Show that the TM F below is a reduction from Atm to EQTM F ="On input (M,w) where M is a TM and w is a string: 1. Construct a TM Mų as follows: M1 ="On input x 1. accept 2. Construct a TM M2 as follows: M1 ="On input x 1. Run M on input w 2. If M accepts w, accept. If M rejects w, reject." 3. Output (M1, M2)"
Answers
To show that the TM F below is a reduction from Atm to EQTM, we must prove that F is a computable function, that F transforms its input from Atm into EQTM, and that F preserves its output from Atm to EQTM.
The definition of Atm is that it accepts (M,w) as input and decides whether or not M accepts w. EQTM is defined as (M1,M2) as input and decides whether or not L(M1)=L(M2). If we can show a polynomial-time reduction F from Atm to EQTM, we can prove that EQTM is at least as difficult as Atm, and it is also a Turing-recognizable problem. Here's a reduction from Atm to EQTM:For a given input (M,w), construct M1 to accept any string, then construct M2 to run M on w. If M accepts w, accept. If M rejects w, reject. Output the pair (M1, M2).
Thus, we can conclude that the TM F below is a reduction from Atm to EQTM.
To know more about Turing-recognizable visit:
https://brainly.com/question/32223971
#SPJ11
Related Questions
A filename ________ is a short sequence of characters that appear at the end of a filename preceded by a period.
Answers
A filename extension is a short sequence of characters that appear at the end of a filename preceded by a period. This extension is used to identify the file type and the program needed to open the file.
Extensions help users to easily identify and access files of a specific type. For example, a file with a . docx extension is a Word document, while a file with a . jpg extension is an image file. The extension also allows operating systems to associate files with the appropriate programs, making it easy to open files with just a double-click.
Extensions play an important role in file management and organization. They provide valuable information about the type of file and how it should be opened, making it easy for users to quickly locate and access the files they need.
To know more about filename extension visit:
https://brainly.com/question/21419607
#SPJ11
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
What is the value of number after the following statements execute?
int number; number 18 4+ 2
a) 6
b) 3
c) 4
d) 6.5
e) the statement is invalid
Answers
The correct option in this case would be "e) the statement is invalid."
The value of the number after the given statements execute can be determined by evaluating the mathematical expression. Based on the given statements, the expression "4 + 2" is added to the value of the number, which is initially undefined.
However, there is an error in the syntax of the statement "number 18," as it seems to be incomplete or incorrect. Therefore, the statement itself is invalid.
In programming, the correct syntax to assign a value to a variable would be to use the assignment operator "=", such as "number = 18." Without the assignment operator, the statement "number 18" is not a valid assignment or mathematical operation.
Since the statement is invalid, the value of the number cannot be determined from the given code. The correct option in this case would be "e) the statement is invalid."
Learn more about syntax here:
https://brainly.com/question/31605310
#SPJ11
In python
BINGO! - Create a piece of code that meets the following requirements:
Asks the user to enter their name.
The code should then ask the user to enter their lucky number (it should tell them it must be between 1 - 10).
The code should then randomly generate and output a number between 1 - 10. If the number is a match, it should display the message “BINGO!”. However if it does not match, the code should continue until the two numbers match.
At the end of the code it should display how many numbers it took until the user got a match.
Answers
Using the knowledge in computational language in python it is possible to write a code that Create a piece of code that meets the following requirements: Asks the user to enter their name.
Writting the code:import random
name = input("What is your name? ")
print("Good Luck ! ", name)
words = ['rainbow', 'computer', 'science', 'programming',
'python', 'mathematics', 'player', 'condition',
'reverse', 'water', 'board', 'geeks']
word = random.choice(words)
print("Guess the characters")
guesses = ''
turns = 12
while turns > 0:
failed = 0
for char in word:
if char in guesses:
print(char, end=" ")
else:
print("_")
print(char, end=" ")
failed += 1
if failed == 0:
print("You Win")
print("The word is: ", word)
break
print()
guess = input("guess a character:")
guesses += guess
if guess not in word:
turns -= 1
print("Wrong")
print("You have", + turns, 'more guesses')
if turns == 0:
print("You Loose")
See more about python at brainly.com/question/18502436
#SPJ1


What are some common security threats for our home devices and IoTs?
Answers
Answer:
Botnets. A botnet is a network that combines various systems together to remotely take control over a victim’s system and distribute malware.A denial-of-service (DoS) attack deliberately tries to cause a capacity overload in the target system by sending multiple requests. In a Man-in-the-Middle (MiTM) attack, a hacker breaches the communication channel between two individual systems in an attempt to intercept messages among them.Hackers use social engineering to manipulate people into giving up their sensitive information such as passwords and bank details.Ransomware attacks have become one of the most notorious cyber threats. In this attack, a hacker uses malware to encrypt data that may be required for business operations. An attacker will decrypt critical data only after receiving a ransom.Explanation:
you have an azure web app named webapp1. you discover that backup options are unavailable for webapp1. you need to back up webapp1. what should you do first? select only one answer. modify the platform settings of webapp1. modify the application settings of webapp1. scale up the app service plan. scale out the app service plan.
Answers
The correct option regarding what you should do first for backup options is given by:
Scale up the app service plan.
What is the meaning of scaling up an application?Vertical scaling, also called scaling up, is equivalent to adding more resources to an instance of the application that you already have.
You can do this in multiple ways, such as adding more virtual machines or changing database performance levels, allowing you to enhance the performance of the application when there is high demand and then scaling down when the demand diminishes.
In this problem, there is a demand for backup, hence you have to scale up the application, and the correct option is given by:
Scale up the app service plan.
More can be learned about applications at https://brainly.com/question/13990715
#SPJ1
the chief information officer (cio) is negotiating lease prices with several telecommunications providers. she wants a service that offers circuits that will link to various physical buildings and branches, including a connection to the physical demarcation point. for what network infrastructure will this service be used?
Answers
A number of telecom companies, the chief information officer (CIO) is negotiating leasing rates. Several computers are linked via a hub in a local area network (LAN).
What is domain?
Switches, one of the network's traffic controllers, typically operate at Layer. By utilising packet switching, they enable the connection of several devices within a LAN while reducing the collision domain. To allow private network addresses to be converted to a random external port and public IP address, both network address translation (NAT) and port address translation (PAT) must be enabled. A demilitarised zone (DMZ) is a physical or logical subnet in computer networks that divides a local area network (LAN) from other untrusted networks, typically the public internet.
To learn more about networks from given link
brainly.com/question/15088389
#SPJ4
Most of us have been using elements of Web 2.0 without even realizing it.
True
False
Answers
Answer: True?
Explanation:
I’m pretty sure I’m new to that stuff
what allows people all around the world to communicate in real-time?
Answers
In this modern world, there are various components or devices that allow people all around the world to communicate in real-time. Some of them may include mobile phones, laptops, the internet, etc.
What is real-time communication?Real-time communication (RTC) may be defined as a type of communication or interaction through the live process of telecommunication conducted over technological devices across the world. It is nearly instant with minimal latency.
Examples of real-time communications include Voice over landlines and mobile phones, VoIP, Instant messaging with the help of various mobile applications, etc.
The advantage of this strategy and development is determined by the fact that it is a cost-effective way of getting several people from different locations to attend meetings and conferences – without having to spend time or money on travel and accommodation.
Therefore, there are various components or devices that allow people all around the world to communicate in real-time. Some of them may include mobile phones, laptops, the internet, etc.
To learn more about Real-time communications, refer to the link:
https://brainly.com/question/14611916
#SPJ1
pls answer dis question when i'm not connected and i open bluestacks 5 it will be working but if i am connected it wil not work again. Pls how can i fix it
I will give u 100 pts if u answer my question
Answers
Answer:
Explanation:
idek man your guess is as good as mine
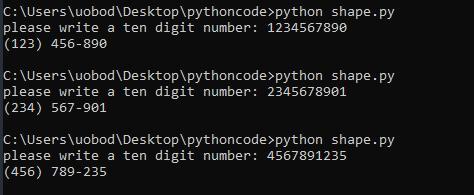
Write a program that takes a 10-digit phone number and adds a hyphen in the correct location. Using an input field for the user to enter the information. Also, use a string for instructions on how to enter the phone in the input field.
Answers
The python program will request for a ten digit number from the user and formulate a real phone number from it.
How to write a python program to form a real phone number?The program is written in python.
Therefore,
x = input("please write a ten digit number: ")
if len(x) == 10:
a = f"({x[0:3]})"
b = x[3:6]
c = x[7:]
print(a + " " + b + "-" + c)
Code explanation:The variable x is used to store the user's input.If the length of x is equals to 10, then we get the first three terms in bracket, the second three terms and the last 4 terms.Finally, we use delimiters to join the variables as required and print it out.learn more on python here: brainly.com/question/13462052
#SPJ1


How do I delete the Chrome apps folder, because I tried to remove from chrome but it won't let me
Answers
Answer:
Explanation:
1. Open your Start menu by selecting the Windows logo in the taskbar and then click the “Settings” cog icon.
2. From the pop-up menu, click “Apps.”
3.Scroll down the “Apps & Features” list to find g00gle chrome
4. Click “G00gle Chrome” and then select the “Uninstall” button.
Hope this help!
Helped by none other than the #Queen herself
Hi can you please label each part of the laptop input or output

Answers
The correct labeling of the parts of the computer is given below:
Output deviceInput deviceProcessing unitOutput unitProcessing unitInput deviceInput deviceThe Central Processing Unit which is labeled 3 and 5 respectively is neither an input or output device as it is a processing unit that also contains an Arithmetic and Logic Unit (A.L.U)
What is an Input Device?This refers to the device that is used to give commands to a computer or system.
Hence, we can see that The Central Processing Unit which is labeled 3 and 5 respectively is neither an input or output device as it is a processing unit that also contains an Arithmetic and Logic Unit (A.L.U)
Read more about input devices here:
https://brainly.com/question/24455519
#SPJ1
Thanks for asking me to ask a ques !!
Answers
Answer:
I'm not sure what this means by Hope you have a great day :)
Answer:
An important role to follow when learning is to ask questions.
Prepare a short report on what you learned about
problem-oriented policing.
/
Answers
Problem-oriented policing (POP) is a policing strategy that aims to identify and prevent the underlying causes of criminal behavior. It is a proactive approach to policing that aims to reduce crime and disorder by addressing the root causes of problems in the community.
Pop was introduced by Herman Goldstein, a law professor at the University of Wisconsin-Madison, in 1979. It gained popularity in the 1990s as an alternative to traditional policing methods, which focused on responding to crime rather than preventing it. Problem-oriented policing is based on the idea that crime is not a random occurrence but is rather the result of specific underlying problems that can be identified and addressed.
The success of problem-oriented policing depends on a number of factors, including the quality of problem analysis, the effectiveness of the strategies developed to address the underlying causes of crime, and the level of collaboration between the police department and other agencies in the community. When implemented effectively, problem-oriented policing can be an effective strategy for reducing crime and disorder in communities.
To know more about Problem-oriented policing visit:
brainly.com/question/9171028
#SPJ11
Te amount of time that a ten-year-old boy plays video games in a week is normally distributed with a mean of 10 hours and a standard deviation of 4 hours. a. Suppose 9 ten-year-old boys are randomly chosen. What is the probability that the sample mean time for playing video games per week is 8 to 12 hours
Answers
The probability that the sample mean time for playing video games per week is 8 to 12 hours for a randomly chosen group of 9 ten-year-old boys is 86.64%.
To answer this question, we need to use the central limit theorem, which states that the sample mean of a large enough sample size will be normally distributed, regardless of the distribution of the population. In this case, since we are sampling 9 boys, we can assume that the sample size is large enough for this theorem to apply.
First, we need to calculate the standard error of the mean, which is the standard deviation of the population divided by the square root of the sample size. In this case, the standard error is 4/sqrt(9) = 1.33 hours.
Next, we can use the z-score formula to calculate the probability of the sample mean falling between 8 and 12 hours.
The z-score is calculated as (sample mean - population mean) / standard error.
Plugging in the numbers, we get (8-10) / 1.33 = -1.50 and (12-10) / 1.33 = 1.50.
Using a z-table or a calculator, we can find the probability that the z-score falls between -1.50 and 1.50, which is approximately 0.8664 or 86.64%.
Learn more about Central Limit Theorem at
https://brainly.com/question/13073518
#SPJ11
Call your function from Example 1 three times with different kinds of arguments: a value, a variable, and an expression. Identify which kind of argument is which.
Answers
Answer:
Example 1:
def function(num):
print(num*2)
Example 2:
function(5)
num = 2
function(num)
function(3-1)
Explanation:
Given:
See attachment for complete question
To start with Example (1)
def function(num):
print(num*2)
Note that; the above code segment which doubles the parameter, num could have been any other code
In Example (1), the parameter is num
For example (2):
We can call the function using:
#1. A value:
function(5)
In #1, the argument is 5; a value
#2. A Variable
num = 2
function(num)
In #2, the argument is num; a variable
#3. An Expression
function(3-1)
In #3, the argument is 3-1; an expression

Fill is the inside color of a shape.
O
a. True
B. False
Answers
Answer:
True.
Explanation:
Fill describes the color of the area inside a designated shape. This statement is true.
a file that serves as a starting point for a new document
Answers
Answer:
The appropriate response is "Template".
Explanation:
A template would be a document that might open new opportunities for such a new folder. Because once you launch a framework, that's already pre-formatted sometimes in a manner. This same template will indeed presumably have such identification and phone number environment throughout the upper left, a person receiving identify location somewhat below something on the opposite side, a response body location further below, as well as a signature, identify at either the lower part.Project Stem 2.7 code practice question 2 (python)
The following lines of code represent some locations of a sea turtle that are denoted with black pins in latitudes and longitudes.
lat = [15.18, 15.11, 15.12, 15.12, 15.08, 14.95, 14.87, 14.81, 14.81, 14.75, 14.73, 14.68, 14.55]
lon = [-62.942, -62.807, -62.622, -62.499, -62.438, -62.372, -62.352, -62.318, -62.321, -62.201, -62.150, -62.154, -61.915]
The lat list indicates how far north and south the positions are, and the lon list represents how far east and west the positions are. The larger the latitude value, the further north the seal was located, and for this area of the world, the larger the longitude value, the further east the turtle is located.
Write a program to calculate the farthest in each direction that the turtle was located throughout its travels. Add four print statements to the lines of code above that output the following, where the number signs are replaced with the correct values from the correct list:
Farthest north is #
Farthest west is #
Farthest south is #
Farthest east is #
Answers
Answer:
lat = [15.18, 15.11, 15.12, 15.12, 15.08, 14.95, 14.87, 14.81, 14.81, 14.75, 14.73, 14.68, 14.55]
lon = [-62.942, -62.807, -62.622, -62.499, -62.438, -62.372, -62.352, -62.318, -62.321, -62.201, -62.150, -62.154, -61.915]
print("Farthest north is " + str(max(lat)))
print ("Farthest west is " + str(min(lon)))
print ("Farthest south is " + str(min(lat)))
print("Farthest east is " + str(max(lon)))
Explanation:
trust me bro
Farmers must meet the changing needs of our planet and the expectations of regulators, consumers, and food processors and retailers- Analyze the statement and predict the most suitable solution
Answers
Farmers must meet the changing needs of our planet and the expectations of consumers.
Why is consumer the right answer?Consumers are becoming sensitive ot how their product sare produced. For example, consumers will shun a product which was produced using child labor or using unethical practices.
Since protecting the earth is now a big issue, a front burner in with regadds to the global supply chain cycle, Farmers must pay attention to the changing needs of our planet.
Learn more about Consumers :
https://brainly.com/question/15869639
#SPJ1
I need answers ASAP
Thx

Answers
true/false. there sre several ways to describe light including: wavelength, frequency, energy, and color. convert each into the desired units
Answers
The statement "there are several ways to describe light including: wavelength, frequency, energy, and color" is true because each of these descriptions provides unique information about light.
Wavelength describes the distance between two consecutive peaks or troughs in a wave, and is typically measured in meters or nanometers. Frequency refers to the number of wave cycles that occur in a given unit of time, and is measured in units of hertz or megahertz.
Energy is a physical quantity that is proportional to the frequency of the light and is measured in units of joules or electron volts. Color is a perceptual property of light that is determined by the wavelength or frequency of the light, and is typically described using color spaces like RGB or CMYK.
Therefore, these four ways of describing light are all valid and important in various fields of science and technology.
Learn more about light https://brainly.com/question/31606560
#SPJ11
1 point
4. Part of a computer that allows
a user to put information into the
computer ?
O Output Device
O Operating System
O Input Device
O Software
Answers
Answer:
adwawdasdw
Explanation:
Answer:
I'm so sorry about the comment of that person down there
anyways I think its Number 2.
33. (03.03 LC)
Technologies are having a negative impact on businesses. (2 points)
O
True
False
I need help smh
Answers
Answer:
False
Explanation:
Technology enhances the smooth run of businesses around the world at large. take an example of your transport systems, communication systems and even to advertisment of company products/services
if you were writing an essay about the major rivers of America which illustration would be the most helpful to your reader
Answers
Answer:A map
Explanation: (╹◡╹)
how graphical representation of spreadsheet data can be helpful in business
Answers
Answer: Business graphs are visual aids used to analyze data. They can make comparing multiple sets of data much easier, as sometimes trends and relationships are easily identified on the chart or graph. They also help to show the audience the data in a way that is easy to understand and remember.
Explanation:
What is it called when a logical operation is performed between the bits of each column of the operands to produce a result bit for each column
Answers
The process that is executed when a logical operation is performed between the bits of each column of the operands to produce a result bit for each column is called bitwise operations. Bitwise operations are a type of computer operation that operates on one or more bits or binary digits.
It works on the bits of an integer or binary value. Bitwise operations are used in computer programming to manipulate binary values by performing an operation on each bit separately. Bitwise operators perform a logical operation on the bits of a variable. The logical operations are performed between the bits of each column of the operands to produce a result bit for each column.
The bitwise XOR operator produces a 1 in each column of the output if the corresponding bits of the operands differ. The NOT operator reverses the bits of the input and produces the result. Finally, the left and right shifts operations move the bits of a binary number to the left or right.
To know more about logical operation visit:
https://brainly.com/question/13382082
#SPJ11
what kinds of things would you incorporate in a training program to teach managers to better frame their messages so as to achieve their goals and objecti
Answers
A training program for managers to better frame their messages so as to achieve their goals and objectives should include clear and concise communication; active listening; emotional intelligence and conflict resolution.
1. Clear and concise communication: Managers should be taught how to effectively communicate their messages in a clear and concise manner so that they can achieve their goals and objectives.
2. Active listening: Managers should also be trained on active listening, as it is an important aspect of effective communication. This will help them better understand the needs of their employees and help them achieve their goals and objectives.
3. Emotional intelligence: Managers should also be trained on emotional intelligence so that they can effectively communicate their messages in a way that resonates with their employees. This will help them achieve their goals and objectives.
4. Conflict resolution: Managers should also be trained on conflict resolution so that they can effectively resolve any conflicts that may arise in the workplace. This will help them achieve their goals and objectives.
Overall, a training program for managers should incorporate clear and concise communication, active listening, emotional intelligence, and conflict resolution to help them better frame their messages and achieve their goals and objectives.
You can learn more about the manager training program at
https://brainly.com/question/14886708
#SPJ11
what are the components of Database system?
\( \\ \\ \)
Thanks ✨
Answers
The five major components of a database are hardware, software, data, procedure, and database access language.
hope helpez~ :)!