using python
Ask for and receive any number of integers from the user . you
should store these values in a list as integers
Answers
Here is an example of how we can do this in python:``#Ask user to input any number of integersnumbers =
[]while True: num = input("Enter an integer (press q to quit): ") if num == 'q': break try: num = int(num) except ValueError: print("Invalid input. Please enter an integer.") continue numbers.append(num)print(numbers)```
To ask for and receive any number of integers from the user, we can use the input function in python. This function allows us to accept user input from the console. We can create a loop to ask the user to enter a number, and then store each value in a list as integers. n the above code, we ask the user to input any number of integers by using a loop.
We accept the input using the input function, and then we check if the input is 'q'. If the input is 'q', we break out of the loop. If the input is not 'q', we try to convert the input to an integer using the int function. If the input cannot be converted to an integer, we ask the user to enter an integer again. If the input is an integer, we append it to the numbers list. Finally, we print the list of integers.
Learn more about python input function: https://brainly.com/question/25755578
#SPJ11
Related Questions
concerning self-reinforcement, which of the following statements is true? question 9 options: a) self-reinforcement leads to less life satisfaction. b) mildly depressed college students tend to frequently use self-reinforcement, rather than peer reinforcement. c) self-reinforcement is closely related to low self-esteem. d) self-reinforcement is similar to the psychoanalytical concept of the superego.
Answers
The right response is (b), which states that college students who are mildly depressed frequently employ self-reinforcement rather than peer reinforcement.
Self-reinforcement: What is it?In operant contexts, self-reinforcement mainly refers to setups where the subject delivers a consequence to himself based on his action. The definition of all other forms of reinforcement, it should be observed, makes their delivery dependent on the subject's behaviour.
What function does self-reinforcement serve?Students can change their emphasis to what they can do and approach even stressful situations with stronger coping mechanisms by using positive self-talk or self-reinforcements. Positive self-talk can boost motivation and self-esteem while also lowering anxiety, according to research.
To know more about self-reinforcement visit:-
https://brainly.com/question/12440506
#SPJ1
Karlie wants to eat a good breakfast before taking a test
Answers
Answer:C
Explanation:
What is the function of input device?
Answers
Answer:
The function of an input device is to communicate information to a computer or other sort of information processing equipment. Input devices are types of peripheral devices that communicate with processing units.
what is the approximate bandwidth of a 13-wpm international morse code transmission?A. 13 HZB. 26 HZC. 52 HZD. 104 HZ
Answers
The correct answer is International Morse code is a method of transmitting information through a series of dots and dashes that represent letters, numbers, and symbols.
To calculate the bandwidth of a 13-wpm Morse code transmission, we need to consider the frequency range of the dots and dashes, as well as the spacing between them. Morse code transmissions typically use a keying tone to indicate the start and end of each character, which is typically a square wave with a frequency of around 800 Hz. The dots and dashes themselves are usually modulated onto this tone by varying the duration of the keying signal. For a 13-wpm Morse code transmission, each character will take approximately 4.6 seconds to transmit (assuming a standard word length of 5 characters). The dots and dashes themselves are typically much shorter than this, lasting only a fraction of a second each. However, the keying tone and the spacing between characters also contribute to the overall bandwidth of the transmission. Based on these factors, the approximate bandwidth of a 13-wpm Morse code transmission is around 52 Hz. This takes into account the frequency range required to accurately transmit the keying tone, as well as the variations in duration between the dots, dashes, and spaces. It's worth noting that this is a relatively narrow bandwidth compared to many other forms of communication, such as voice or data transmissions, which typically require much higher bandwidths to transmit information accurately.
To learn more about transmission click on the link below:
brainly.com/question/14725358
#SPJ4
Consider the implementation of Dijkstra's algorithm in an SDN framework. Which of the following statements are true? (Hint: more than one statement is true.) a When executing, Dijkstra's algorithm will run as a network control application "on top on the SDN controller. b If a router's forwarding table should be changed as a result of running Dijkstra's algorithm, the new flow table for that router will be updated by the SDN controller via the southbound API using the Openflow protocol.
c When executing, Dijkstra's algorithm will need to send messages to all of the routers to gather their link costs.
d If a router's forwarding table should be changed as a result of running Dijkstra's algorithm, the implementation of Dijkstra's algorithm will determine the routers needing updated flow tables, and send the new flow tables to them directly using the OSPF protocol. e When executing, Dijkstra's algorithm will execute within the operating system of the SDN controller f When executing, Dijkstra's algorithm will use the link-state database that is maintained within the SDN controller.
Answers
The true statements regarding the implementation of Dijkstra's algorithm in an SDN framework are:
a) When executing, Dijkstra's algorithm will run as a network control application "on top on the SDN controller." This means that Dijkstra's algorithm is implemented as a software application that operates within the SDN controller, utilizing its capabilities for network control and management.
b) If a router's forwarding table should be changed as a result of running Dijkstra's algorithm, the new flow table for that router will be updated by the SDN controller via the southbound API using the OpenFlow protocol. This statement highlights the role of the SDN controller in updating the forwarding tables of routers based on the output of Dijkstra's algorithm.
c) When executing, Dijkstra's algorithm will need to send messages to all of the routers to gather their link costs. This step is essential for Dijkstra's algorithm to gather information about the link costs in the network, which is necessary for determining the shortest paths.
Know more about Dijkstra's algorithm here:
https://brainly.com/question/30767850
#SPJ11
What is the purpose of this diamond shape in a flowchart?
Answers
Answer:
To represent a decision making step.
Explanation:
for example, assume that you need to display 'pass' if the total marks are greater than 50 and 'fail' if it's less than 50
Then, after calculating the total, you should draw a diamond and inside it write, 'is total ∠ 50?'
after that you can continue your flowchart taking one decission as 'yes' and the other decission as 'no'
The rectangular shape stands for a task or course of activity. In the flowchart sequence, the diamond shape represents a question or a branch.
What is flowchart?A flowchart is a diagram that shows a process' individual steps in their proper order.
It is a general tool that may be customised for a wide range of uses and used to define a variety of processes, including a project plan, an administrative or service process, or a manufacturing process.
These four typical forms are excellent for outlining organisational structure, how various departments interact, and economic, industrial, or administrative operations.
In a process, a decision point is represented by a diamond. Usually, the statement in the symbol will call for a "yes" or "no" response and, in accordance, branch to other locations in the flowchart.
Thus, this is the main use of diamond symbol in a flowchart.
For more details regarding a flowchart, visit:
https://brainly.com/question/14598590
#SPJ2
CAn someone please vote me brainliest I don't even have one BRAINLY and can someone thanks me too!
Answers
Answer:
5 robuk now noob
Explanation: noob vs pro = pro wins
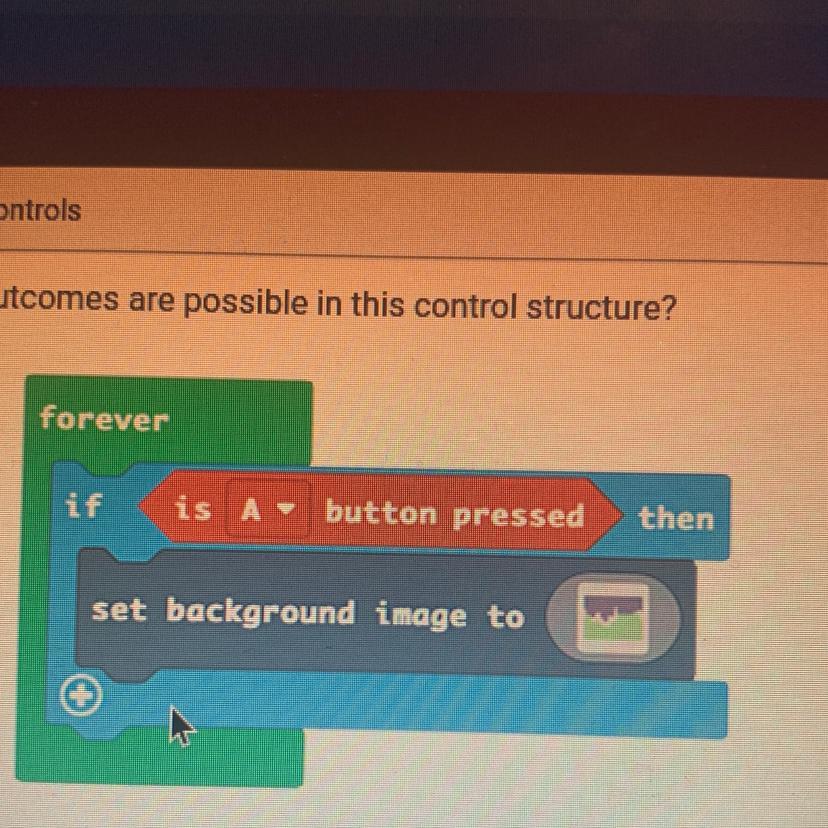
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
The Linux platform that runs on mobile phones is called:
a.MicroLinux
a.IOS
b.Android
c.Teledroid
d.LinuxMobile
Answers
The Linux platform that runs on mobile phones is called: b.Android
What is the Linux platform?Android is an open-source OS for mobile devices based on Linux. Developed by Android Inc., later acquired by Go/o/gle. Android is a popular and adaptable platform for mobile devices. Android is Linux-based.
The Linux kernel manages processes, memory, devices, and security. Android is open-source, allowing developers to freely modify and distribute its source code. The open nature draws a vibrant developer community to improve Android.
Learn more about Linux platform from
https://brainly.com/question/12853667
#SPJ4
what will the value of x be after the following nested loop executes in matlab (enter a number)? x = 0 ; for r = 1 : 3 for c = 1 : 2 x = x c ; end end
Answers
The number of times the outer loop executes, which is 3. Therefore, x = 6.
What is outer loop execute?Outer loop is a type of looping structure in programming. It is used to execute a block of code a certain number of times. Outer loop is also known as the outermost loop because it is the loop that is the furthest out from the inner loop. It is typically used when you need to repeat a process multiple times, such as looping through a list of items. The outer loop is responsible for iterating over the entire list, while the inner loop is responsible for performing some kind of action on each item in the list. Outer loops are commonly used in programming languages such as Java, C#, and Python.
x will have a value of 6 after the nested loop executes. The value of x will increment by 2 every time the inner loop executes, and the inner loop will execute twice every time the outer loop executes, so the final value of x will be 2 times the number of times the outer loop executes, which is 3. Therefore, x = 6.
To learn more about outer loop execute
https://brainly.com/question/30919197
#SPJ4
Why does an annular eclipse occur when the moon is between the sun and Earth, but is too far from Earth for a total eclipse?
Answers
Answer:
Moon Is Far from Earth
Explanation:
The reason we can see the glowing outer edge of the Sun at the maximum point of an annular eclipse is that it happens while the Moon is near its farthest point from Earth, called apogee, when the Moon is smaller than the Sun when viewed from Earth.
what is networking??????????????????????
Answers
Answer:
the activity or cycle of collaborating with others to trade data and create proficient or social contacts.
Explanation:
<3
What is a good general rule to follow when deciding whether to repair or replace a computer
Answers
Answer:
witch is most cheap and would benifit you use pros and cons
Explanation:
FILL THE BLANK. in a swap module, the variable used as a temporary storage location is declared as a ________ variable.
Answers
In a swap module, the variable used as a temporary storage location is declared as a "temporary" variable.
The purpose of the temporary variable is to temporarily hold the value of one variable while swapping it with the value of another variable. It allows for the exchange of values between variables without losing the original values during the swapping process.
The temporary variable is often declared within the scope of the swap module or function. It is used to facilitate the swapping operation by storing the value of one variable before assigning it to another variable, ensuring that both variables have their values exchanged correctly.
By using a temporary variable, the values of the variables can be interchanged without data loss or interference, providing a reliable and predictable swapping mechanism. Once the swapping is completed, the temporary variable can be discarded as its purpose has been served.
Learn more about Variable: https://brainly.com/question/28248724
#SPJ11
Who is the monst important person and why
Answers
Answer:
Jesus Christ
Explanation:
Jesus Christ is the Son of God, and he was sent down to Earth to be sacraficed and die for your sins, so that everyone who believes in him should be forgiven and have eternal life.
Internal combustion engines use hot expanding gasses to produce the engine's power. Technician A says that some engines use spark to ignite the gasses. Technician B says some engines use compression to ignite the gasses. Who is correct?
Answers
Answer:
Explanation:
Both are right.
Engines are divided into:
1) Internal combustion engines
2) Diesels
Python - Write a program to print the multiplication table as shown in the image by using for loops.

Answers
Answer:
Explanation:
The following python code creates the multiplication table for 10 rows and 10 columns. This code uses nested for loops to traverse the table and print out the product of each multiplication. The image attached shows the output of the code.
for x in range(1, 11):
for y in range(1, 11):
z = x * y
print(z, end="\t")
print()

The program to print the multiplication table as shown in the image by using for loops is in the Source code.
The Python program that uses nested for loops to print the multiplication table:
Source code:
for i in range(1, 11):
for j in range(1, 11):
if i == 1 and j == 1:
print("x", end=" ")
elif i == 1:
print(j, end=" ")
elif j == 1:
print(i, end=" ")
else:
print(i * j, end=" ")
print()
This program will iterate through the values of `i` from 1 to 10 and `j` from 1 to 10. It checks for special cases when `i` or `j` is equal to 1 to print the headers (x and the numbers 1 to 10).
For other cases, it calculates the multiplication of `i` and `j` and prints the result.
Learn more about Nested loop here:
https://brainly.com/question/33832336
#SPJ6
hard copies of cji data should be ________when no longer required.
Answers
The answer to your question is that hard copies of CJI data should be disposed of properly when they are no longer command needed. This means that they should be shredded or otherwise destroyed in a secure manner to prevent unauthorized access to the sensitive information they contain.
it is important to remember that CJI data, or criminal justice information, is highly sensitive information that is subject to strict regulations and protections. This includes information such as criminal histories, fingerprints, and other identifying information about individuals involved in the criminal justice system.
When hard copies of this data are no longer needed, they pose a risk if they are not properly disposed of. This is because they could fall into the wrong hands and be used for nefarious purposes, such as identity theft or other crimes. In order to ensure the security of CJI data, it is important to follow proper procedures for disposal, including shredding or other secure destruction methods. This may require additional resources and planning, but it is an essential step in protecting the sensitive information involved.
To know more about command visit:
https://brainly.com/question/29627815
#SPJ11
Which of the following describes why graphical interfaces quickly became popular after their introduction to the mass market?
A.superior usability
B.form over function
C.strong ISO standards
D.contextual design analysis of a market demographic
Answers
A.superior usability
What must be true if the triangles are similar by sas~? assign lengths and angle measures to the variables to demonstrate your reasoning.
Answers
The correct statement for the triangles to be similar to each other by SAS is,
y = z, and c/f = a/e,
where y = z = 50°; c = 4, f = 3; a = 8; e = 6.
We have,
There are two triangles shown in the attached image.
Since We know that,
SAS stands for "side-angle-side", which means that if two triangles have two pairs of corresponding sides that are proportional in length and the included angles between them are congruent, then the triangles are similar.
Here, the triangles are similar by SAS.
Therefore, for the triangles to be similar to SAS, we would have:
y = z, and
c/f = a/e
Assigning values, we would have:
y = z = 50°
c/f = 4/3
a/e = 8/6
Learn more about the SAS Similarity Theorem on:
brainly.com/question/22472034
#SPJ4

(2.04 MC)Carlos is using the software development life cycle to create a new app. He has completed writing the code and is ready to see the output it produces. What stage of the software development life cycle is Carlos ready for next?
Answers
Carlos is ready for the testing stage of the software development life cycle.
After completing the coding phase in the software development life cycle, the next stage is typically the testing phase. This involves checking the code for errors or bugs, and making sure it meets the requirements and specifications outlined in the planning phase. During testing, Carlos can run various tests on the app to verify that it functions correctly, and make any necessary adjustments to the code. Once the testing phase is complete and the app is deemed to be functioning properly, it can move on to the deployment phase.
You can learn more about software development life cycle at
https://brainly.com/question/30523819
#SPJ11
Vulnerability scanners make use of common identifiers to facilitate sharing of intelligence data across different platforms. Currently, a security engineer has an interest in Common Weakness Enumeration (CWE) items. Which area does the engineer study
Answers
Answer: The purpose of CWE is to facilitate the effective use of tools that can identify, find and resolve bugs, vulnerabilities and exposures in computer software before the programs are publicly distributed or sold.
Explanation:
Currently, a security engineer has an interest in Common Weakness Enumeration (CWE) items. The engineer study computer software and programs.
What is CWE?The Common Weakness Enumeration is a classification scheme for flaws and vulnerabilities in both software as well as hardware. This is supported by a community effort whose objectives are to comprehend hardware and software defects and develop bots that may be used to find, correct, and eliminate those problems.
The goal of CWE is to make it easier in using methods that could also locate, discover, and fix flaws, exploits, and exposes in computer code even before applications are made available to the general population or sold.
Common identities are used by penetration tests to enable the dissemination of intelligence information throughout many networks.
Learn more about CWE, here:
https://brainly.com/question/24469282
#SPJ5
A set of programs that enable the hardware to process data is _____.
a. network
b. procedures
c. software
d. hardware E. database
Answers
The main function of Cyber Incident Response Capability (CIRC) is to _____.
a.
restrict access controls to unauthorized personnel
b.
provide level 1 security
c.
create backdoors to bypass security protocols
d.
provide information on security incidents
Answers
The main function of Cyber Incident Response Capability (CIRC) is to provide information on security incidents. so the correct option is D.
What is access control in security?Access controls restrict unauthorized individuals from using information resources. These controls involve two major functions: authentication and authorization. Authentication confirms the identity of the person requiring access.
Access control is a central region of the information security that directs who's permitted to access and utilize organization data and assets.
Cyber Incident Response Capability (CIRC) provide the information on security incidents.
Therefore, the correct option is D.
Learn more about access control here:
brainly.com/question/27961288
#SPJ4
Some systems allow a data file to specify the program it is to be used with. This property is called a(n)
a) association.
b) attachment.
c) relationship.
d) membership.
Answers
The correct answer is a) association. An association is a property that allows a data file to specify the program it is to be used with.
When a data file specifies the program it is to be used with, this property is called an association. When a user opens a file, the operating system uses the association to determine which program should be used to open the file.
This feature is helpful because it allows users to easily work with different types of files without having to manually select the appropriate program each time. It also helps ensure that files are opened in the correct program, reducing the risk of errors or compatibility issues.
Learn more about operating system here:
brainly.com/question/6689423
#SPJ11
Explain the function of cpu what are work done by cu ,alu,and mu
Answers
Answer:
The CPU processes instructions it receives in the process of decoding data.
An arithmetic logic unit (ALU) is a digital circuit used to perform arithmetic and logic operations. It represents the fundamental building block of the central processing unit (CPU) of a computer. Modern CPUs contain very powerful and complex ALUs. In addition to ALUs, modern CPUs contain a control unit (CU). While the memory unit (MU), is the primary memory for holding data. It tells the computer's memory, arithmetic/logic unit and input and output devices how to respond to a program's instructions.
Hope this helps! :)
Which of these is not a potential cause of data loss?
using the ARP protocol
firewall
human error
network congestion
Answers
Answer:
Using the ARP protocol
Explanation:
Edgenuity and i got it right
Answer:
ARP
Explanation:
EDJ 2020
What is
assembly language
Answers
Explanation:
An assembly language is a type of low-level programming language that is intended to communicate directly with a computer's hardware. Unlike machine language, which consists of binary and hexadecimal characters, assembly languages are designed to be readable by humans.
which of the following are true? (select all that apply). a full mesh topology is more scalable than the hub-and-spoke topology a full mesh topology is more fault-tolerance than the hub-and-spoke topology. client-server network is more scalable than peer-to-peer network. star topology requires more cable than ring topology. a logical topology describes how devices are connected to each other while a physical topology defines how devices communicate with each other.
Answers
Every element in the network is directly linked to every other element. A mesh topology has the following characteristics: Links across the network are redundant in a mesh design.
Is mesh and fully connected topology same?This topology offers a lot of redundancy as well as various paths to success at the target. Both privacy and security are very good. Because failure doesn't interfere with its operations, data transfer is more reliable. Transmission of data won't be hampered by adding extra devices.
comprehensive topology: a topology for a network where there is always a direct route (branch) between any two nodes. There are n(n-1)/2 direct pathways, or branches, in a fully connected network with n nodes. mesh network with all nodes connected.
When a network's nodes are all connected to one another by a circuit, this is known as a full mesh topology. In case of a node failure, network traffic can be routed to any of the other nodes thanks to full mesh's highest level of redundancy. For backbone networks, full mesh is typically used.
To learn more about topology refer to :
https://brainly.com/question/8983698
#SPJ4
which one of the following would not normally be found in an organization's information security policy?
Answers
Requirement to use AES-256 encryption would not normally be found in an organization's information security policy.
When it comes to information security, organizations have a variety of different policies and requirements that they adhere to. One of those requirements is the use of AES-256 encryption.
However, not every organization has AES-256 encryption as a requirement in their information security policy. In fact, many organizations don't even know what AES-256 encryption is.
Why is AES-256 encryption relevant?
Well, AES-256 encryption is a strong form of encryption that is used to protect data. It is often used by governments and organizations to protect sensitive data.
AES-256 encryption is a requirement for many organizations because it provides a high level of security for data. Without AES-256 encryption, data could be compromised.
Learn more about information security policy here:
https://brainly.com/question/14292882
#SPJ4