
Answers
The maximum number of paths between any two vertices of a tree can be determined using the formula `n(n-1)/2A tree is a connected graph having no encryption cycles.
In a tree with `n` vertices, the maximum number of paths between any two vertices can be determined using the formula `n(n-1)/2`. This formula is derived as follows: For a given vertex, there are `n-1` vertices that it can be connected to directly (excluding itself).
Therefore, the maximum number of paths from this vertex is `n-1`.Similarly, for each of the `n-1` vertices that are connected to the first vertex, there are `n-2` vertices that they can be connected to (excluding themselves and the first vertex). Therefore, the maximum number of paths from each of these vertices is `n-2`.Continuing this pattern for all `n-1` vertices, we get the following sum:`(n-1) + (n-2) + (n-2) + ... + 1 = (n-1) + ((n-2) + (n-3) + ... + 1) = (n-1) + ((n-2)(n-1)/2) = n(n-1)/2`Therefore, the maximum number of paths between any two vertices of a tree with `n` vertices is `n(n-1)/2`.
To know more about encryption visit:
https://brainly.com/question/30225557
#SPJ11
which line of code will allow you to only load the localtime() method into active memory

Answers
Answer:
from time import localtime
Explanation:
have a lovely day :)
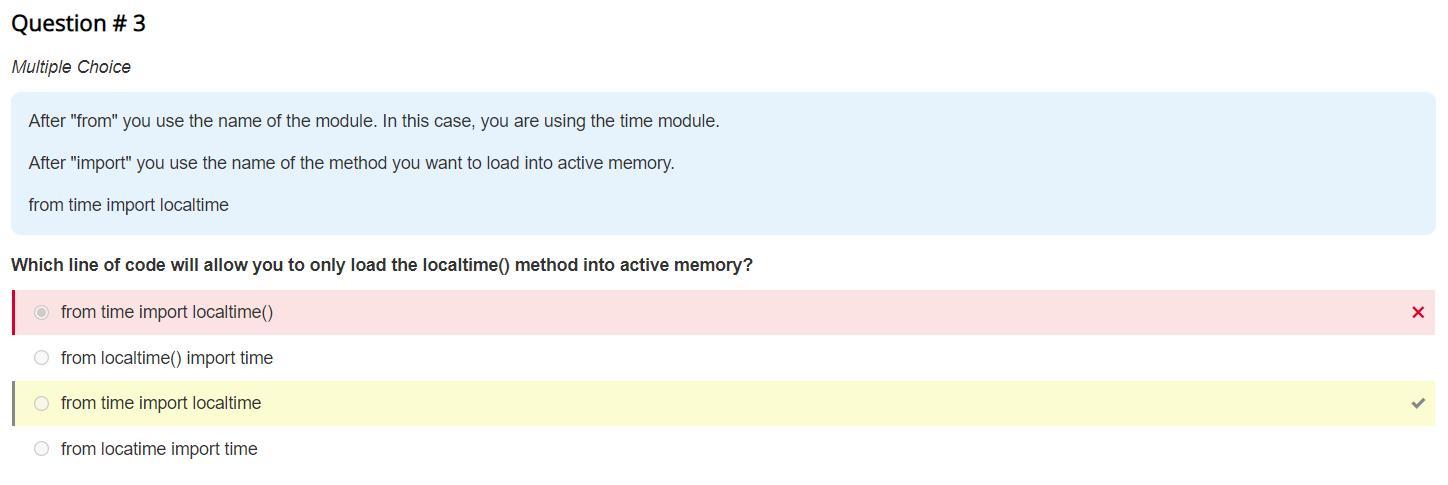
The line of code that will allow you to only load the localtime method into active memory is time.
The localtime function is simply known to be time in seconds as long as Epoch is targeted by timer into a broken-down time.
It is mostly written in local time. The function is known to be of timezone and any seasonal time adjustments. Local timezone information is used as though localtime() calls tzset().LocalTime cannot have a muted date-time object that shows a time, often viewed as hour-minute-second. Time is shown in nanosecond precision.
Learn more from
https://brainly.com/question/19639119
What are Apps?
How do we interact with them?
Answers
Answer:
Sliding elements in list format.
Cards.
Images.
Buttons.
Overflow screens.
Multiple selection app interactions.
Text input fields.Explanation:
Non-delivered goods, counterfeit products, fraudulent payments are common type of cyber crime these
days.
a. What are such types of cyber crimes collectively called?
b. What are counterfeit products?
c. What measures can you take to stop fraudulent payments? Write any two measures.
Answers
Answer:
a. Internet auction fraud
b. Counterfeit products are products made and/or sold under the brand name of a product of a higher quality
c. 1) Monitor business transactions
2) Use an Address Verification System AVS
Explanation:
a. Such types of cyber crimes are collectively called Internet auction fraud
Internet or online auction fraud is a form of fraud that involves the act of providing misleading information about goods paced on advert for sale on an online auction site, including the sale of counterfeit goods, sale of goods of poor quality, receiving a different item from what was ordered, artificial bidding to increase price, omission of important information about a product, delivering an item that looks different from what was displayed on the website and the non-delivery of an item already to the buyer.
A seller can be a victim of the internet auction fraud when a buyer does not pay for goods an/or services received, request for delivery before payment, the buyer pays with a stolen credit card, the buyer uses a fake escrow account such that the money returns to the buyer after receiving the goods
b. Counterfeit products or goods are products that are being manufactured and marketed, without formal authorization, under the name of a popular and recognized but are usually of lesser quality than the product they try to imitate
c. Measures that can be taken to stop fraudulent payments are;
1) Monitor transactions to to check for red flags, including disparity in shipping and billing information
Monitor transactions from customer that use free or anonymous emails services which can easily be opened and closed without payment or proper documentation
2) Make use of Address Verification System to authenticate the billing address on a payment, and the address on the credit card.
Which layer is used for reliable communication between end nodes over the network and provides mechanisms for establishing, maintaining, and terminating virtual circuits as well as controlling the flow of information?
Answers
The layer used for reliable communication between end nodes over the network and providing mechanisms for establishing controlling the flow of information, is the Transport Layer.
The Transport Layer is the fourth layer in the OSI (Open Systems Interconnection) model and is responsible for end-to-end communication between host devices. Its primary function is to ensure the reliable and orderly delivery of data from the source to the destination. This layer establishes connections, breaks data into segments or packets, and reassembles them at the receiving end. It also handles error detection and correction, flow control, and congestion control to optimize the transmission of data.
Some common protocols operating at the Transport Layer include Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP provides reliable and connection-oriented communication, while UDP offers unreliable and connectionless communication.
In summary, the Transport Layer plays a crucial role in ensuring the smooth and reliable transfer of data between end nodes over the network by establishing virtual circuits, managing data segmentation and reassembly, and controlling the flow of information.
To know more about nodes, click here:
https://brainly.com/question/31324954
#SPJ11
computer system allows three users to access the central computer simultaneously. Agents who attempt to use the system when it is full are denied access; no waiting is allowed. of 28 calls per hour. The service rate per line is 18 calls per hour. (a) What is the probability that 0,1,2, and 3 access lines will be in use? (Round your answers to four decimal places.) P(0)= P(1)= P(2)= P(3)= (b) What is the probability that an agent will be denied access to the system? (Round your answers to four decimal places.) p k
= (c) What is the average number of access lines in use? (Round your answers to two decimal places.) system have?
Answers
In the given computer system scenario, there are three access lines available for users to access the central computer simultaneously. The arrival rate of calls is 28 per hour, and the service rate per line is 18 calls per hour.
We are required to calculate the probabilities of different numbers of access lines being in use, the probability of an agent being denied access, and the average number of access lines in use.
(a) To calculate the probabilities of different numbers of access lines being in use, we can use the formula for the probability of having k lines in use in a system with three lines, given by P(k) = (1 - p) * p^(k-1), where p is the utilization factor. The utilization factor can be calculated as p = λ / μ, where λ is the arrival rate and μ is the service rate per line.
Using the given values, we can calculate the probabilities as follows:
P(0) = (1 - p) * p^2
P(1) = (1 - p) * p^0
P(2) = (1 - p) * p^1
P(3) = p^3
(b) The probability of an agent being denied access is equal to the probability of all three access lines being in use, which is P(3) = p^3.
(c) The average number of access lines in use can be calculated using the formula for the average number of customers in a system, given by L = λ / (μ - λ). In this case, since there are three lines available, the average number of access lines in use would be L / 3.
By plugging in the values and calculating the probabilities and average number of access lines, we can obtain specific numerical answers.
Learn more about arrival rate here :
https://brainly.com/question/29099684
#SPJ11