what data type can be used to represent a number of students in a class
Answers
Answer:
percentage
Explanation:
percentage, character, interger
Related Questions
Which of the following best describes an insider attack on a network?
OA. an attack by someone who uses fake emails to gather information related to user credentials
OB. an attack by someone who becomes an intermediary between two communication devices in an organizatio
OC. an attack by a current or former employee who misuses access to an organization's network
O D. an attack by an employee who tricks coworkers into divulging critical information to compromise a network
Answers
An attack by a current or former employee who misuses access to an organization's network ca be an insider attack on a network. The correct option is C.
An insider attack on a network refers to an attack carried out by a person who has authorized access to an organization's network infrastructure, either as a current or former employee.
This individual intentionally misuses their access privileges to compromise the network's security or to cause harm to the organization.
Option C best describes an insider attack as it specifically mentions the misuse of network access by a current or former employee.
The other options mentioned (A, B, and D) describe different types of attacks, but they do not specifically involve an insider with authorized access to the network.
Thus, the correct option is C.
For more details regarding network, visit:
https://brainly.com/question/29350844
#SPJ1
question below in attachment
Answers
You can use basic HTML elements like input, select and textarea to generate an HTML web-form and gather the data for the code table.
What is the program?The form in this code case is configured to use the "post" method and directs to "insert_item.php", a PHP script that manages the form submissions. The structure comprises of input sections for the "name", "description", and "quantity" cells in the "item" table, as well as a button for submitting the information.
One method of collecting user input from a web-form and adding it to a database table is by utilizing PHP and SQL commands, which enables connectivity to the database and the ability to run the INSERT query.
Learn more about program from
https://brainly.com/question/26134656
#SPJ1



Write a method named removeDuplicates that accepts as a parameter a List of integers, and modifies it by removing any duplicates. Note that the elements of the list are not in any particular order, so the duplicates might not occur consecutively. You should retain the original relative order of the elements. Use a Set as auxiliary storage to help you solve this problem.
For example, if a list named list stores [4, 0, 2, 9, 4, 7, 2, 0, 0, 9, 6, 6], the call of removeDuplicates(list); should modify it to store [4, 0, 2, 9, 7, 6].
Answers
The method is an illustration of loops or iteration.
Loops are used to carry out repetitive operations.
The removeDuplicates method in Python is as follows, where comments are used to explain each line.
#This defines the method
def removeDuplicates(list):
#This initializes the output list
outputList = []
#This iterates through the list
for i in list:
#All elements not in the output list, are appended to the output list
if i not in outputList:
outputList.append(i)
#This returns the output list
return str(outputList)
At the end of the method, the new list contains no duplicates.
Read more about similar program at:
https://brainly.com/question/6692366
Which robot component could be considered an output device?
A. A display screen
B. A keypad
C. A temperature sensor
D. An ultrasonic detector
Answers
Answer:
B. A keypad
Explanation:
B. A keypad I guess
the programming language is for visual basic

Answers
A code segment that displays a menu of three food items along with a quit
option
while True:
print("Please choose one of the following options:")
print("1. Pizza")
print("2. Chicken")
print("3. Salad")
print("4. Quit")
choice = input("Enter your choice: "
What is code segment?
A code segment, sometimes referred to as a text segment or just text in the computing world, is a section of a computer file that is made up of object code or an equivalent section of the program's address space which contains information about executable commands and directives. When a programme is processed and run, it is often saved in an object-code-based computer file. The code segment is on of the object file's divisions. When the programme is loaded into memory by the loader so that it might be executed and implemented, various memory segments are assigned for a specific use, just as they are for segments in object code-based computer files and segments that are only needed during run time when the programme is being executed.
To learn more about code segment
https://brainly.com/question/25781514
#SPJ13
In this lab, you declare and initialize constants in a Java program. The program file named NewAge2.java, calculates your age in the year 2050.
Answers
This sentence is a statement about a lab activity involving writing a Java program to calculate someone's age in the year 2050. The program is named NewAge2.java, and it involves declaring and initializing constants. The sentence does not provide any further details about the lab or how the program works, but it suggests that the program involves some mathematical calculations to determine someone's age in the future.
public static void main(String[] args) {
final int CURRENT_YEAR = 2023;
final int BIRTH_YEAR = 1990;
final int FUTURE_YEAR = 2050;
int currentAge = CURRENT_YEAR - BIRTH_YEAR;
int futureAge = currentAge + (FUTURE_YEAR - CURRENT_YEAR);
System.out.println("Your current age is: " + currentAge);
System.out.println("Your age in " + FUTURE_YEAR + " will be: " + futureAge);
}
}
Write code in MinutesToHours that assigns totalHours with totalMins divided by 60
Given the following code:
Function MinutesToHours(float totalMins) returns float totalHours
totalHours = MinutesToHours(totalMins / 60)
// Calculate totalHours:
totalHours = 0
Function Main() returns nothing
float userMins
float totalHours
userMins = Get next input
totalHours = MinutesToHours(userMins)
Put userMins to output
Put " minutes are " to output
Put totalHours to output
Put " hours." to output
Answers
Answer:
Function MinutesToHours(float totalMins) returns float totalHours
// Calculate totalHours:
totalHours = totalMins / 60
return totalHours
End Function
somebody help me to fix this code
class Item:
def __init__(self, nome, quantidade, marca):
self.nome = nome
self.quantidade = quantidade
self.marca = ade
self.marca = marca
self.proximo = None
class ListaDeCompras:
def __init__(self):
self.primeiro = None
self.ultimo = None
def adicionar_item(self, nome, quantidade, marca):
novo_item = Item(nome, quantidade, marca)
if self.primeiro is None:
self.primeiro = if self.primeiro is None:
self.primeiro = novo_item
self.ultimo = novo_item
else:
self.ultimo.proximo = novo_item
self.ultimo = novo_item
def remover_item(self, nome):
item_atual = self.primeiro
item_anterior = None
while item_atual is not None:
if item_atual.nome == nome:
if item_anterior is not None:
item_anterior.proximo = item_atual.proximo
else:
self.primeiro = item_atual.proximo
if item_atual.proximo is None:
self.ultimo = item_anterior
return True
item_anterior = item_atual
item_atual = item_atual.proximo
return False
def imprimir_lista(self):
item_atual = self.primeiro
while item_atual is not None:
print(f"{item_atual.nome} - {item_atual.quantidade} - {item_atual.marca}")
item_atual = item_atual.proximo
Answers
What has changed?
You have defined two classes in Python. These classes also have constructor methods. In the first of these constructor methods, you have defined the variable "marca" twice. I fixed a typo in the "adicionar_item" method in the second class. I fixed the if-else block structure in the "remover_item" method.
class Item:
def __init__(self, nome, quantidade, marca):
self.nome = nome
self.quantidade = quantidade
self.marca = marca
self.proximo = None
class ListaDeCompras:
def __init__(self):
self.primeiro = None
self.ultimo = None
def adicionar_item(self, nome, quantidade, marca):
novo_item = Item(nome, quantidade, marca)
if self.primeiro is None:
self.primeiro = novo_item
self.ultimo = novo_item
else:
self.ultimo.proximo = novo_item
self.ultimo = novo_item
def remover_item(self, nome):
item_atual = self.primeiro
item_anterior = None
while item_atual is not None:
if item_atual.nome == nome:
if item_anterior is not None:
item_anterior.proximo = item_atual.proximo
else:
self.primeiro = item_atual.proximo
if item_atual.proximo is None:
self.ultimo = item_anterior
return True
item_anterior = item_atual
item_atual = item_atual.proximo
return False
def imprimir_lista(self):
item_atual = self.primeiro
while item_atual is not None:
print(f"{item_atual.nome} - {item_atual.quantidade} - {item_atual.marca}")
item_atual = item_atual.proximo
Which of the following pieces of equipment has a 3-P ,30 -A rated combination magnetic motor starter ?
aA.3/4 -hp motor
B.ATC PANEL
C.water heater
D.single pole switch
Answers
a) A.3/4 -hp motor has a 3-p, 30 -A rated combination magnetic motor starter
follow me to know more of my answers
Match the different aspects of the marketing information systems to the scenarios that portray them.
1. Marketing intelligence system
2. Internal reporting system
3. Marketing model
4. Marketing research system
A. includes number of orders received, stock holdings, and sales invoices
B. MIS collects, regulates, and analyzes data for marketing plan
C. gathers information such as demographic data
D. includes time series, sales model, and linear programming
Answers
Answer:
1. Marketing intelligence system - C
2. Internal reporting system - A
3. Marketing model - D
4. Marketing research system - B
Explanation:
9. They are normally made of huge steel towers.
a. Transmission Lines
c. Distribution Substation
b. Transmission Substation
d. Distribution Lines
10. Voltage reduction is done through a attached through pole,
a. Transmission Transformer c. Distribution Substation . . b.DistributionTransfont
d. Disttid tihines
Answers
Answer:
9. a (Transmission Lines )
10.a (Transmission Transformer)
The thing that are normally made of huge steel towers is a. Transmission Lines, option A is correct.
Voltage reduction is done through a attached through pole, a. Transmission Transformer, option A is correct.
What is Voltage reduction?Voltage reduction has emerged as another tool utilities can use to lower demand, usually without the customer's knowledge. Yet, only the load's resistive part reacts to the drop in voltage by lowering aggregate demand.
Several electric utilities regularly use voltage reduction as a tool for energy conservation and as a way to lower system peak demand during emergency situations or, in some cases, during daily peak load periods.
Learn more about Voltage reduction at;
https://brainly.com/question/28164474
#SPJ3
Given a positive integer n, the following rules will always create a sequence that ends with 1, called the hailstone sequence:If n is even, divide it by 2If n is odd, multiply it by 3 and add 1 (i.e. 3n +1)Continue until n is 1Write a program that reads an integer as input and prints the hailstone sequence starting with the integer entered. Format the output so that ten integers, each separated by a tab character (\t), are printed per line.The output format can be achieved as follows:print(n, end='\t')Ex: If the input is:
Answers
Question 11 (2.5 points)
A start-up company has hired you to implement an email strategy for its organization.
The company wants all of its employees to have an enterprise-level email client and
is considering Windows Live Essentials. They ask you if there are any limitations
about this email solution. Which of the following is a major limitation?
Answers
Answer:
the dot
Explanation:
the dot is a good day forecast for a bit
Create a c program that calculates the amount of time and fuel for a 1980 Cessna 172N to fly a specified distance.
Answers
Solution :
#include <iostream>
#include <iomanip>
using namespace std;
int main()
{
//declaring variables
int mile, hours ,minute;
char option='Y';
float fuel;
//display welcome message
cout<<"Aircraft Fuel Calculator\n\n";
//this loop will run untill user enter Y or y
while(option=='Y' || option=='y'){
//asking user to enter miles
cout<<"Distance in nautical miles : ";
cin>>miles;
//calculating hour and minutes
hour=miles/120;
minutes=(miles%120)/2;
//setting 1 decimal place
cout << fixed << setprecision(1);
fuel=(miles/120.0 + 0.5)*8.4;
//display data
cout<<"Flight time: "<<hour<<" hour(s) and "<<minutes<<" minute(s)"<<endl;
cout<<"Required fuel: "<<fuel<<" gallons\n\n";
cout<<"Continue? (y/n): ";
cin>>option;
cout<<"\n";
}
cout << "Bye!" << endl;
return 0;
In a non-price rationing system, consumers receive goods and services first-come, first served. Give me an example of a time when a consumer may experience this.
Answers
When someone may be giving away something for free.
Fill in the blank: To keep your content calendar agile, it shouldn’t extend more than ___________.
two weeks
one month
three months
six month
Answers
To keep your content calendar agile, it shouldn’t extend more than three months.
Thus, A written schedule for when and where content will be published is known as a content calendar.
Maintaining a well-organized content marketing strategy is crucial since it protects you from last-minute crisis scenarios and enables you to consistently generate new material and calender agile.
As a result, after the additional three months, it was unable to maintain your content calendar's agility.
Thus, To keep your content calendar agile, it shouldn’t extend more than three months.
Learn more about Calendar, refer to the link:
https://brainly.com/question/4657906
#SPJ1
foot pad, starting mark, handle, and hook are all pieces of what tool?
A. Conduit locknut
B. PVC cutter
C. Bender
D. Fish tape
Answers
Answer:
Explanation:
b
Engine Room Tools, 1949, is indeed a training book, focusing here on the proper use of tools onboard vessels. It is remarkable since it contains equipment unique to the marine industry.
This machinery has a history that marine experts should thoroughly research.This history will teach you a lot about machinery's previous experiences, including severe accidents, difficulties, and refurbishing operations.Therefore, Each engine room has a footpad, the starting line, a handle, and a hook.
Learn more:
brainly.com/question/1101514

full forms Window XP
Answers
c++ program by using + operator overloading

Answers
A good example of a program that shows operator overloading for complex numbers and employee bonus calculation is given below
What is the c++ program?In the code given. the Complex class in this software shows complex numbers and has overloaded the + and * operators. The Employee category shows an individual hired by a company and tells their bonus amount in accordance with their relevant experience.
The software is one that gives c1 and c2 complex numbers, then applies overloaded operators to execute addition and multiplication. After that, the outcomes are reproduced.
Learn more about c++ program from
https://brainly.com/question/13441075
#SPJ1
See text below
Ex No: 5 2623
Aimi
Operator Overloading
To implement c++ program by overloading the operators needed for their application.
Problem statements:
To overload +, *, 24, ≫ operators for two complex numbers.
c++ program
To overload the + operator for employee bonus calculation.
Tips for bonus calculation:
* If experience of employee is:
→0 to 5 years then, B. P = 16500, DA=5%. 4 BP, HRA = 2% of B.P, Bonus = 500
→ 6 to 10 years then, B.P = 16500, DA = 10%. of B-P, HRA = 47. of B.P, Bonus = 750
→ 11 to 20 years then, B.P = 16500, DA = 10%. of B⋅P, HRA = 7%. & B. P, Bonus = 1500
→ More than 20 years then, B.P = 16500, DA =151 of B.P, 10%. of B⋅ P= HRA, Bonus = 3000



Write a python program to display "Hello, How are you?" if a number entered by
user is a multiple of five, otherwise print "Bye Bye"
Answers
Answer:
Here's a simple Python program that takes input from the user and checks if the entered number is a multiple of five, then displays the appropriate message accordingly:
# Get input from user
num = int(input("Enter a number: "))
# Check if the number is a multiple of five
if num % 5 == 0:
print("Hello, How are you?")
else:
print("Bye Bye")
Answer:
Here's a simple Python program that takes input from the user and checks if the entered number is a multiple of five, then displays the appropriate message accordingly:
# Get input from user
num = int(input("Enter a number: "))
# Check if the number is a multiple of five
if num % 5 == 0:
print("Hello, How are you?")
else:
print("Bye Bye")
This is in Java.
Description:
Output "Fruit" if the value of userItem is a type of fruit. Otherwise, if the value of userItem is a type of drink, output "Drink". End each output with a newline.
Ex: If userItem is GR_APPLES, then the output is:
Fruit
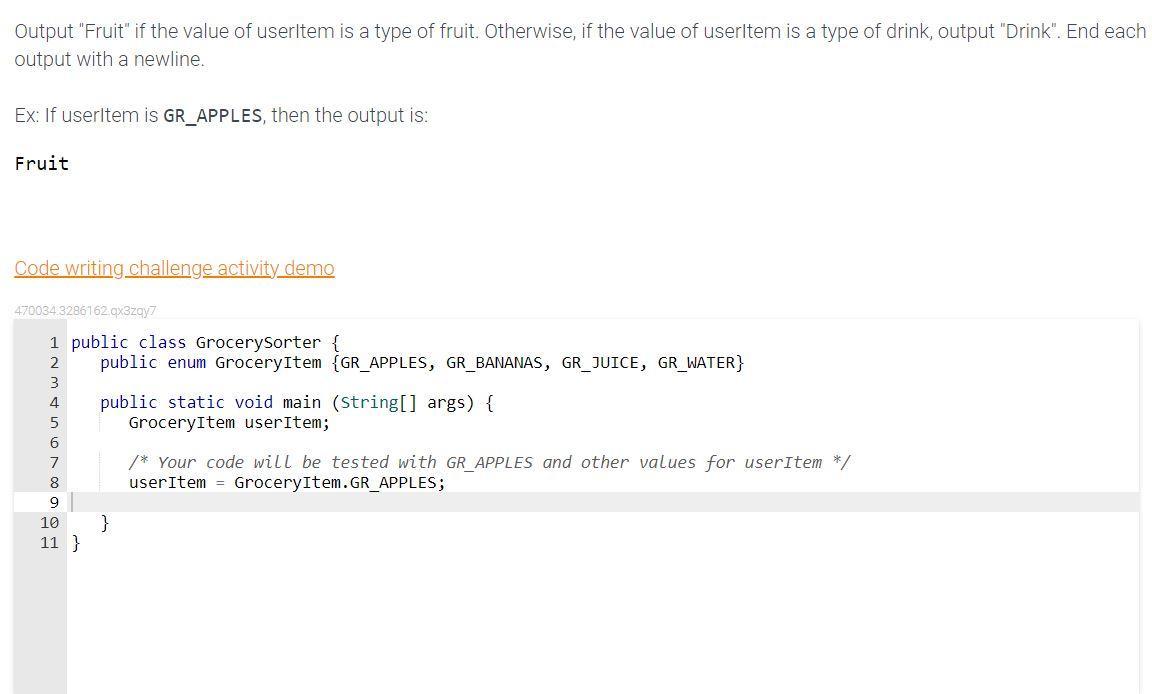
Answers
Explanation:
public class GrocerySorter {
public static void main(String[] args) {
GroceryItem item = new GroceryItem("GR_APPLES", 1.99);
String itemName = item.getName();
if(itemName.startsWith("GR_")) {
System.out.println("Fruit\n");
} else {
System.out.println("Drink\n");
}
}
}
The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
What is program in Python?The program in Python, where comments are used to explain each line is as follows
#This gets input from the user
userItem = input("Item: ")
#This checks if user input is GR_APPLES or GR_BANANAS
if(userItem == "GR_APPLES" or userItem == "GR_BANANAS"):
#If yes, the program prints Fruit
print("Fruit")
#if otherwise, this checks if user input is GR_JUICE or GR_WATER
elif (userItem == "GR_JUICE" or userItem == "GR_WATER"):
#If yes, the program prints Drink
print("Drink")
#If otherwise
else:
#This prints Invalid
print("Invalid")
See attachment for sample run
Therefore, The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
Read more about conditional statements at:
brainly.com/question/4211780
#SPJ2
Which of the following is the most effective protection against IP packet spoofing on a private network?
Anti-virus scanners
Host-based IDS
Ingress and egress filters
Digital signatures
Answers
The correct response is d) ingress and egress filters. Filters provide you the ability to choose certain records from a list depending on certain criteria.
Systems or components known as filters are used to eliminate particles like dust, filth, electronic signals, etc. as they travel through filtering material or equipment. Filters can be used to remove particles from fluids, gases, electrical, and optical phenomena. The low-pass filter, high-pass filter, band-pass filter, and notch filter are the four main categories of filters (or the band-reject or band-stop filter). Based on the frequency range that they are permitting and/or rejecting, active filters can be broadly divided into the following four types: Low-pass active filter. High-pass active filter. Bandpass active filter. Band-stop filter that is active. In radio, television, audio recording, radar, control systems, music synthesis, image processing, and computer graphics, filters are used extensively in electronics and telecommunication.
Learn more about filters here
https://brainly.com/question/7411233
#SPJ4
What is a disadvantage of communicating on social media?
Collaborating with others
Speed
Lack of privacy
Maintaining relationships
Answers
Answer:
Lack of privacy
Explanation:
what is smarta Art ?
Answers
Answer:
A SmartArt graphic is a visual representation of your information and ideas. You create one by choosing a layout that fits your message. Some layouts (such as organization charts and Venn diagrams) portray specific kinds of information, while others simply enhance the appearance of a bulleted list.
short ans(SmartArt is a way to turn ordinary text into something more visually appealing. It helps draw attention to important information or make information easier to interpret and understand.)
The are two schools of ____________ are Symmetry and Asymmetry.
Answers
The two schools of design that encompass symmetry and asymmetry are known as symmetrical design and asymmetrical design.
Symmetrical design is characterized by the balanced distribution of visual elements on either side of a central axis. It follows a mirror-like reflection, where the elements on one side are replicated on the other side, creating a sense of equilibrium and harmony.
Symmetrical designs often evoke a sense of formality, stability, and order.
On the other hand, asymmetrical design embraces a more dynamic and informal approach. It involves the intentional placement of visual elements in an unbalanced manner, without strict adherence to a central axis.
Asymmetrical designs strive for a sense of visual interest and tension through the careful juxtaposition of elements with varying sizes, shapes, colors, and textures.
They create a more energetic and vibrant visual experience.
Both symmetrical and asymmetrical design approaches have their merits and are employed in various contexts. Symmetry is often used in formal settings, such as architecture, classical art, and traditional graphic design, to convey a sense of elegance and tradition.
Asymmetry, on the other hand, is commonly found in contemporary design, modern art, and advertising, where it adds a sense of dynamism and creativity.
In conclusion, the schools of symmetry and asymmetry represent distinct design approaches, with symmetrical design emphasizing balance and order, while asymmetrical design embraces a more dynamic and unbalanced aesthetic.
For more such questions on symmetry,click on
https://brainly.com/question/31547649
#SPJ8
The more employees can do, the less they have to be managed by supervisors.
Please select the best answer from the choices provided
T
F
Answers
Don’t take me too seriously cause I could be wrong, but I think it’s false. Unless the employees are like the best hardworking employees, they will likely slack off the second they get the chance. The more they can do just means that they can do more, it doesn’t necessary mean they need less supervision
Answer:
True
Explanation:
A digital footprint is something
Answers
Describe the discretionary power of police
Answers
Police officers are trained to use their discretion in a way that is fair, impartial, and consistent with the law. They are expected to exercise their power in a way that promotes public safety and protects the rights of individuals. However, discretionary power can also be abused, leading to unfair treatment or discrimination based on factors such as race, ethnicity, or socio-economic status.
Police officers are held accountable for their use of discretionary power through internal review processes and external oversight by independent agencies. In some cases, excessive or inappropriate use of discretionary power can lead to disciplinary action, legal consequences, or civil suits against the police department.
Overall, the discretionary power of police is an important aspect of their role in maintaining law and order. However, it is important to ensure that this power is used in a way that is fair, transparent, and accountable, and that it promotes trust and confidence in the police force among all members of the community.
is permanent software programmed into read-only memory.
Firmware
JavaScript
PHP
o
Answers
Answer:
Firmware
Explanation:
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1