technical term a program that destroy flies and hangs computer frequently
Answers
Answer:
A Bug.
Explanation:
Related Questions
Avery just got her driver’s license. Because she isn’t too familiar with the roads and routes, she decides to use an app to help her navigate. Which one should she use?
Answers
Answer:
Most likely a modern GPS app because it displays roads, popular/frequently visited buildings/locations, and allows you to put in an address to find directions.
a network card on a machine is receiving packets at an average rate of 100 packets per second. if we assume that each packet causes the network interrupt service routine (isr) to execute for 0.2 millisecond, what percentage of the cpu time is used in handling network packets?
Answers
20% of the cpu time is used in handling network packets as a network card on a machine is receiving packets at an average rate of 100 packets per second.
What is CPU time?CPU time is the amount of time a central processing unit was utilized to process instructions from a computer program or operating system, as opposed to elapsed time, which includes things like waiting for input/output operations or going into low-power mode. CPU time is expressed in clock ticks or seconds. CPU time (countable and uncountable, plural CPU times) (computing) The time it takes a central processing unit to process instructions for a certain program or job.
To know more about CPU time,
https://brainly.com/question/18568238
#SPJ4
PLEASEEE HELP HURRY

Answers
To start searching for a scholarly article on G. o. ogle Scholar, you should:
"Type the title of the article or keywords associated with it." (Option A)
What is the rationale for the above response?Here are the steps you can follow:
Go to Go. o. gle Scholar website In the search box, type the title of the article or relevant keywords associated with it.Click the "Search" button.Browse through the search results to find the article you are looking for.Click on the title of the article to view the abstract and other details.If the article is available for free, you can download or access it directly from the search results page. If not, you may need to purchase or access it through a library or other academic institution.Note that you can also use advanced search options and filters available on Go. ogle Scholar to narrow down your search results based on various criteria, such as publication date, author, and journal.
Learn more about G. o. ogle at:
https://brainly.com/question/28727776
#SPJ1
The main reason for formatting message style and theme is that it can be useful for making your message
more entertaining to the reader.
easier to send and receive.
professional in appearance.
top priority for the reader.
Answers
Answer:
The answer is C
Explanation:
CCCCC
Answer:
C
Explanation:
Answered myself.
Someone help pleaseee
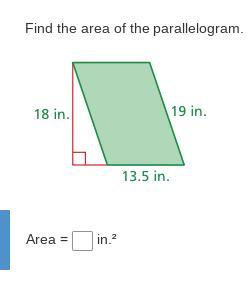
Answers
Answer:
243in^2
Explanation:
Area= base x height
base=13.5
height=18
A= 13.5 x 18
A=243in^2
hope this helps :)
The key to learn about and engage with individual customers is to blend the new digital technologies and approaches with traditional marketing to create what?
Answers
The key to learn about and engage with individual customers is to blend the new digital technologies and approaches with traditional marketing to create a personalized approach.
What is digital technologies ?Digital technologies are the use of computer systems and other digital devices to store and manipulate data, transmit data over a network, or display information for users. Digital technologies include computers, mobile phones, the internet, social networks, digital media, digital signals, and software. Digital technologies have had a major impact on the way people live and work, as well as on businesses, education, and entertainment. Digital technologies provide new opportunities for communication, collaboration, and innovation.
This approach can involve using data-driven strategies like personalized emails, tailored advertising and personalized content.
To learn more about digital technologies
https://brainly.com/question/25719495
#SPJ4
The first commercially available digital camera was which of the following?
Answers
Kodak Professional Digital Camera System
hope it helps
pls mark me as brainliest
Answer:
D
Explanation:
None of the above
____ allow us to store a binary image in code. (1 point)
Bitmaps
Classes
Arrays
Unions
Answers
Answer:
A. Bitmaps
Explanation:
if the current date is march 1, 2023, which javascript statement(s) should you use to set an expiration date for a cookie that is one year in the future?
Answers
To set an expiration date for a cookie that is one year in the future from the current date of March 1, 2023 in JavaScript, you can use the following statement:
var d = new Date();
d.setTime(d.getTime() + (365 * 24 * 60 * 60 * 1000));
var expires = "expires="+ d.toUTCString();
document.cookie = "cookieName=cookieValue;" + expires + ";path=/";
In this statement, we first create a new Date object and set it to the current date and time using the new Date() constructor. Then we set the expiration date of the cookie to one year in the future by adding the number of milliseconds in a day (24 hours) multiplied by the number of days in a year (365) to the current time using the setTime() method.
Next, we convert the expiration date to a UTC string using the toUTCString() method, and store it in a variable called expires.
Finally, we set the cookie by using the document.cookie property and specifying the name and value of the cookie, as well as the expires attribute and the path attribute, which sets the scope of the cookie to the root directory of the website.
To set an expiration date for a cookie that is one year in the future from the current date of March 1, 2023, the following JavaScript statement should be used:
var expirationDate = new Date();
expirationDate.setFullYear(expirationDate.getFullYear() + 1);
document.cookie = "cookieName=value;expires=" + expirationDate.toUT
In JavaScript, cookies can be created and set with an expiration date using the document.cookie property. To set an expiration date for a cookie that is one year in the future from the current date, a new Date object is first created, representing the current date and time. The setFullYear() method is then used to add one to the current year, which sets the year of the expirationDate object to 2024.
To set the cookie with the cookieName and value specified, the document.cookie property is assigned a string that includes the expires attribute followed by the expiration date formatted as a UTC string using the toUTCString() method. This sets the expiration date of the cookie to March 1, 2024, which is exactly one year after the current date of March 1, 2023.
""
Complete question
if the current date is march 1, 2023, which javascript statement(s) should you use to set an expiration date for a cookie that is one year in the future?
a: var expirationDate = new Date();
expirationDate.setFullYear(expirationDate.getFullYear() + 1);
document.cookie = "cookieName=value;expires=" + expirationDate.toUT
b: var expirationDate = new Time();
expirationDate.setFullYear(expirationDate.getFullYear() + 1);
document.cookie = "cookieName=value;expires=" + expirationDate.toUT
""
You can learn more about JavaScript at
https://brainly.com/question/29846946
#SPJ11
Please help. You dont need to answer the extension.

Answers
Answer:
Hope the below helps!
Explanation:
#Program for simple authentication routine
name = input("Enter name: ")
password = input("Enter password (must have at least 8 characters): ")
while len(password) < 8:
print("Make sure your password has at least 8 characters")
password = input("Enter password (must have at least 8 characters): ")
else:
print("Your password has been accepted - successful sign-up")

Submit your definitions for the words below:
gigabyte
intranet
pixel
telecommunication
modem
raster graphic
vector graphic
digital
GUI
Answers
Answer:
1. gigabyte- Technology branded as GIGABYTE or sometimes GIGA-BYTE; formally GIGA-BYTE Technology Co., Ltd. it is a Taiwanese manufacturer and distributor of computer hardware. Gigabyte's principal business is motherboards.
2. intranet-a computer network for sharing information, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders.
3. pixel-a minute area of illumination on a display screen, one of many from which an image is composed.
4. telecommunication-the transmission of information by various types of technologies over wire, radio, optical or other electromagnetic systems.
5. modem- a combined device for modulation and demodulation, for example, between the digital data of a computer and the analog signal of a phone line.
6. raster graphic-In computer graphics and digital photography, a raster graphic or bitmap image is a dot matrix data structure that represents a generally rectangular grid of pixels (points of color), viewable via a bitmapped display (monitor), paper, or other display medium.
7. vector graphic-computer graphics images that are defined in terms of points on a Cartesian plane, which are connected by lines and curves to form polygons and other shapes.
8. digital-expressed as series of the digits 0 and 1, typically represented by values of a physical quantity such as voltage or magnetic polarization.GUI-a system of interactive visual components for computer software.
9. GUI- displays objects that convey information, and represent actions that can be taken by the user. The objects change color, size, or visibility when the user interacts with them.punineep and 15 more users found this answer helpful4.0(6 votes)
Explanation:
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
When did the internet reach the novelty (development), entrepreneurial, and mass medium stages?
Answers
The internet reached different stages of development at various points in history:
Novelty (Development) Stage:
The novelty stage of the internet began in the late 1960s with the creation of ARPANET, the precursor to the modern internet. During this stage, the internet was primarily used by researchers, scientists, and academics for sharing information and conducting experiments. It was a relatively small network limited to a few institutions.
Entrepreneurial Stage:
The entrepreneurial stage of the internet emerged in the 1990s with the widespread commercialization and popularization of the World Wide Web. This period saw the rise of internet companies, startups, and e-commerce ventures. It was characterized by the development of web-based services, online marketplaces, and the exploration of new business models enabled by the internet. This stage experienced rapid growth and innovation as companies sought to capitalize on the emerging digital landscape.
Mass Medium Stage:
The mass medium stage of the internet can be traced back to the early 2000s when internet usage became more pervasive and accessible to the general public. This stage is marked by the widespread adoption of the internet as a mainstream communication and information platform. It saw the rise of social media, online news consumption, streaming services, and the integration of the internet into various aspects of daily life. The internet became a dominant medium for connecting people, accessing content, and conducting business on a global scale.
It is important to note that these stages are not strictly defined and can overlap to some extent. The evolution of the internet is an ongoing process, with continuous advancements and shifts in usage patterns.
Learn more about Novelty (Development) Stage here:
https://brainly.com/question/32760647
#SPJ11
Write 4 types of viruses , explain them briefly.
Answers
I can help with two.
Web Scripting Virus, A sneaky virus that targets popular websites. What this virus does is overwrite code on a website and insert links that can install malicious software on your device. Web scripting viruses can steal your cookies and use the information to post on your behalf on the infected website.
FILE INFECTOR, targeting executable files (.exe), file infector viruses slow down programs and damage system files when a user runs them.
In what situations other than developing software might the process of analysis, design, development, test, deployment, and maintenance be a useful approach to problem solving?
Answers
In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach.
What is software development?Software development is known to be a term that connote the composition of computer science works made for the process of developing , designing, and aiding software.
Note that In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach. as it also uses the dteps listed above.
Learn more about software from
https://brainly.com/question/1538272
#SPJ1
Robert is leading a project online that includes students from different cultures. Two of the students spend most of the time listening intently but not speaking. Robert knows they are smart, but he becomes
frustrated when they don’t respond to his attempts to engage them.
Which excerpts from a report to his supervisor explains the most likely reason that the students don’t speak? Check all that apply.
A. There are differences in our communication styles because of the cultures the students grew up in.
B. Online meetings are an ineffective way to meet with people from different cultures.
C. There are differences in social behaviors because the students come from cultures that emphasize listening.
D, The language barrier is too great for our group to have an effective meeting online.
E. Online meetings make it hard for the students to discuss material they don’t understand.
Answers
Answer:
A & C
Explanation:
Answer:
A&C
Explanation:
I took this on a test
Choose the correct answers. The process of classifying information ......
a. Should be resulted from multidisciplinary workshops
b. is the main objective of information security
c. is a one-time activity
d. should be done on an ongoing basis
Which is not an advantage of information classification
a.Identifying critical asset
b.Promoting sound risk management
c.Ensuring the safety of human resources
d.Facilitating decision-making and helping target investments in terms of information protection
Which is not a risk treatment option?
a.Eliminating the risk
b.Mitigating the risk
c.Transferring the risk
d.Accepting the risk
e.Avoiding the risk
Answers
1. The process of classifying information should be done on an ongoing basis, and it is not a one-time activity resulting from multidisciplinary workshops or the main objective of information security.
2. Ensuring the safety of human resources is not an advantage of information classification, while identifying critical assets, promoting sound risk management, and facilitating decision-making are advantages.
3. Avoiding the risk is not a risk treatment option, but eliminating, mitigating, transferring, and accepting the risk are valid options.
1. The process of classifying information is an ongoing activity that involves categorizing information based on its sensitivity, importance, or level of confidentiality. It is not a one-time activity resulting from multidisciplinary workshops. While information security aims to protect information, classification itself is not its main objective.
2. Ensuring the safety of human resources is not an advantage of information classification. However, identifying critical assets is an advantage as it helps prioritize protection efforts, promoting sound risk management allows for effective allocation of resources, and facilitating decision-making and targeting investments in information protection enhances overall security measures.
3. Avoiding the risk is not a risk treatment option. The valid risk treatment options include eliminating the risk by removing the cause, mitigating the risk by implementing controls, transferring the risk through insurance or contracts, and accepting the risk by acknowledging and living with it within acceptable limits. Avoidance implies not engaging in activities that pose a risk, which is different from treating or managing the risk.
learn more about workshop here
https://brainly.com/question/31026752
#SPJ11
236. A system such as a printer, smart TV, or HVAC controller, typically uses an operating system on what is called a:
Answers
Answer:
Embedded System
Answer:
Embedded system
Explanation:
A embedded system is a microprocessor-based computer hardware system with software that is designed to perform a dedicated function, either as an independent system or as a part of a large system.
When you insert a Quick table, you cannot format it true or false
Answers
Answer:
True
Explanation:
Format the table the way you want — e.g. borders, shading, row height, alignment, emphasis, font size, etc. for the heading row and the table rows. You can use manual formatting, or one of the built-in table designs
how come when i go to get a answer and watch a video, it never shows me a video and it just sits there and it wont answer any question
Answers
any traffic from the local host to a remote host for purposes of an ike exchange bypasses the ipsec processing
True or False
Answers
The given statement "any traffic from the local host to a remote host for purposes of an ike exchange bypasses the ipsec processing" is true because the Internet Key Exchange (IKE) protocol is used to establish a secure communication channel between two hosts.
The IPsec protocol is used to encrypt and protect the data that is transmitted over that channel.
During the IKE exchange, the hosts negotiate the security parameters that will be used for the IPsec connection, such as the encryption algorithm and the key lifetime. Once these parameters have been agreed upon, the actual data transmission can begin.
At this point, any traffic that is sent from the local host to the remote host is already encrypted and protected by IPsec, so there is no need for further processing by the IPsec module.
However, it's important to note that this only applies to traffic that is specifically related to the IKE exchange. If the local host sends any other traffic to the remote host (such as web traffic or email), that traffic will still need to be processed by IPsec in order to ensure its security.
Additionally, if there are any errors or security issues with the IKE exchange itself, the IPsec processing may need to be re-applied in order to maintain a secure connection.
Learn more about Internet Protocol Security (IPsec) protocol.:https://brainly.com/question/29805968
#SPJ11
Describe how a cell’s content and format attributes are related.
Answers
Answer: They are independent and not related.
Explanation: Changing the format affects the content. Which of the following is NOT a way to change the column width in Excel?
hope this helps
What can you add to your presentation from the Insert tab?
Animations
Pictures
Variants
Transitions
Answers
Answer:
B. PICTURES
Explanation:
Answer:
I know its late but pictures is the answer.
Explanation:
I took the test and got it right.
the formula =sum(b2:b10 finds the?
Answers
Answer:
sum (addition) of all the numbers in cells b2 to b10.
Explanation:
9.18 lab: even/odd values in a vector write a program that reads a list of integers, and outputs whether the list contains all even numbers, odd numbers, or neither. the input begins with an integer indicating the number of integers that follow. ex: if the input is 5 2 4 6 8 10, the output is: all even ex: if the input is 5 1 3 5 7 9, the output is: all odd ex: if the input is 5 1 2 3 4 5, the output is: not even or odd your program must define and call the following two functions. isvectoreven returns true if all integers in the array are even and false otherwise. isvectorodd returns true if all integers in the array are odd and false otherwise. bool isvectoreven(vector myvec) bool isvectorodd(vector myvec)
Answers
def is_list_even(my_list):
for i in my_list:
if(i%2 != 0):
return False
return True
def is_list_odd(my_list):
for i in my_list:
if(i%2 == 0):
return False
return True
def main():
n = int(input())
lst = []
for i in range(n):
lst.append(int(input()))
if(is_list_even(lst)):
print('all even')
elif(is_list_odd(lst)):
print('all odd')
else:
print('not even or odd')
if __name__ == '__main__':
main()
In the game Badland, how do you get to the next level?
A.
If you get close enough to the exit pipe, it sucks you up and spits you out in the next level.
B.
If you shoot enough enemies, you automatically advance to the next level.
C.
If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
D.
If you answer enough puzzles correctly, you advance to the next level.
Answers
In the game Badland, the way a person get to the next level is option C: If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
What is the story of BADLAND game?
The story occurs throughout the span of two distinct days, at various times during each day's dawn, noon, dusk, and night. Giant egg-shaped robots start to emerge from the water and background and take over the forest as your character is soaring through this already quite scary environment.
Over 30 million people have played the side-scrolling action-adventure game BADLAND, which has won numerous awards. The physics-based gameplay in BADLAND has been hailed for being novel, as have the game's cunningly inventive stages and breathtakingly moody sounds and visuals.
Therefore, in playing this game, the player's controller in Badland is a mobile device's touchscreen. The player's Clone will be raised aloft and briefly become airborne by tapping anywhere on the screen.ult for In the game Badland, the way a person get to the next level.
Learn more about game from
https://brainly.com/question/908343
#SPJ1
state the types of Data range
Answers
There about 5 types of data range. See them below.
What are the various types of data range?Numeric range: This is a range of values that can be expressed as a numerical value.
Boolean range: This is a range of values that can be either true or false. Boolean data types are commonly used for logical expressions and conditional statements.
Character range: This is a range of values that can be represented as a character or string of characters. Character data types are commonly used for text-based data.
Date/time range: This is a range of values that can be expressed as a date or time value. Date/time data types are commonly used for tracking events or scheduling tasks.
Enumeration range: This is a range of values that can be expressed as a predefined set of values.
Learn more about data range at:
https://brainly.com/question/20607770
#SPJ1
1-DESIGN TAB....................2-LAYOUT TAB .
1-wordart styles,
2-table size,
1-Table styles,
2-alignment,
1-draw borders,
2-rows and columns

Answers
design tab
wordart stylestable stylesdraw borderlayout tab
table sizerows and columnsalignmentAnswer:
The person above is correct.
Explanation:

¿Podría decir que la Tecnología cumple como medio y herramienta para
satisfacer necesidades? Justifique su respuesta.
Answers
Answer:
gggaghqjgfdttedfvqtffqgfq graffiti qtrdgg
In the U6_L2_Activity_Three class, write a public static method called hasDuplicates, which has a single parameter of an array of int values. The method should return a boolean which is true if the parameter array contains the same value more than once, and false otherwise. Use the runner class to test this method: do not add a main method to your code in the U6_L2_Activity_Three. Java file or it will not be scored correctly
Answers
Answer:
Here is an implementation of the hasDuplicates method in the U6_L2_Activity_Three class:
import java.util.HashSet;
public class U6_L2_Activity_Three {
public static boolean hasDuplicates(int[] array) {
// Create a HashSet to store the values in the array
HashSet<Integer> set = new HashSet<>();
// Iterate through the array and add each value to the set
for (int value : array) {
if (set.contains(value)) {
// If the value is already in the set, return true
return true;
}
set.add(value);
}
// If no duplicates were found, return false
return false;
}
}
To test this method, you can use the Runner class like this:
public class Runner {
public static void main(String[] args) {
int[] array1 = {1, 2, 3, 4, 5};
int[] array2 = {1, 2, 2, 3, 4, 5};
int[] array3 = {1, 1, 2, 3, 4, 5};
System.out.println(U6_L2_Activity_Three.hasDuplicates(array1)); // should print false
System.out.println(U6_L2_Activity_Three.hasDuplicates(array2)); // should print true
System.out.println(U6_L2_Activity_Three.hasDuplicates(array3)); // should print true
}
}
Explanation:
This will print false, true, and true to the console, indicating that the hasDuplicates method is working as expected.