Solve the following 4 data structure and algorithm
questions!
1. Which of the following statements is false regarding the heap sort algorithm? Select one: Heap-sort is basically a not-stable algorithm, that is, elements with the same value may appear in a differ
Answers
The false statement regarding the heap sort algorithm is: "Heap-sort is basically a not-stable algorithm, that is, elements with the same value may appear in a different order in the sorted output."
Heap sort is indeed not a stable sorting algorithm. Stability in sorting algorithms refers to the preservation of the relative order of elements with equal values. In other words, if two elements have the same value and appear in a particular order in the input, a stable sorting algorithm will ensure that they appear in the same order in the sorted output.
However, heap sort does not guarantee stability. During the process of building the heap and performing the heapify operation, the algorithm swaps elements to maintain the heap property. This swapping can change the relative order of equal elements, resulting in a different order in the sorted output.
For example, consider an input array with two elements: (2, A) and (2, B), where the first value is the key and the second value represents the element. If the algorithm swaps these elements during the heapify operation, the relative order of A and B can be reversed in the sorted output.
While heap sort is an efficient and in-place sorting algorithm with a time complexity of O(n log n), it is not suitable for situations where stability is a requirement. In such cases, alternative stable sorting algorithms like merge sort or insertion sort should be used.
To learn more about heap sort algorithm click here: brainly.com/question/33338317
#SPJ11
Related Questions
Explain why this scenario could put an organization in jeopardy of losing some of its workforce.
Situation: The IT manager decides to add a new software application to replace an older albeit less efficient software application.
Answers
Answer:
Not educating its employees on the new software.
an expanded version of a star schema in which all of the tables are fully normalized is called a(n):
Answers
A snowflake schema is an extended form of a star schema in which all of the tables have undergone full normalization.
A snowflake schema in computing is a logical setup of tables in a multidimensional database so that the entity relationship diagram looks like a snowflake. Centralized fact tables connected to various dimensions serve as the representation of the snowflake schema. A star schema's dimension tables can be normalized by a process called "snowflaking." When all of the dimension tables are fully normalized, the resulting structure resembles a snowflake with the fact table in the center. The basic idea behind snowflaking is to normalize dimension tables by splitting out low cardinality characteristics and creating new tables.
Similar to the star schema is the snowflake schema. In contrast, dimensions are standardized into numerous linked tables in the snowflake schema.
Learn more about snowflake schema here:
https://brainly.com/question/29676088
#SPJ4
In order to improve performance, a company has decided to place copies of the same data items in multiple locations around the world. This is termed a ________ database.
Answers
In order to improve performance, a company has decided to place copies of the same data items in multiple locations around the world. This is termed a distributed database. A distributed database is a database system that stores the same data in different physical locations.
This approach offers several benefits, including improved performance, increased availability, and fault tolerance. By distributing data across multiple locations, a company can reduce network latency and improve response times for users in different geographical regions.
In summary, a distributed database is a strategy employed by companies to improve performance by placing copies of the same data items in multiple locations around the world. This approach enhances data availability, reduces latency, and ensures continuity in case of failures.
To know more about performance visit:
https://brainly.com/question/33454156
#SPJ11
Three popular types of ____ are handheld computers, PDAs, smart phones.
Answers
Answer:
portable media players, and digital cameras
Explanation:
Three popular types of mobile devices are handheld computers, PDAs, and smart phones.
What are smart phones?Smart phones can be defined as hybrid versions of mobile devices that are designed and developed to have more features, so as to enable them run different applications, functions and tasks with the aid of software applications such as web browsers, multimedia player, etc.
In Computer technology, three popular types of mobile devices are handheld computers, PDAs, and smart phones.
Read more on smart phones here: https://brainly.com/question/15867542
#SPJ2
Is this a desktop or a computer, or are they the same thing

Answers
Answer:
Same thing.
Explanation:
Drag the tiles to the correct boxes to complete the pairs.
Match the testing tools to their use.
Selenium
JMeter
load testing tool
functional testing tool
test management tool
defect-tracking tool
QTP
web browser automation tool
Quality Center
Bugzilla
Answers
Answer:
JMeter is a functional testing tool
Sora is preparing a presentation describing policies included in President Lyndon Johnson’s "Great Society” and wants to use a relevant online source.
Which source is the most relevant for the presentation?
a]-an interview with history students about the “Great Society”
b]-a photograph of Johnson making his “Great Society” speech
c]-a chart describing the conditions that led to the “Great Society”
d]-an audio recording of Johnson’s “Great Society” speech
Answers
Answer:
Option d) is correct
Explanation:
To prepare a presentation describing policies included in President Lyndon Johnson’s "Great Society”, the most relevant source that Sora should use is an audio recording of Johnson’s “Great Society” speech.
An audio recording of Johnson’s “Great Society” speech can give a more proper clarification and information regarding policies included in President Lyndon Johnson’s "Great Society”.
So,
Option d) is correct
Answer:
the answer is D
Explanation:
I just took the quiz :)
A school is conducting a survey of students to learn more about how they get to school. Students were asked how they travel to school, how long it takes them to get to school, what time they arrive at school, and for a description of their most significant challenges when traveling to school. Several rows of the data collected are shown in the table below.
Which column is data will likely be most difficult to visualize or analyze?
A. How Travel
B. How Long
C. Time Arrive
D. Biggest Challenges
Answers
Answer: D.
Explanation: I can't say this is the correct answer for sure since the chart is not there but I'm pretty sure the answer is D. This video might help you out on the subject. https://youtu.be/dQw4w9WgXcQ
The column in which the data will likely be most difficult to visualize or analyze is Biggest Challenges. The correct option is D.
What is survey?A survey is a research method that involves gathering information from a group of people through the use of pre-designed questions or structured interviews.
A survey's purpose is to collect information about people's opinions, beliefs, attitudes, behaviors, or experiences on a specific topic.
Biggest Challenges is the column in which the data will most likely be difficult to visualize or analyze.
The table's other columns, How Travel, How Long, and Time Arrive, all contain quantitative data that can be easily visualized and analyzed.
The How Travel column, for example, could be represented by a pie chart or bar graph depicting the percentage of students who walk, bike, drive, or take the bus to school.
Thus, the correct option is D.
For more details regarding survey, visit:
https://brainly.com/question/17373064
#SPJ3
Write a short program in assembly that reads the numbers stored in an array named once, doubles the value, and writes them to another array named twice. Initialize both arrays in the ram using assembler directives. The array once should contain the numbers {0x3, 0xe, 0xf8, 0xfe0}. You can initialize the array twice to all zeros
Answers
Answer:
Assuming it's talking about x86-64 architecture, here's the program:
section .data
once: dd 0x3, 0xe, 0xf8, 0xfe0
twice: times 4 dd 0
section .text
global _start
_start:
mov esi, once ; set esi to the start of the once array
mov edi, twice ; set edi to the start of the twice array
mov ecx, 4 ; set the loop counter to 4 (the number of elements in the arrays)
loop:
mov eax, [esi] ; load a value from once into eax
add eax, eax ; double the value
mov [edi], eax ; store the result in twice
add esi, 4 ; advance to the next element in once
add edi, 4 ; advance to the next element in twice
loop loop ; repeat until ecx is zero
; exit the program
mov eax, 60 ; system call for exit
xor ebx, ebx ; return code of zero
syscall
Explanation:
The 'dd' directive defines the once array with the specified values, and the 'times' directive defines the twice array with four zero values.
It uses the 'mov' instruction to set the registers 'esi' and 'edi' to the start of the once and twice arrays respectively. Then it sets the loop counter 'ecx' to 4.
The program then enters a loop that loads a value from once into 'eax', doubles the value by adding it to itself, stores the result in twice, and then advances to the next element in both arrays. This loop will repeat until 'ecx' is zero.
Hope this helps! (By the way, the comments (;) aren't necessary, they're just there to help - remember, they're not instructions).
A technician wishes to update the nic driver for a computer. What is the best location for finding new drivers for the nic? select one:.
Answers
The best place to find new drivers for the NIC is the website for the manufacturer of NIC. So the answer is C.
NIC is stand for A network interface controller. NIC, also called as a network interface card, network adapter, LAN adapter or physical network interface, and by similar terms can be described as a computer hardware element that associated a computer to a computer network. Compared to the wireless network card, NIC recognizes a secure, faster, and more reliable connection. NIC lets us to share bulk data among many users. NIC can helps us to link peripheral devices using many ports of NIC.
The question is not complete. The complete question can be seen below:
What is the best location for finding new drivers for the NIC? Group of answer choices
A. Windows Update the installation media that came with the NIC
B. the installation media for Windows
C. the website for the manufacturer of the NIC
D. the website for Microsoft.
Learn more about NIC at https://brainly.com/question/17060244
#SPJ4
a customer needs to look up tips for proper machine use in the user guide for their product. they do not know where to find the user guide. where should you tell them to look?
Answers
A task-oriented document is a user manual or guide. It includes operating and maintenance instructions as well as technical descriptions, drawings, flowcharts, and diagrams.
Even though instructions on how to use or repair a product are documented, it might not always suit the intended purpose. A user handbook, often referred to as a user guide, is designed to help users use a specific good, service, or application. Typically, a technician, a product developer, or a member of the company's customer support team will write it. Because of this, nonvolatile memory—which retains its data even if a computer's power is switched off or a storage device is unplugged from a power source—is frequently employed in conjunction with RAM. Additionally, unlike some volatile memory, nonvolatile memory does not require periodic content refreshment.
Learn more about memory here-
https://brainly.com/question/28754403
#SPJ4
what two optical disc drive standards allow for rewritable discs
Answers
Two optical disc drive standards that allow for rewritable discs are CD-RW and DVD-RW.
1. CD-RW (Compact Disc Rewritable): CD-RW drives allow users to write and rewrite data onto CD-RW discs. These discs can be erased and reused multiple times, making them suitable for data storage and transfer.
2. DVD-RW (Digital Versatile Disc Rewritable): DVD-RW drives are capable of writing and rewriting data onto DVD-RW discs. Similar to CD-RW, these discs can be erased and reused multiple times, providing a flexible storage solution for larger files, videos, and multimedia content.
Both CD-RW and DVD-RW drives use a laser to alter the physical properties of the disc's recording layer, allowing for multiple write cycles. It's important to note that the compatibility of CD-RW and DVD-RW discs depends on the device you intend to use them with. Some older CD and DVD players may not be able to read or play rewritable discs.
In summary, CD-RW and DVD-RW are two optical disc drive standards that allow for rewritable discs. These drives offer users the ability to write, erase, and rewrite data onto CD-RW and DVD-RW discs, respectively, providing a flexible storage solution.
To know more about optical visit :-
https://brainly.com/question/31664497
#SPJ11
two lists showing the same data about the same person is an example of
Answers
When two or more lists display the same data about the same person, they are called duplicate data. Duplicate data is common in a variety of settings, including data management and personal finance software. Users may have entered the same data twice, resulting in two identical entries for the same person or item.
The presence of duplicates in a data set can make data analysis more difficult and result in inaccurate results. As a result, duplicate data detection and elimination are essential in ensuring data quality and accuracy.In the context of databases, a unique index is frequently used to guarantee that data is entered only once.
This unique index prohibits multiple entries of the same data for the same person. It also ensures that data is input in a consistent and accurate manner.
To know more about software visit:
https://brainly.com/question/32393976
#SPJ11
Can scratch cloud variables save across computers? For example, if I save the cloud variable as 10, then log in from a different computer will that variable save from that other computer?
Answers
Answer:
Explanation:
Scratch cloud variables are a feature in Scratch, a visual programming language, that allows for saving and sharing data across different projects and even across different computers. Once a variable is saved as a cloud variable, it can be accessed from any other project that has been shared with the same Scratch account.
If you set the value of a cloud variable to 10 on one computer, and then log in to Scratch from a different computer using the same Scratch account, you will be able to access the variable and its value (10) from that other computer.
It is important to note that the cloud variable feature is only available for Scratch accounts with a login, if you don't have a Scratch account, you won't be able to use this feature.
It's also good to keep in mind that if you set a variable as a cloud variable in a project, it will be accessible to anyone who has access to that project. So make sure you understand the sharing settings and permissions before using cloud variables in a project that contains sensitive information.
The invention of computers as a technological tool has completely changed our lives. Name any three areas to support this statement and explain how computers have made our lives better
Answers
Answer:
-They allow huge amounts of information to be stored in a small space
-They also allow a person to calculate mathematical problems with ease
-They allow people to communicate with one another through internet sites
-Finally, computers provide teachers and students the means to communicate quickly via email. Online grading systems also make it easier to view and audit a student's progress
Hope i helped!
Why would Claire, who has a Certified Information Systems Security Professional credential, object to shadow IT efforts at her company
Answers
Security experts who make sure that their firm complies with IT governance regulations are the target audience for the ISACA certified in risk and information system control certification.
ISACA is a global professional organization specializing on IT governance. Although ISACA currently just uses its acronym, it is still referred to in its IRS filings as the Information Systems Audit and Control Association. Association for Information Systems Audit and Control.
ISACA created the Certified in Risk and Information Systems Control (CRISC) program to help students better comprehend the implications of IT risk and determine how it applies to their organization.
To learn more about ISACA visit:
brainly.com/question/30031847
#SPJ4
is the area where we createour drawings
Answers
Answer:
Answer:
CANVAS IS THE AREA WHERE WE CREATE OUR DRAWING.
Explanation:
.
Answer: CANVAS IS THE AREA WHERE WEE CREATE OUR DRAWING.
Explanation:
In the context of the operators used in a query by example (QBE) form, the _____ is used when only one of the conditions in the QBE form must be met. Group of answer choices NOT operator AND operator OR operator NOR operator
Answers
In the context of the operators used in a query by example (QBE) form, the OR operator is used when only one of the conditions in the QBE form must be met.The Query by Example (QBE) form is used to query a database.
A QBE form is a grid that allows the user to define and execute database queries by drawing a sample of the data they want to recover. The QBE system can be used in both a relational and non-relational setting.OR operator stands for "logical disjunction," and is commonly used in computer programming to refer to Boolean logic, which is based on Boolean algebra. OR operator is used to determine the logical sum of two Boolean expressions. In QBE, it is used to identify the disjunction (or logical "or") between two Boolean expressions in a query
.The OR operator is used when only one of the conditions in the QBE form must be met. For example, in a database of books, one may want to find all books that have either been published in the last 5 years or are written by a particular author. In such a situation, the OR operator is used to combine two criteria so that either one can be met for a book to be included in the results.
To know more about operators visit:
https://brainly.com/question/29949119
#SPJ11
Hey, Another question. I'm sure it's possible in the future, but I wanted to ask if HIE would be possible. I'm sure it would be, I just want to hear other people's comments on this. (Beatless)
Answers
Answer:
Originally Answered: Will there ever be a band as big as the Beatles? No, there will never be a band as popular as the Beatles. For one thing they were exceptionally good in a time of great music in general.
Explanation:
please mark this answer as brainliest
which camera is interchangeable
freeform
hybrid
DSLR
point and shoot
Answers
Answer:
DSLR
Explanation:
Double check my answer
Topics with problems or controversies are strong topic ideas.
Please select the best answer from the choices provided
T
F
Answers
Answer:
This would be considered true
Topics with problems or controversies are strong topic ideas is a true statement.
What is ideas in philosophy?The term ideas is known to be the outcome of human thoughts.
Based on the above, Topics with problems or controversies are strong topic ideas is a true statement because they are entered on relevant areas of human live that need to be addressed.
Learn more about ideas from
https://brainly.com/question/540693
#SPJ1
The linux/unix command __________ can be used to search for files or contents of files.
Answers
What is the index of the last element? int numList[50]: O a. 0 O b.49 O c. 50 O d. Unknown, because the array has not been initialized.
Answers
Answer:
b. 49
Explanation:
What is the basic function of a media gateway and where do they appear in the network topology?
Answers
The basic function of a media gateway is to facilitate the conversion and transmission of voice and multimedia data between different networks.
It acts as a bridge between different types of communication networks, such as traditional telephone networks (PSTN) and IP-based networks (such as the internet or private IP networks). Media gateways perform protocol conversions and support various audio and video codecs to enable seamless communication across different networks. In terms of network topology, media gateways can appear at various points depending on the network architecture.
They are typically found at the edge of the network, where different types of networks converge. For example, in a traditional telecommunication network, media gateways are placed at the point of interconnection between the PSTN and the IP network. In an IP-based network, media gateways may appear at the border between the IP network and the public switched telephone network.
Learn more about media gateway: https://brainly.com/question/30724116
#SPJ11
The following piece of code has an error. Select the best category for the error.
score = 75
percent = score / (100-100)
Group of answer choices
a. Syntax
b. Run time
c. Logic or semantic
Answers
The best category for the error is score = 75 c. Logic or semantic.
The error in the code is a logical or semantic error. The variable "percent" is being assigned a value based on a formula that divides "score" by the difference between 100 and 100 (which is 0). This results in a division by zero error and an incorrect value being assigned to "percent". The syntax of the code is correct, and there are no issues that would cause a run time error.
Text that is grammatically correct but makes no sense is a semantic mistake. In the case of the C# programming language, an illustration would be "int x = 12.3;" - This sentence is illogical since 12.3 is not an integer literal and there is no implicit conversion from 12.3 to int.
Semantic errors are issues with a software that runs properly but accomplishes the wrong thing despite not generating error messages. As an illustration, an expression might not be assessed in the sequence you anticipate, leading to an inaccurate outcome.
Semantic mistake definitions. a mathematical or logical error that needs to be found at run time.
To know more about semantic error, click here:
https://brainly.com/question/873851
#SPJ11
The error in the given code is a logic or semantic error due to the incorrect calculation of the denominator value.
It is important to identify and rectify such errors to ensure the correct functioning of the code.
The error in the given code falls under the category of logic or semantic errors.
This is because the code is trying to divide the score by (100-100), which is equal to zero.
Any number divided by zero is undefined, and hence the calculation is not logically correct.
The code is trying to calculate the percentage of the score, but due to the logical error, it is not achieving the desired result.
This error could lead to incorrect results and affect the performance of the code.
To rectify this error, we need to change the denominator value to a non-zero value.
In this case, we need to subtract 100 from 100, which will result in zero.
Instead, we should subtract 100 from 100 percent, which is equal to one.
The corrected code should be:
score = 75
\(percent = score / (100-100)\)
\(percent = score / (100-100)\)
\(percent = score / (1-1)\)
\(percent = score / 0.01\)
\(percent = score \times 100\)
In this corrected code, we first subtract 100 from 100 percent to get the correct denominator value.
Then we divide the score by the corrected denominator value to get the percentage.
Finally, we multiply the result by 100 to get the percentage value in the desired format.
For similar questions on Error
https://brainly.com/question/30062195
#SPJ11
What is the difference between the = operator and the == operator in Java?
= denotes an allocation, and == denotes an assignment
= denotes an assignment, and == denotes a comparison
= denotes an initialization, and == denotes a comparison
= denotes a comparison, and == denotes an assignment
Answers
Answer:
The are different severs I guess
Explanation:
7.2 code practice edhesive. I need help!!
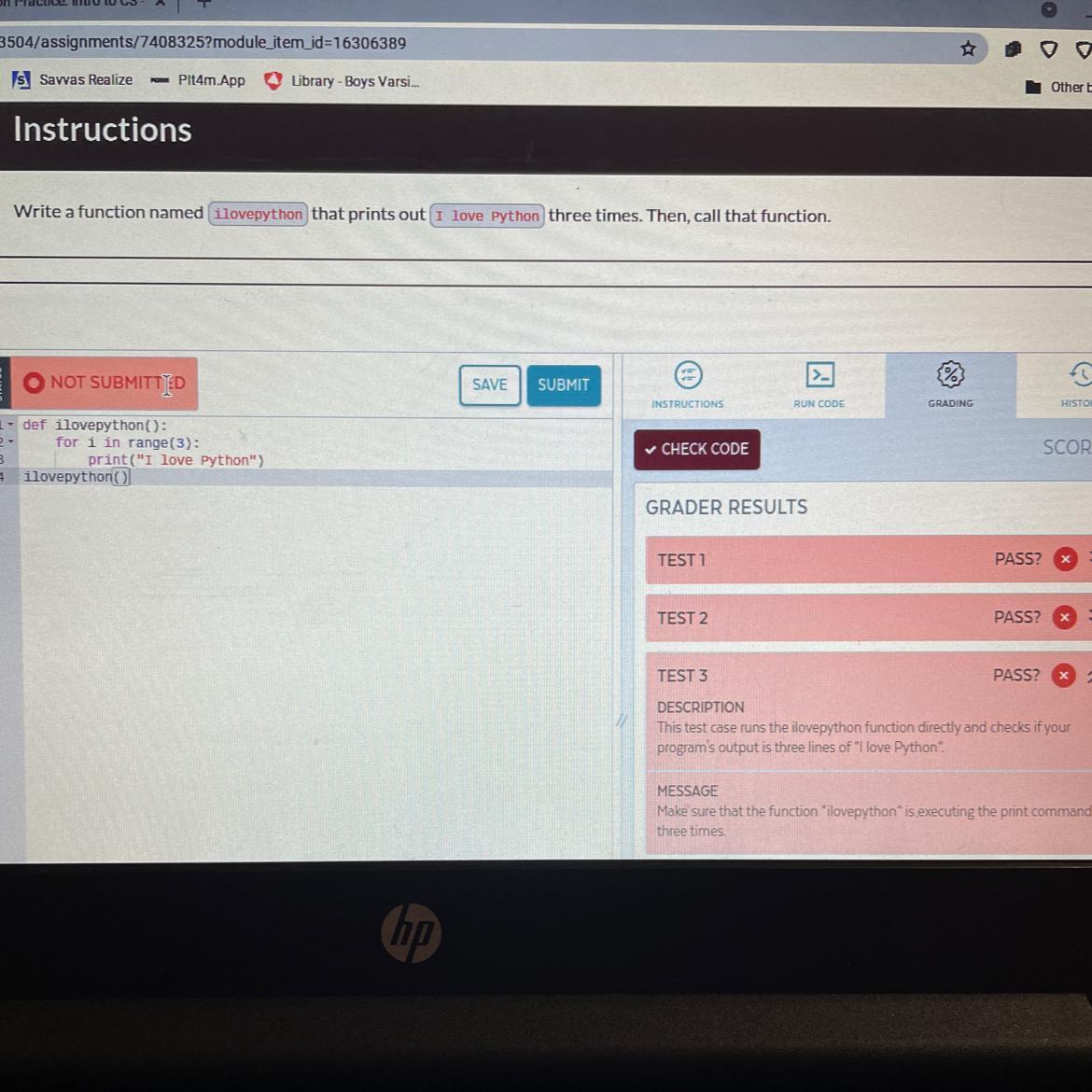
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
...This is totally a question

Answers
Answer: No Answer
Explanation: No Explanation
which term refers to the data stored in computer memory on which the processor applies to program instructions
A.) equation
B.) variable
C.) operand
D.) integer
Answers
Answer:
I'm not 100% sure but i think the answers D
Explanation:
Answer: C. Operand
Explanation: Got it right on test
consider a logical address space of 64 pages of 1,024 words each, mapped onto a physical memory of 32 frames. a. how many bits are there in the logical address? b. how many bits are there in the physical address?
Answers
The logical address requires 16 bits to represent it, while the physical address requires 15 bits.
To determine the number of bits in the logical address, we need to consider the number of pages in the logical address space. With 64 pages, we require log2(64) = 6 bits to represent the page number. Additionally, we need log2(1024) = 10 bits to represent the word offset within each page. Thus, the logical address consists of 6 + 10 = 16 bits.
For the physical address, we need to calculate the number of bits required to represent the frame number. With 32 frames in the physical memory, we need log2(32) = 5 bits to represent the frame number. The word offset within each frame remains the same as in the logical address, requiring 10 bits. Therefore, the physical address consists of 5 + 10 = 15 bits.
Learn more about logical address here;
https://brainly.com/question/13013906
#SPJ11