The key difference between narrow intelligence and broad intelligence is best described by which of the following phrases:
Determine machine's human ability.
Narrow AI can only do a certain task - and it can do it quite well - but narrow AI can't transfer its knowledge to different sorts of problems as with Broad AI.
The ability to use previous experiences to come up with new creative ideas.
Answers
The key difference between narrow intelligence and broad intelligence is best described by the phrase: Narrow AI can only do a certain task - and it can do it quite well - but narrow AI can't transfer its knowledge to different sorts of problems as with Broad AI.
What is narrow intelligence and broad intelligence?
Narrow intelligence can be defined as the capacity to focus on a single task or ability. People with narrow intelligence have great expertise in a single area of activity. It refers to an individual's ability to conduct specific tasks, functions, or operations while disregarding others.
Broad intelligence, on the other hand, refers to the capacity to perform various functions or adapt to a range of circumstances. A person who possesses a broad range of abilities and knowledge is said to have broad intelligence. They can do a range of tasks and solve various problems.
What is the key difference between narrow intelligence and broad intelligence?
Narrow AI refers to the intelligence of machines designed to execute a single task. It can't adapt to other tasks, whereas broad AI refers to the intelligence of machines designed to execute a wide range of tasks. The key difference between narrow intelligence and broad intelligence is best described by the phrase: Narrow AI can only do a certain task - and it can do it quite well - but narrow AI can't transfer its knowledge to different sorts of problems as with Broad AI.
Learn more about Narrow intelligence at https://brainly.com/question/31145681
#SPJ11
Related Questions
1. What does "IdentifyGrid" do?
2. What do "Set_Grids" and "PickAGrid" do?
3.Why did you use if-else if-else blocks? What do they do while the program running? How did you create your conditions?
Answers
Using the knowledge of computational language in C++ it is possible to write a code that "Set_Grids" and "PickAGrid".
The "IdentifyGrid" do:subroutine set_grids
use species, only: init_species
use egrid, only: setvgrid, x0, x0_maxw, zeroes, zeroes_maxw
use species, only: nspec, spec, f0_maxwellian
use theta_grid, only: init_theta_grid, ntgrid, nbset, bset, eps_trapped
use file_utils, only: open_output_file, close_output_file
use mp, only: proc0
implicit none
integer :: tsize,is
logical :: has_maxwellian_species
integer :: unit
call init_theta_grid
call init_species
allocate (dele(negrid,nspec),speed(negrid,nspec),speed_maxw(negrid),w_maxw(negrid),energy_maxw(negrid))
w_maxw = 0.0
energy_maxw = 0.0
speed_maxw = 0.0
has_maxwellian_species = .false.
speed = sqrt(energy)
do is = 1,nspec
if (spec(is)%f0type .EQ. f0_maxwellian) then
has_maxwellian_species = .true.
w_maxw(:) = w(:,is)
energy_maxw(:) = energy(:,is)
speed_maxw(:) = speed(:,is)
zeroes_maxw(:) = zeroes(:,is)
x0_maxw = x0(is)
exit
end if
end do
if (.not. has_maxwellian_species) write(*,*) &
'Warning; no maxwellian species; collisions will fail'
See more about C++ at brainly.com/question/29594386
#SPJ1

Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
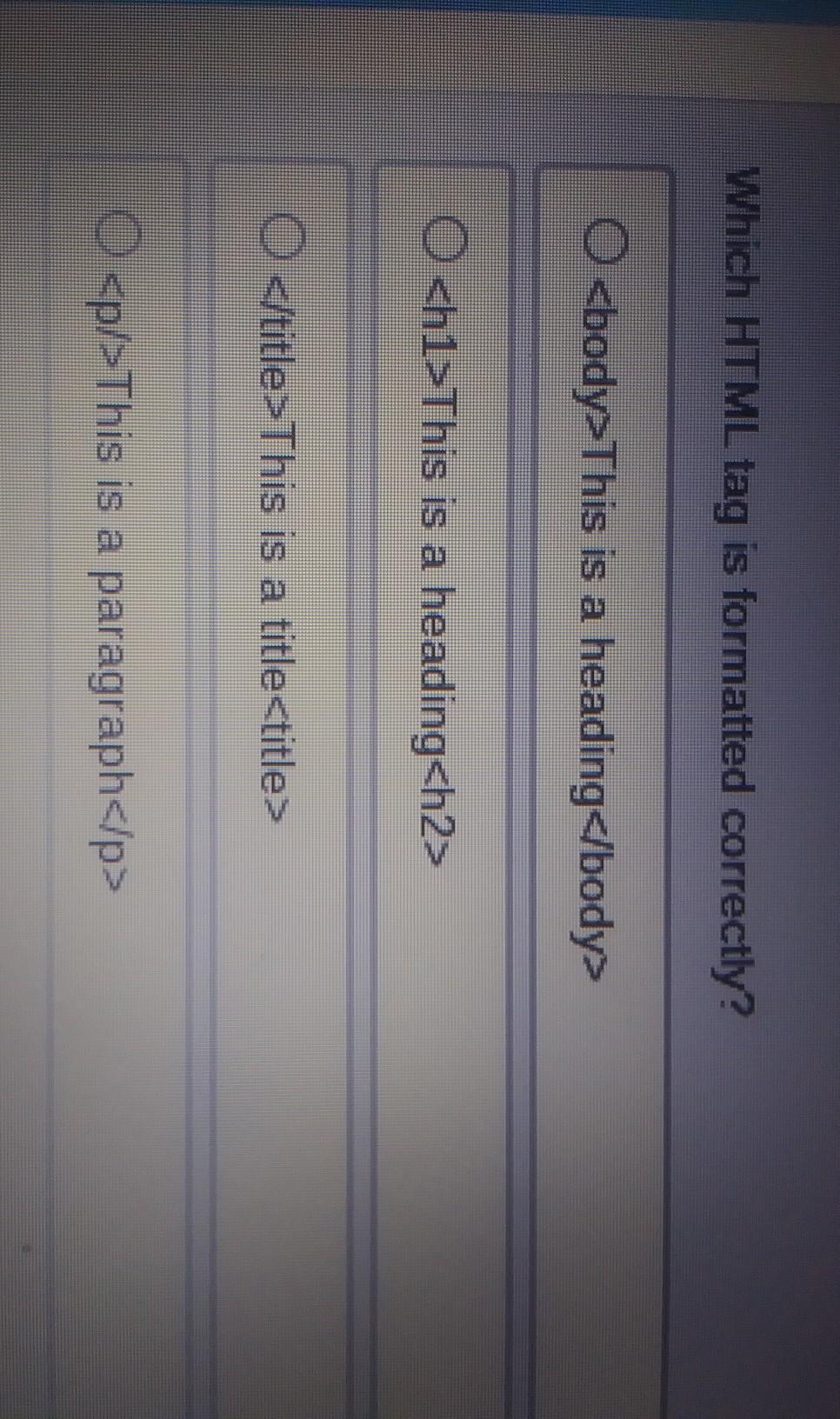
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
PLEASE HELP WILL MARK AS BRAINLIEST
Directions and Analysis
Task 1: Role of Computer Skills in an Industry
In this activity, you will understand the importance of computer skills in an industry by
completing the following tasks:
Select an industry of your choice. With the help of online research, explain how compute!
skills are necessary for the industry's management team.
Discuss how these skills are important in terms of planning, marketing, and use of financial
resources.
Discuss the ways in which a person should aim to upgrade their skills, and also discuss
why this process is of importance.
.
Answers
Answer:
Manufacturing
Explanation:
Planning. Data plots on all things and future plans as in if how much is bought what prices of stock you will have. Person could improve by taking courses in business planning.
Answer: Industry HealthCare
Explanation: Industry: Healthcare
Computer skills have become an integral part of healthcare management. The management team in the healthcare industry is responsible for managing day-to-day operations, financial resources, and planning for future growth. In order to accomplish these tasks effectively, computer skills are crucial.
Planning: Healthcare management team uses computer skills for strategic planning. Computer programs can analyze large amounts of data and provide useful insights for decision making. The team can analyze the current market trends, patient data, and financial data to make informed decisions.
Marketing: Marketing is an important aspect of the healthcare industry. The management team uses computer skills for targeted marketing campaigns. They can analyze the demographics of the patients and create marketing strategies that are tailored to meet their needs. Computer programs can also help in tracking the success of marketing campaigns and make necessary changes.
Financial Resources: Managing financial resources is critical for any industry, including healthcare. The management team uses computer skills for financial planning, budgeting, and forecasting. They can create financial reports that provide an overview of the financial health of the organization. Computer programs can also help in tracking expenses and revenue, which helps in identifying areas that need improvement.
Upgrading Skills: Healthcare professionals should aim to upgrade their computer skills regularly. The healthcare industry is constantly evolving, and new technologies are being introduced regularly. Professionals need to keep up-to-date with the latest software programs and technology. The upgrading process is important because it ensures that professionals are equipped with the necessary skills to perform their job effectively.
In conclusion, computer skills are essential for the management team in the healthcare industry. These skills are necessary for strategic planning, targeted marketing campaigns, and managing financial resources. Healthcare professionals should aim to upgrade their computer skills regularly to stay up-to-date with the latest technologies and software programs.
What would be printed to the screen when the following program is run?
function returnNumber() {
return x *5;
println(returnNumber(2));
Answers
Following are the correct Python program to calculate its output:
Program Explanation:
Defining a method "returnNumber" that takes "x" variable in the parameter.Inside the method, a return keyword is used that multiplies the parameter value by 5 and returns its value.Outside the method, a print method is declared that calls the "returnNumber" method which accepts an integer value into the parameter.Program:
def returnNumber(x):#defining a variable returnNumber that x variable in parameter
return x*5;#defining a return keyword that multiply the parameter value by 5
print(returnNumber(2))#calling method returnNumber that takes integer value in parameter
Output:
Please find the attached file.
Learn more:
brainly.com/question/13785329

write a function number in months that takes a list of dates and a list of months (i.e., an int list) and returns the number of dates in the list of dates that are in any of the months in the list of months. assume the list of months has no number repeated. hint: use your answer to the previous problem.
Answers
Simply said, a function is a "chunk" of code that you may reuse repeatedly rather than having to write it out several times.
What does computer function mean?
The following tasks are routinely performed by computers as part of their functions: obtaining, processing, returning, and storing data. Computer devices can be categorized as input devices, processing devices, output devices, and storage devices, in that order, to assist computer systems in carrying out these tasks.
Create a function called number in months that accepts an int list of dates and months and returns the number of dates in the dates list that are in any month in the months list.
dates: (int * int * int) list, months: int list, fun number in months = if null if months, 0 else number in months + number in months(dates, hd months) (dates, tl months)
To know more about functions visit:
https://brainly.com/question/13733551
#SPJ4
Which statement is true? Select 3 options.
1. Deques can be created empty.
2. Deques are lists.
3. Lists are deques.
4. Deques can contain lists.
5. A deque is a type of collection.
Answers
Answer:
2nd statement is True dear!!!
Answer:
Deques can contain lists.
A deque is a type of collection.
Deques can be created empty.
Explanation:
Answers can be found in Edge instructions
"You can make a deque whose members are lists."
"You can create an empty deque or create a deque with a list or a string."
"You have used lists and deques, which are two types of collections used by Python. "
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
Do you think that smart televisions are going to replace media players?
Answers
Answer:
yes because smart television give more information
he payroll department keeps a list of employee information for each pay period in a text file. the format of each line of the file is write a program that inputs a filename from the user and prints a report to the terminal of the wages paid to the employees for th
Answers
Following are the required code to make a report in tabular format by using the appropriate headers:
Python code:
file_name = input('Enter input filename: ')#defining a variable file_name that inputs file value
try:#defining try block that uses thr open method to open file
file = open(file_name, 'r')#defining file variable that opens file
except:#defining exception block when file not found
print('Error opening file ' , file_name)#print message
exit()#calling exit method to close program
print('{:<12s} {:>10s} {:>10s}'.format('Name', 'Hours', 'Total Pay'))#using print method to print headers
for l in file.readlines():#defining loop that holds file value and calculate the value
name, hour, wages = l.split()#defining variable that holds the value of file
hour = int(hour)#holiding hour value
wages = float(wages)#holiding wages value
total = hour * wages#defining variable total variable that calculates the total value
print('{:<12s} {:>10d} {:>10.2f}'.format(name, hour, total))#print calculated value with message
file.close()#close file
Required file (data.txt) with the value:
Database 34 99
base 30 90
case 34 99
What is code explanation?Defining the variable "file_name" that uses the input method to input the file name with an extension. Using the exception handling to check the file, with using the try block and except block. In the try block check file, and in except block print message with the exit method when file not found. In the next line, a print method has used that prints the header and uses a loop to read the file value. Inside the loop, a header variable is used that splits and holds the file value, calculates the value, prints its value with the message, and closes the file.
To know more about python code,
https://brainly.com/question/21888908
#SPJ4
Which of these technologies has been most used by terrorist organizations?
Group of answer choices
phishing
social media
cloud computing
encoding
Answers
Answer:
Phishing and Social Media
Explanation:
A quick web search can give you this information. Terrorist organizations have used social media to socially engineer innocent people into joining their organizations and more. Phishing is also an attack that's used to obtain critical information such as hashes or plaintext credentials to get into people's accounts. This is a tactic that's also been used by terrorist organizations in the past.
Which action would best help a school improve equity for its students?
O A. Provide classes on economics and investing
O B. Focus interventions on the students with disabilities
O C. Make the classes easier so everyone can get an A
O D. Provide all students with what they need to be successful
SUBMIT
Answers
D, the first two focus on two specific aspects and the third wouldn’t help i’m the long run.
it appears this account relationship is not online banking enabled
Answers
Check your options to make sure you didn't hide the account. Restart your browser after clearing your cookies and memory cache. After that, try logging back into your online bank. Ensure that the web browser you're using is compatible.
What does the relational bank account look like?The Relationship Bank Account (RBA) is remarkably similar to a bank checking account. You can put money into the relationship and strengthen it, or you can take withdrawals and make it weaker. Consistent investments made over a long period of time always result in a robust and healthy partnership.
What does a relationship account serve as?Relationship Banking: What Is It? Relationship banking is a tactic adopted by banks to increase client loyalty and offer a centralized point of contact for a variety of products.
To know more about cache visit:-
https://brainly.com/question/28232012
#SPJ1
of the following similar-sounding items, which one would you likely find on your keyboard?
Answers
Of the following similar-sounding items, the one that you likely find on your keyboard is Caret.
What is the symbol about?A symbol with many applications in mathematics and computer programming is the caret (). The caret stands for an exponent in mathematics, such as a square, cube, or other exponential power. For instance, 62 can also be used to symbolize 62.
Thus to use, Press and hold the Shift key while pressing the 6 key on your keyboard to make the caret symbol (Shift+6). Its visual resemblance to the caret used by the original proofreader to indicate where a punctuation mark, word, or phrase should be added into a document gave rise to the name "caret."
Learn more about keyboard from
https://brainly.com/question/26632484
#SPJ1
user downloads a widget onto his android phone but is puzzled to see that when the widget is touched an app is launched. what is a possible cause?
Answers
Answer:
Explanation:
A possible cause for the behavior where touching a widget on an Android phone launches an app could be that the widget is incorrectly configured or associated with the wrong app.
Widgets on Android devices are intended to provide quick access to specific functions or information without opening the full application. They are typically placed on the home screen or in a widget panel. When a user interacts with a widget, it should perform the designated action associated with that widget.
If touching a widget launches an app instead of performing the expected action, it suggests that the widget's configuration may be incorrect. The widget may be associated with the wrong app, resulting in the app being launched instead of the intended widget behavior.
To resolve this issue, the user can try the following steps:
1. **Remove and Re-add the Widget**: Remove the problematic widget from the home screen or widget panel and re-add it. This can sometimes refresh the widget's settings and resolve any misconfigurations.
2. **Check Widget Settings**: Some widgets have settings that allow customization of their behavior. The user should verify the widget's settings to ensure they are correctly configured for the desired action.
3. **Reinstall the Widget or App**: If the issue persists, uninstalling and reinstalling the widget or the associated app can help resolve any underlying software conflicts or issues.
4. **Contact App Developer**: If the problem continues, reaching out to the app developer or widget provider for support can provide further assistance in troubleshooting the issue.
It's important to note that the specific cause can vary depending on the widget, app, and device configuration. The steps above provide general guidance to address the issue of a widget launching an app instead of performing its designated action.
Learn more about widget here:
https://brainly.in/question/17825063
#SPJ11
write a python program to initialize the value of two variables then find sum
Answers
Answer:
JavaScript:
Let x = 10
Let y = 10
Console.log(x + y)
//outputs 20
C++:
Let x = 10
Let y = 10
The file is Math.cpp so,
std::cout << "" + y + "" + x
g++ Math.cpp -o Maths
./Maths
//Outputs 20
Answer:
#Ask the user for a number
a = int(input("Enter a number: "))
#Ask the user for a number
b = int(input("Enter a number: "))
#Calculate the sum of a and b
sum = a + b
#print the ouput
print(str(a) + " + " + str(b) + " = " + str(sum))
43. What are the three major ways of authenticating users? What are the pros and cons of each approach?
Answers
The three major ways of authenticating users are:Password-based authentication,Two-factor authentication,Public key infrastructure (PKI) authentication.
Password-based authentication: This is the most common form of authentication, where a user provides a username and a password to prove their identity. The password is compared to the stored password for that user, and if it matches, the user is authenticated.
Pros:
It is easy to implement and use.
It is familiar to most users.
It can be used in various systems and applications.
Cons:
Passwords can be guessed or stolen.
Users tend to use weak passwords, reuse passwords across multiple accounts, and write them down, making them vulnerable to attacks.
Passwords can be intercepted during transmission, if the communication is not properly secured.
Two-factor authentication (2FA): In this method, the user is required to provide two different forms of authentication to prove their identity. This can be a combination of something the user knows (such as a password), something the user has (such as a token or a smart card), or something the user is (such as biometric data).
Pros:
It adds an extra layer of security to the authentication process.
It is more difficult to bypass or circumvent than password-based authentication.
It can prevent unauthorized access even if the password is compromised.
Cons:
It can be more difficult and expensive to implement and maintain.
It can be inconvenient for users to carry and use the additional authentication factor.
Some 2FA methods (such as SMS-based authentication) can be vulnerable to attacks.
Public key infrastructure (PKI) authentication: This method uses digital certificates and a public key infrastructure to authenticate users. Each user has a public-private key pair, and a certificate authority (CA) issues digital certificates that link the user's identity to their public key.
Pros:
It provides strong authentication and encryption capabilities.
It can be used in a wide range of applications, such as secure email, web browsing, and e-commerce.
It can be used for non-repudiation (i.e., to prove that a user sent a message or made a transaction).
Cons:
It can be complex to set up and manage.
It requires a trusted third party (the CA) to issue and manage the digital certificates.
It can be vulnerable to attacks if the private key is compromised.
Overall, each authentication method has its own strengths and weaknesses, and the appropriate method depends on the level of security required, the usability needs, and the specific context of the system or application. It is often recommended to use a combination of different authentication methods to achieve a higher level of security.
Learn more about Two-factor authentication here:https://brainly.com/question/28398310
#SPJ11
Stephen is slowing down as he approaches a red light. He is looking in his mirror to switch lanes and misjudges how close Keisha's car is, rear-ending her car. When
they get out and assess the damage, Keisha's bumper will need to be replaced. What type(s) of insurance could Stephen use to cover this accident? Explain.
Krisha had some discomfort in her neck at the time of the accident but thought it was minor and would go away. A week or so after the accident, Keisha finally goes
What t) of insurance could Keisha use to cover this accident?
Answers
The type of insurance that Stephen could use to cover this accident is known as liability coverage
What t) of insurance could Keisha use to cover this accident?The insurance that Keisha could use to cover this accident is personal injury protection.
In the case above, The type of insurance that Stephen could use to cover this accident is known as liability coverage as damage was one to his property.
Learn more about Property Damage from
https://brainly.com/question/27587802
#SPJ1
a windows user called the help desk to request that their local user account password be reset on their computer. the help desk technician connected to the computer using rdc and reset the password using the network places wizard. after the password was reset, the user lost access to all the data files on the local hdd. what is the most likely reason for the lost data files? question 17 options: a) the technician erased all the data files while resetting the password. b) the user had previously encrypted their data files and folders using efs. c) the user lost access to the network shared drive when their password was reset. d) the user attempted to enter an incorrect password too many times.
Answers
The most likely reason for the lost data files after the help desk technician reset the password for the Windows user's local account is that the user had previously encrypted their data files and folders using EFS.
Encrypting File System (EFS) is a feature in Windows that allows users to encrypt files and folders to protect them from unauthorized access. When a user encrypts a file or folder using EFS, only they or someone with their encryption certificate can access it. If the user forgets their password or loses their encryption certificate, they may not be able to access their encrypted files and folders.
In this scenario, when the help desk technician reset the user's password using the network places wizard, it may have also reset the user's encryption certificate, which would have resulted in the user losing access to their encrypted data files. The technician may not have been aware that the user had encrypted their files and folders using EFS and inadvertently reset the encryption certificate along with the password.
Therefore, the most likely reason for the lost data files is that the user had previously encrypted their data files and folders using EFS. To prevent this from happening in the future, the help desk should verify if the user has encrypted any files and folders using EFS before resetting their password and take appropriate steps to ensure that the user does not lose access to their encrypted data.
For more such question on encrypted
https://brainly.com/question/20709892
#SPJ11
By default, pivottables display __________ data for each category. However, you may want to set a filter to exclude particular categories or values.
Answers
By default, pivot tables display the summarized data for each category. This means that the data displayed is an aggregate of all the values within a particular category.
For example, if we have a pivot table with categories of different products and their corresponding sales figures, the default display will show the total sales for each product. However, there may be instances where we want to exclude particular categories or values from our pivot table. For example, we may want to exclude a particular product that is not relevant to our analysis or exclude any zero values from our table. To achieve this, we can set a filter on our pivot table.
Filters enable us to exclude particular categories or values based on specific criteria. For instance, we can filter our pivot table to show only products with sales above a particular threshold or exclude products that have zero sales. We can also filter by date ranges, regions, or any other category that we have in our pivot table.
To set a filter on our pivot table, we can click on the filter icon located at the top of the category column, select the categories or values we want to exclude, and click on OK. Our pivot table will update automatically to show the filtered data.
In summary, pivot tables by default display summarized data for each category, but we can set filters to exclude particular categories or values based on specific criteria.
To know more about pivot table visit:
https://brainly.com/question/30543245
#SPJ11
The option to send a publication in an e-mail is available in the _____ tab.
File
Home
View
Review
Answers
Answer:
File
Explanation:
After teaching a group of students about the indications for use for aminoglycosides, the instructor determines that the teaching was successful when the students identify which type of infection as a primary indication
Answers
It is also essential that you do not drink milk within two hours (either before or after) of carrying tetracycline. This is because both food and milk can reduce the amount of medicine absorbed by your body, making it less useful in fighting infection. The tablets can cause throat tingle
What are the 4 types of infections?
The four different classifications of infectious agents are bacteria, viruses, fungi, and parasites. When studying these agents, researchers separate them using certain characteristics: Size of the spreading agent
What is disease and its types?
Infection happens when germs enter your body and multiply, resulting in disease. The four main kinds of infections are viral, bacterial, fungal, and parasitic.
To learn more about Infection, refer
https://brainly.com/question/25258835
#SPJ4
Which CSS declaration makes the child of the paragraph blue?
This will be the blue paragraph.
a. p > span { color: blue;}
b. p ~ span { color: blue;}
c. p + span { color: blue;}
d. p < span { color: blue;}
Answers
The CSS declaration that makes the child of the paragraph blue is: a. p > span { color: blue;}.
Explanation: Given options are:a. p > span { color: blue;}b. p ~ span { color: blue;}c. p + span { color: blue;}d. p < span { color: blue;}Here, p > span means that any child of `` tags with `` tags will have the color blue. So, Option a is the correct answer. The symbol > is known as child selector which selects all the direct child elements specified with the second element. Here, p is the parent selector and span is the child selector which means that the code p > span applies to any span element that is a direct child of a p element.
An ordered group of CSS values and properties makes up a CSS declaration block. It appears as a CSSStyleDeclaration in the DOM.
Every set of properties and values is referred to as a CSS declaration. These properties are linked to the CSS declaration block:
derived flag
If the CSSStyleDeclaration object is a computed style as opposed to a given style, it is set. By default, unset.
declarations
The associated CSS declarations for this item.
CSS parent rule
The CSSRule that the block of CSS declaration belongs to, unless null.
node owner
The element to which the CSS declaration block is attached; if null, the element.
modifying flag
Sets the time at which the owner node's style attribute is updated by the CSS declaration block.
Know more about CSS here:
https://brainly.com/question/32535384
#SPJ11
Zoom was identified as a unicorn in the case. A unicorn is a:.
Answers
Zoom was identified as a unicorn in the case. A unicorn is option C: a private company worth $1 billion or more.
What is the unicorn about?Within the setting of commerce and fund, a unicorn alludes to a secretly held startup company that has accomplished a valuation of over $1 billion.
Zoom is additionally a well-known unicorn company that gives video conferencing computer program and other communication devices. In 2020, Zoom was esteemed at over $100 billion, making it one of the foremost profitable unicorns within the world.
Learn more about unicorn from
https://brainly.com/question/24667141
#SPJ1
Zoom was identified as a unicorn in the case. A unicorn is a Multiple Choice private equity firm investing $1 billion or more into a start-up company. O foreign company entering into the United States with no local investment in capital. private company worth $1 billion or more. O tech startup company with over a million users. о company with an IPO that gains at least 50 percent on opening day.
explain the verbal method of communication
Answers
Answer:
verbal method of communication means using kaomji, emojis gifs and stickers although you know how to use the keyboard.
Answer:
The Verbal Communication is a type of oral communication wherein the message is transmitted through the spoken words. Explanation: Here the sender gives words to his feelings, thoughts, ideas and opinions and expresses them in the form of speeches, discussions, presentations, and conversations.
which of the following is not true about column-family nosql databases? o a. column family databases organize their data into column families. o b. each column can be part of multiple column families. o c. data for a specific column family is stored together on disk to optimize disk input/output operations. o d. columns are dynamically created upon insertion of new data.
Answers
Each column cannot be part of multiple column families in case of column-family nosql databases.
What do you mean by No-sql databases?NoSQL databases, also referred as "not merely SQL," are non-tabular databases that store data in various ways from relational tables. Depending on their data model, NoSQL databases can be classified as several categories. The primary types include wide-column, graph, document, and key-value. With a lot of data and a lot of users, they scale well and offer customizable schemas.
There are distinct qualities seen in every NoSQL database. High-level characteristics of several NoSQL databases include:
Adaptable modelsHorizontal scalingThe data model allows for quick queries.Ease of use for developersFour main categories of NoSQL databases have developed over time:
document databaseskey-value databaseswide-column storesgraph databasesTo learn more about databases refer to:
https://brainly.com/question/518894
#SPJ1
_____ are software systems designed to support interoperable machine-to-machine interaction over a network.
Answers
Answer:
A Web service
Explanation:
A Web service is a software system designed to support interoperable machine-to-machine interaction over a network. It has an interface described in a machine-processable format
Can anyone help me on assignment 8: personal organizer on edhesive?
Answers
Open the PDF attached and it has the code I used to answer it. It got me 100%. Hope it works for you <3
A school is developing a program to keep track of information about students and their class schedules. In which of the following instances would a data abstraction be most helpful?
Answers
Answer:
A data abstraction would be most helpful in the instance where the school is developing a program to keep track of information about students and their class schedules. This is because data abstraction allows for the hiding of complex implementation details and the manipulation of data through a simplified interface. This allows the program to be more organized and efficient, as well as easier for users to understand and interact with. In this case, data abstraction can be used to create a user-friendly interface for entering and viewing student information and class schedules, while also ensuring that the underlying data is stored and processed in a consistent and secure manner.
A data abstraction would be most helpful in the instance where the school is developing a program to keep track of information about students and their class schedules.
What does the Data abstraction?Data abstraction has been allows for the hiding of the complex implementation as well as the details and the manipulation of data through the simplified interface. This has allows the program to be more organized along with the efficient.
It is easy for the users to understand and interact with. In this case, data has abstraction which can be used to create a user-friendly interface for the entering as well as viewing the student information and the class schedules, while it has also ensuring that the underlying data has been stored and processed in the consistent and the secure manner.
Data abstraction has been the process of reducing the specific set of the data to a condensed illustration of the total. Generally, abstraction has the process of the stripping something of its characteristics in order to reduce it to its core components.
Therefore, A data abstraction would be most helpful in the instance where the school is developing a program to keep track of information about students and their class schedules.
Learn more about data abstraction on:
https://brainly.com/question/30626835
#SPJ2
The third finger on the left hand types _____.
7 U J M
3 E D C
8 I K ,
1 Q A Z
Answers
Answer:
3 E D C
Explanation:
Note that there are typically a outdent on the "f" key and "j" key, which are used by your pointer fingers. The "f" key is the one pressed by your left hand, and next to your pointer finger is your third finger, which rests on the key "d". Since only one answer has the "d" option, then it is your answer.
There is obviously some differences, and not everybody may type as such. However, I personally use that finger to type "e", "d", & "c", and so it should be your answer choice.
~
you have recently installed windows server 2016 desktop experience on a server. your manager informs you that he needs to extensively use the command line and powershell. he also does not want the graphical interface. what should you do to meet his requirements? [choose two that apply]
Answers
To meet your manager's requirements, you can take the following steps:
Uninstall the desktop experience feature: The desktop experience feature provides a graphical user interface (GUI) on Windows Server, which your manager doesn't want. You can uninstall this feature by running the following PowerShell command as an administrator:
Uninstall-WindowsFeature Server-Gui-Shell -Restart
This will remove the desktop experience feature and reboot the server.
Install the Windows Server Core mode: The Windows Server Core installation provides a command-line interface with no GUI, which is suitable for your manager's needs. You can install this mode by running the following PowerShell command as an administrator:
Install-WindowsFeature ServerCore
This will install the Windows Server Core mode, which only includes the command-line interface and essential system components.
Note: Before making any changes to a production system, it is recommended to test the changes in a non-production environment. Also, make sure to communicate with your manager and obtain approval before making any changes to the server.
For more such question on interface
https://brainly.com/question/30390717
#SPJ11