The software crisis is aggravated by the progress in hardware technology?"" Explain with examples
Answers
The software crisis refers to the difficulties and challenges associated with developing and maintaining complex software systems. These challenges include issues related to software quality, productivity, cost, and reliability.
Hardware technology has been advancing rapidly over the years, with newer and more powerful computers, processors, and devices being introduced regularly. While these advancements have made it possible to build more complex and sophisticated software systems, they have also contributed to the software crisis in several ways.
Firstly, the progress in hardware technology has raised expectations for software performance and functionality. As hardware becomes more powerful, users and stakeholders expect software to make better use of the available resources and deliver faster, more reliable, and more feature-rich applications. This puts pressure on software developers to keep up with hardware advancements and build software that can leverage the latest hardware capabilities.
Secondly, hardware technology has made it easier to build complex software systems, but it has also made them more difficult to maintain and upgrade. With hardware advancements, software systems have grown in size and complexity, making them harder to debug, test, and update. This leads to maintenance issues and creates a situation where software systems become increasingly difficult to modify or extend.
Finally, hardware technology has also contributed to the proliferation of software systems, leading to a situation where organizations have to manage multiple software applications, platforms, and technologies. This has led to compatibility issues, integration challenges, and a lack of standardization, all of which contribute to the software crisis.
In summary, while hardware technology has enabled the development of more powerful and sophisticated software systems, it has also exacerbated the software crisis by raising expectations for software performance, making software systems more complex and difficult to maintain, and creating compatibility and integration challenges.
Learn more about technology visit:
https://brainly.com/question/30247796
#SPJ11
Related Questions
Visual servoing using spherical projection model: the inverse projection onto the unit sphere can be obtained from the unified model equation by:
X
s
=λ(x,y,1−
λ
ξ
)
λ=
1+x
2
+y
2
ξ+
1+(1−ξ
2
)(x
2
+y
2
)
a. Give the equation that links the 3D point coordinates and those for its projection onto a unit sphere b. Determine the interaction matrix related to the coordinates of the projection of 3D point onto unit sphere c. Consider that you have two different projected points onto the unit sphere. Compute the interaction matrix related to their inner product d. What could you conclude?)
Answers
(a) The equation linking the 3D point coordinates (x, y, ξ) and its projection onto a unit sphere (Xs) is Xs = λ(x, y, 1 - λξ), where λ is determined by the expression λ = 1 / (1 + x^2 + y^2).
(b) The interaction matrix related to the coordinates of the projection of a 3D point onto the unit sphere can be derived by differentiating the equation with respect to the point coordinates. It can be represented as a 3x3 matrix.
(c) To compute the interaction matrix related to the inner product of two different projected points onto the unit sphere, we differentiate the equation of the inner product with respect to the coordinates of the projected points. This will result in a 1x3 matrix.
(d) From the obtained interaction matrix in part (c), we can conclude how changes in the coordinates of the projected points on the unit sphere affect the inner product.
(a) The equation Xs = λ(x, y, 1 - λξ) describes the relationship between the 3D point coordinates (x, y, ξ) and its projection onto a unit sphere (Xs). The value of λ is determined by the expression λ = 1 / (1 + x^2 + y^2).
(b) The interaction matrix related to the projection of a 3D point onto the unit sphere can be obtained by differentiating the equation Xs = λ(x, y, 1 - λξ) with respect to the point coordinates (x, y, ξ). This results in a 3x3 matrix that captures the relationship between the changes in the 3D point coordinates and the changes in the projected point coordinates on the unit sphere.
(c) To compute the interaction matrix related to the inner product of two different projected points on the unit sphere, we differentiate the equation for the inner product with respect to the coordinates of the projected points. This will yield a 1x3 matrix that represents the interaction between the changes in the coordinates of the projected points.
(d) The obtained interaction matrix in part (c) provides insights into how changes in the coordinates of the projected points on the unit sphere affect the inner product. By analyzing the matrix elements, we can determine the sensitivity of the inner product to variations in the projected point coordinates and understand the geometric relationship between the points on the unit sphere.
learn more about 3D point coordinates here
https://brainly.com/question/29791404
#SPJ11
For a Python program that reads every third integer in a list, which arguments of the range function should you specify?
A start, a stop, and a step argument
A start and a stop argument
No arguments
One stop argument
Answers
Answer:
A start, a stop, and a step argument
Explanation:
the range function takes three arguments: a start, a stop, and a step.
What does Shu from the Shuhari developmental master model roughly translate to in English?
Answers
Shu from the Shuhari developmental master model roughly translates to "obeying and following traditional teachings" in English, It refers to the stage where the student learns the fundamentals and masters the techniques and principles of the art form under the guidance of a teacher or mentor.
The Shuhari developmental master model is a framework used in traditional Japanese martial arts to describe the stages of learning and mastery. The model is divided into three stages: Shu, Ha, and Ri. In the Shu stage, the student is focused on learning the fundamental techniques and principles of the art form.
This involves closely following the traditional teachings and methods of their teacher or mentor. The student aims to master the basics of the art form, and their movements and actions are often closely guided and supervised by their teacher.
Learn more about master model : https://brainly.com/question/30769904
#SPJ11
if a web server is down (such as powered off), the server may return a page saying to please try again later. group of answer choices true false
Answers
The correct answer is True.
When a web server is down or powered off, it is unable to process incoming requests and serve web pages. In such cases, it is common for the server to return an error page or message to the user indicating that the server is currently unavailable and to try again later. This is a standard practice to inform users about the temporary unavailability of the server and to manage their expectations.
The specific error page or message may vary depending on the configuration of the web server or the application running on it. The purpose of such messages is to provide a clear indication to users that the server is experiencing issues and that they should attempt to access the website or service at a later time when the server is back online or operational.
Therefore, it is true that when a web server is down, it may return a page asking users to try again later.
To know more about web server, visit:
https://brainly.com/question/32221198
#SPJ11
Which of the following correctly describes how sharing and NTFS permissions work?
a. When a file is accessed over the network, sharing permissions are checked first.
b. When a file is accessed interactively, only sharing permissions are checked.
c. When both sharing and NTFS permissions are applied, the least restrictive permissions
apply.
d. Sharing permissions can be assigned to separate files.
Answers
The correct statement that describes how sharing and NTFS permissions work is: c. When both sharing and NTFS permissions are applied, the least restrictive permissions apply.
How does the NTFS permissions work?When a file is opened from another computer, it is checked to see if the person has permission to access it. There are two ways that this is checked, sharing permissions and NTFS permissions.
The permissions that work the best are figured out by bringing together the permissions from both places. Then, the permissions that are least strict are used. When there is a disagreement between sharing and NTFS permissions, the one that allows more access will be used.
Learn more about NTFS permissions from
https://brainly.com/question/14178838
#SPJ4
This method removes the appropriate number of cells from the board. It does so by randomly generating (row, col) coordinates of the board and setting the value to 0 . Note: Be careful not to remove the same cell multiple times. A cell can only be removed once. This method should be called after generating the Sudoku solution. generate_sudoku Note: This is a function outside of the SudokuGenerator class. This function should also be implemented in sudoku_generator.py as it interacts with the class. Given size and removed, this function generates and returns a size-by-size sudoku board. The board has cleared removed number of cells. This function should just call the constructor and appropriate methods from the SudokuGenerator class. Cell This class represents a single cell in the Sudoku board. There are 81 Cells in a Board. draw(self) Draws this cell, along with the value inside it. If this cell has a nonzero value, that value is displayed. Otherwise, no value is displayed in the cell. The cell is outlined red if it is currently selected. Board This class represents an entire Sudoku board. A Board object has 81 Cell objects. sketch(self, value) Sets the sketched value of the current selected cell equal to user entered value. It will be displayed at the top left corner of the cell using the draw() function. place_number(self, value) Sets the value of the current selected cell equal to user entered value. Called when the user presses the Enter key. find_empty(self) Finds an empty cell and returns its|row and col as a tuple (x,y). check_board(self) Check
Answers
The method mentioned in the question is used to remove a specific number of cells from a Sudoku board by randomly generating (row, col) coordinates and setting the value at that cell to 0. This is done to create a partially filled Sudoku board that can be solved by the user.
The generate_sudoku function should call the appropriate methods from the SudokuGenerator class and return a size-by-size Sudoku board with the specified number of cells removed.
The Cell class represents a single cell on the Sudoku board and has a draw function that displays the value inside the cell. The Board class represents the entire Sudoku board and has 81 Cell objects. The sketch function sets the sketched value of the current selected cell equal to the user entered value, which is displayed at the top left corner of the cell using the draw function.
The place_number function sets the value of the current selected cell equal to the user entered value and is called when the user presses the Enter key. The find_empty function is used to find an empty cell and return its row and column as a tuple. The check_board function is used to check if the current Sudoku board is valid.
Learn more about SudokuGenerator here:
https://brainly.com/question/31190410
#SPJ11
Define a class Sphere to input radius of a sphere and compute the volume of it. Volume = πr3 (where π=3.14)
Answers
Lets use Python
Program:-
\(\tt r=(float(input("Enter\:the\:radius\:of\:Sphere=")))\)
\(\tt V=4/3*3.14*r**3\)
\(\tt print("Volume\:of\:the\:sphere=",V)\)
Output:-
\(\tt Enter\:the\:radius\:of\:the\:sphere=3\)
\(\t Volume\:of\:the\:Sphere=103.4\)
In this last step of initiation phase, projects are (blank). At this stage, the project is (blank) with projects that are running.

Answers
Answer:
Approved; compared.
Explanation:
Project management can be defined as the process of designing, planning, developing, leading and execution of a project plan or activities using a set of skills, tools, knowledge, techniques and experience to achieve the set goals and objectives of creating a unique product or service.
Generally, projects are considered to be temporary because they usually have a start-time and an end-time to complete, execute or implement the project plan.
Furthermore, the main purpose of project management is working toward a common goal.
This ultimately implies that, project managers should ensure adequate attention and time is taken to identify, analyze and manage capital, raw materials, people, system of tasks and other resources, so as to effectively and efficiently achieve a common goal with all project stakeholders.
The fundamentals of Project Management includes;
1. Project initiation
2. Project planning
3. Project execution
4. Monitoring and controlling of the project.
5. Adapting and closure of project.
In the last step of an initiation phase, projects are approved for execution. Also, at this stage, the project is compared with projects that are running or already being executed.
In conclusion, it is very important and essential that project managers in various organizations, businesses and professions adopt the aforementioned fundamentals in order to successfully achieve their aim, objectives and goals set for a project.
____ attacks consume the limited resources of a computer or a network by transmitting a large number of packets as quickly as possible.
Answers
The type of attacks that consume the limited resources of a computer or a network by transmitting a large number of packets as quickly as possible are known as Denial of Service (DoS) attacks.
This type of attack involves overwhelming a targeted computer or server with traffic from various sources, making it difficult for the device to process and respond to legitimate requests. DoS attacks can be initiated using a wide range of methods, such as flooding a server with traffic, crashing the server, or exploiting the device's resources to shut it down or prevent it from functioning correctly.Distributed Denial of Service (DDoS) attacks are a variation of DoS attacks.
In these attacks, the attacker uses multiple devices (usually compromised computers, smartphones, or other connected devices) to flood the targeted server or network with traffic from different sources. DDoS attacks are usually more potent than regular DoS attacks because they can generate a higher volume of traffic and be more challenging to trace and mitigate. DDos attacks can cause severe damage to an organization, such as data loss, revenue loss, and reputational damage. Organizations can mitigate these types of attacks by implementing security measures such as firewalls, intrusion prevention systems, and anti-DDoS solutions.
Learn more about Transmitting here,What is an advantage of transmitting information using digital signals?
OA. Digital signals send information very quickl...
https://brainly.com/question/28160561
#SPJ11
write a program that asks the user for the name of a file. the program should display the number of words that the file contains. with tokenizer
Answers
Here's a Python program that uses a tokenizer to count the number of words in a file based on user input:
import nltk
nltk.download('punkt')
def count_words(filename):
try:
with open(filename, 'r') as file:
contents = file.read()
tokenizer = nltk.tokenize.word_tokenize(contents)
word_count = len(tokenizer)
print("The file '{}' contains {} words.".format(filename, word_count))
except FileNotFoundError:
print("File '{}' not found.".format(filename))
# Prompt user for the file name
file_name = input("Enter the name of the file: ")
count_words(file_name)
The program uses the NLTK library's word_tokenize() function to tokenize the contents of the file into words. It then counts the number of tokens to determine the word count and displays the result. If the file is not found, it handles the FileNotFoundError exception and provides an appropriate error message.v
To learn more about tokenizer click on the link below:
brainly.com/question/30141272
#SPJ11
assume you run the __________ command on a computer. the command displays the computer's internet protocol
Answers
Assuming you run the ipconfig command on a computer, the command displays the computer's Internet Protocol. Here's a long answer explaining it:IPCONFIG command:IPCONFIG (short for Internet Protocol Configuration) is a command-line tool used to view the network interface details and configuration of TCP/IP settings.
It displays the computer's current configuration for the Network Interface Card (NIC). It also shows whether DHCP is enabled or disabled, IP address, Subnet Mask, and the Default Gateway, as well as DNS server details, and more.TCP/IP Settings:TCP/IP stands for Transmission Control Protocol/Internet Protocol, and it is the protocol suite used for internet communication. Every computer on the internet has an IP address, which is a unique numeric identifier that is used to send data to a specific device over the internet.
A Subnet Mask determines which part of the IP address is used to identify the network and which part identifies the specific device. The Default Gateway is the IP address of the router that the computer uses to connect to other networks. Lastly, DNS (Domain Name System) servers translate human-readable domain names into IP addresses, making it easier for users to remember website addresses.Along with IP address details, the ipconfig command displays other useful network details such as network adapters present on the device, link-local IPv6 addresses, the MAC address of the adapter, and more.
To know more about command visit:
brainly.com/question/27962446
#SPJ11
Assuming that you run the command on a computer that displays the computer's Internet Protocol (IP) address, the command is ipconfig.
Therefore, the answer is ipconfig. An IP address is an exclusive number linked to all Internet activity you do. The websites you visit, emails you send, and other online activities you engage in are all recorded by your IP address.
IP addresses can be used for a variety of reasons, including determining the country from which a website is accessed or tracking down individuals who engage in malicious online activities.
To know more about displays visit:-
https://brainly.com/question/33443880
#SPJ11
match the following of computer
Answers
This is a human-made physical system.
ecosystem
health care system
bicycle
school system
Answers
the answer is health care system
please help me also
1. For loop is used for repeating over a sequence, that is either a ___________ or _________________
Answers
Answer:
For loop is used for repeating over a sequence, that is either a list, tuple, dictionary, or a set.
All of the following are true about in-database processing technology EXCEPT Group of answer choices it pushes the algorithms to where the data is. it makes the response to queries much faster than conventional databases. it is often used for apps like credit card fraud detection and investment risk management. it is the same as in-memory storage technology.
Answers
All of the aforementioned are true about in-database processing technology except: D. it is the same as in-memory storage technology.
What is an in-database processing technology?An in-database processing technology can be defined as a type of database technology that is designed and developed to allow the processing of data to be performed within the database, especially by building an analytic logic into the database itself.
This ultimately implies that, an in-database processing technology is completely different from in-memory storage technology because this used for the storage of data.
Read more on database here: brainly.com/question/13179611
#SPJ1
Disability benefits are provided to eligible workers pursuant to the:-National Labor Relations Act. -Family Medical Leave Act. -Social Security Act. -Occupational Safety and Health Act.
Answers
In accordance with the National Labor Relations Act, the Family Medical Leave Act, and the Social Security Act, qualifying workers are given access to disability payments.
The Defense Base Act (DBA) is what.The DBA is an expansion of the Longshore and Harbor Workers' Compensation Act (LHWCA), which offers employees of U.S. government contractors who work abroad disability compensation and medical benefits as well as death benefits to eligible survivors of employees. The DBA incorporates the LHWCA's provisions, with a few exceptions. You can find more details in the Longshore FAQs.
The Federal Employees' Compensation Act's provisions do not apply to an employee who is injured or killed while working in agriculture, domestic service, or any other type of casual employment.
To know more about Disability visit:-
https://brainly.com/question/30229877
#SPJ4
A _____ is a grid that displays fields as columns and records as rows.
Answers
Answer: it is a datasheet because data is like a a place to keep things in and you can organise that in many different way's
What are the attacks that can be made against a bluetooth device?
Answers
The various attacks against Bluetooth devices include: Bluejacking, Bluesnarfing, BlueBorne, BlueBugging.
1. Bluejacking: Bluejacking is an attack where an attacker sends unsolicited messages to a Bluetooth-enabled device, such as text messages or images. This is typically done for fun and does not cause significant harm.
2. Bluesnarfing: In Bluesnarfing, an attacker gains unauthorized access to a Bluetooth device and steals sensitive information, such as contacts, emails, and text messages. This is a more serious attack that can compromise user privacy.
3. BlueBorne: BlueBorne is a set of vulnerabilities that allows an attacker to take control of a Bluetooth-enabled device by exploiting its wireless communication capabilities. This can lead to data theft or even remote control of the device.
4. Bluebugging: Bluebugging is an attack where the attacker takes full control of a Bluetooth device by exploiting its security vulnerabilities. This can lead to eavesdropping on phone calls, unauthorized access to data, and even remote control of the device.
To protect your Bluetooth devices from these attacks, always use strong and unique passwords, turn off Bluetooth when not in use, and regularly update your device's firmware to the latest version.
Learn more about Bluetooth: https://brainly.com/question/13072419
#SPJ11
pa 11-3 (static) kooyman hardware sells a ladder. they had... kooyman hardware sells a ladder. they had 5 ladders at the start of the week but demand was for 6 ladders.
What was their fill rate for this ladder?
Answers
The fill rate for a product is the percentage of demand that is met with available inventory.
In this case, Kooyman Hardware had 5 ladders at the start of the week and demand was for 6 ladders. Since they did not have enough inventory to meet the entire demand, the fill rate would be:
(fill rate) = (quantity filled) / (demand) * 100%
(quantity filled) = 5 ladders (since that is all they had)
(demand) = 6 ladders
(fill rate) = 5/6 * 100% = 83.33%
Therefore, Kooyman Hardware's fill rate for this ladder was 83.33%.
For more questions like hardware visit the link below:
https://brainly.com/question/29857377
#SPJ11
E-mail is a special form of business communication.
is the set of rules that governs communication using e-mail.
Answers
Answer:
Your answer would be 'Netiquette ' .
Hope this helped you out :D
What are the benefits of using disk cleanup as part of regular maintenance on a computer? Check all of the boxes that apply.
Trash is emptied to clear space on the hard drive.
Files that are no longer needed are deleted to clear space and help the computer run faster.
Accumulated temporary files are deleted to help the computer run faster.
Unnecessary program files that may slow down the computer are deleted.
Answers
Answer:
all of the above
Explanation:
Answer:
Trash is emptied to clear space on the hard drive.
Files that are no longer needed are deleted to clear space and help the computer run faster.
Accumulated temporary files are deleted to help the computer run faster.
Unnecessary program files that may slow down the computer are deleted.
Explanation:
It's all of the above
__________ attribute specifies the height of the image.
Answers
Answer: The height attribute specifies the height of an image.
Explanation: Hope That Helps! (:
Describe in 2-4 sentences how you would select a function on a spreadsheet.
Answers
Answer:
Explanation:
You would call the capacity from the primary. At that point execute your own factors to it. When the capacity is in the cell, you can copy and after that paste it into another cell to do a similar capacity for that diverse scope of cells.
You would call the capacity from the primary. At that point execute your own factors to it. When the capacity is in the cell, you can copy and after that paste it into another cell to do a similar capacity for that diverse scope of cells.
What is spreadsheet?
A spreadsheet is a type of computer program used for organizing, calculating, analyzing, and storing data in tabular form. Spreadsheets were created as digital counterparts to traditional paper accounting spreadsheets.
The data entered into a table's cells is what the program uses to run. Each cell may include text, numeric data, or formula results that automatically calculate and display values based on the contents of neighboring cells.
Users of spreadsheets can change any stored value and watch the changes in calculated values. This enables quick investigation of numerous scenarios without the need for manual recalculation, making the spreadsheet helpful for "what-if" study.
Therefore, You would call the capacity from the primary. At that point execute your own factors to it. When the capacity is in the cell, you can copy and after that paste it into another cell to do a similar capacity for that diverse scope of cells.
To learn more about Spreadsheet, refer to the link:
https://brainly.com/question/8284022
#SPJ3
in what century was plastic invented ?
Answers
in the year 1907 plastic was invented
working on a python assignment, not sure what i did wrong can anyone help?

Answers
Answer:
Explanation:
line 13 should be changed to:
print(“Item 1: “ + item1 + “ - $” + str(float(const1)))
You cannot concatenate a string to float type.
how do you play pokemon go
Answers
Answer:
download the app then tap your screen for the rest of your life
(And I'm being serious)
Lee finishes entering all the data. Next, he wants to format the header row so it is easier to read and stands out from the rest of the table. What should Lee do to accomplish this task?
Answers
Answer:
A: Add shading to the top row
B: Change the style of the table
Explanation:
Just got the question myself and got the answer from it
Answer:
A B
Explanation:
i just did the assignment└|∵|┐♪
Some one help pls will mark brainless !!!!!
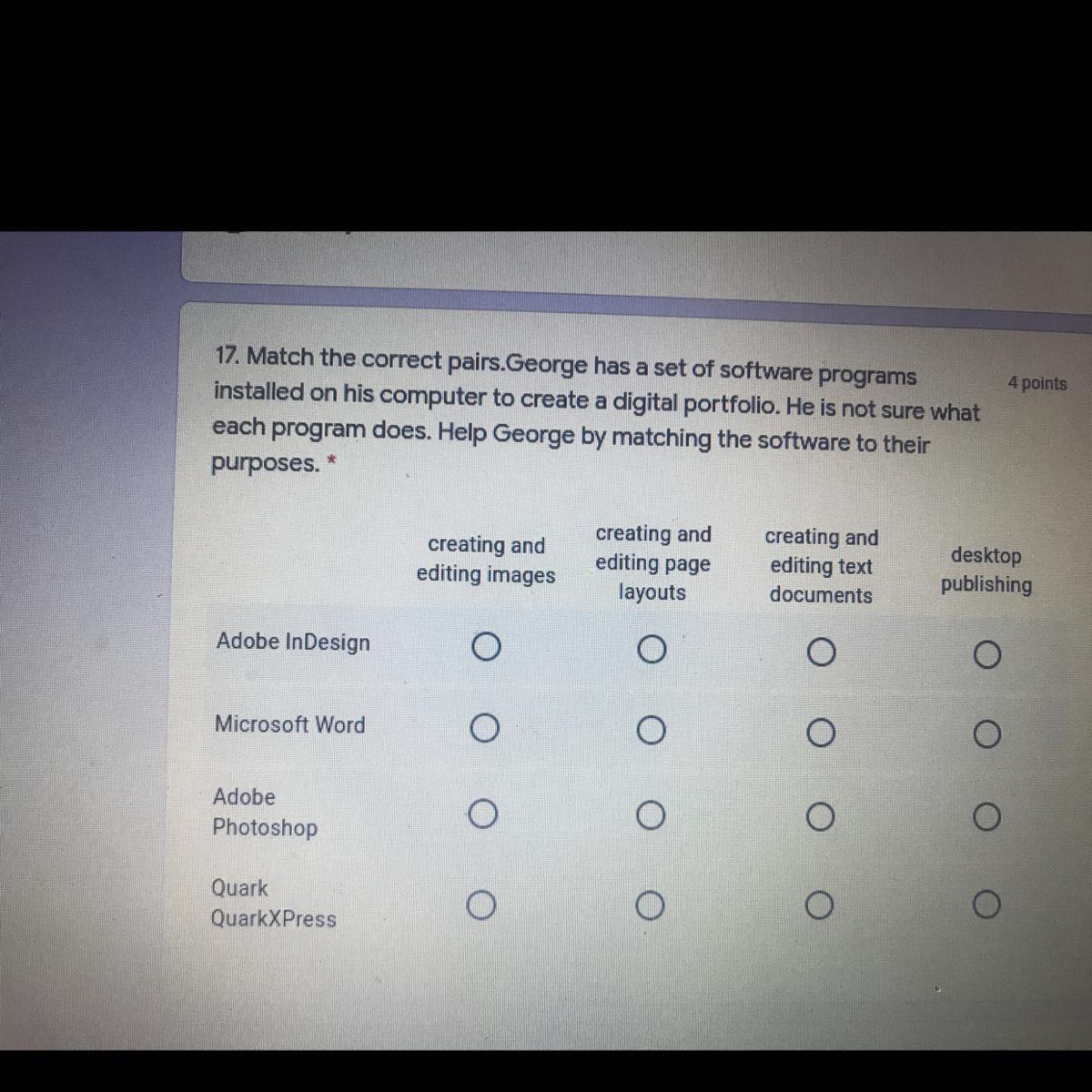
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
The __________ statement allows you to check for
multiple test expressions and execute different codes
for more than two conditions.
Answers
Answer:
B) nested if...else
Explanation:
In Computer programming, there are four (4) main types of statements used in the decision-making process and these are;
I. If statement.
II. If....else statement.
III. Else.....if statement.
IV. Nested if...else statement.
The nested if...else statement allows you to check for multiple test expressions and execute different codes for more than two conditions. It uses the other three (3) statements in its decision-making process.
However, only the first test expression would be executed when it is true and then the program is terminated. Otherwise, the program would continue to run until it gets to the breaking point (else statement) and then terminates.
Which statements describe front-end databases? Check all that apply. They can be used to store tables. They can be used to store forms. They can be used to store queries. They can be used to store reports. They are saved on a shared network folder. They are saved locally on users’ computers.
Answers
Answer
Explanation: these are the correct answer on the quiz
They can be used to store forms.
They can be used to store queries.
They can be used to store reports.
They are saved locally on users’ computers.