- Writo an algorithm to convert from two dimensional array into single dimersional array using two loops?
Answers
Here's an algorithm to convert a two-dimensional array into a single-dimensional array using two loops:
1. Initialize an empty single-dimensional array.
2. Set a variable `index` to 0 to keep track of the current index in the single-dimensional array.
3. Use a nested loop to iterate over each element of the two-dimensional array:
a. Outer loop for rows: Iterate over each row of the two-dimensional array.
b. Inner loop for columns: Iterate over each column within the current row.
4. For each element in the two-dimensional array:
a. Assign the current element to the single-dimensional array at the `index` position.
b. Increment the `index` by 1.
5. After iterating through all the elements of the two-dimensional array, you will have populated the single-dimensional array with all the elements.
6. Return the single-dimensional array.
Here's the algorithm in pseudo code:
```
function convertToSingleDimensional(array2D):
singleArray = [] // Initialize the single-dimensional array
index = 0 // Initialize the index counter
// Iterate over each row
for row in array2D:
// Iterate over each column within the current row
for element in row:
singleArray[index] = element // Assign the element to the single-dimensional array
index = index + 1 // Increment the index counter
return singleArray
```
You can implement this algorithm in the programming language of your choice, such as C++, Java, Python, etc., by following the steps and using the appropriate syntax and data structures for that language.
Learn more about algorithm here:
https://brainly.com/question/33344655
#SPJ11
Related Questions
Which of the following sound file formats have a MIME type of audio/basic?
SNDiframevspacefadezone
Answers
The sound file format that has a MIME type of audio/basic is the Au file format.
The MIME type is a standard used to identify the format of a file based on its content. The audio/basic MIME type is used to identify audio files that use a simple format without any compression. The Au file format, also known as the Sun audio format, is one of the audio formats that uses the audio/basic MIME type. It was developed by Sun Microsystems for use on their Unix-based workstations. The Au file format is a simple format that supports mono or stereo audio at a variety of sample rates and bit depths. It is still used today in some applications, particularly those that require compatibility with legacy systems. Other audio file formats that have different MIME types include WAV, MP3, and Ogg Vorbis.
Learn more about audio file formats and MIME types here:
brainly.com/question/31313637
#SPJ11
Apply the default name for the rule (Gloria Vivaldi) and turn it on for current and future messages.
Answers
The steps to set up a rule with the default name "Gloria Vivaldi" in Microsoft Outlook is given below.
What are the steps needed?Open Microsoft Outlook.
Click on the "File" tab and select "Manage Rules & Alerts."
Click on the "New Rule" button to create a new rule.
In the "Rules Wizard" window, select "Apply rule on messages I receive" and click "Next."
Choose the conditions that you want to apply to the rule, such as specific senders or keywords in the subject line. Click "Next" after making your selections.
Choose the action that you want the rule to perform, such as moving the message to a specific folder or marking it as read.
Click "Next" after making your selections.
In the "Step 2: Edit the rule description" section, give your rule a name, such as "Gloria Vivaldi." You can also add any exceptions to the rule in this section. Click "Finish" when you're done.
The rule will be applied immediately to any incoming messages that meet the conditions you specified. You can also choose to run the rule on your existing messages by selecting the "Run Rules Now" option in the "Rules and Alerts" window.
Learn more about Microsoft on:
https://brainly.com/question/29576990
#SPJ1
Need help pleaseeee!!!!!

Answers
Answer:
Attenuation
Explanation:
This means the signal is getting weaker in long cables.
How many possible values would an 8-bit audio sample have?.
Answers
Write a c program that uses iteration to find the sum of all multiples of 3
and all multiples of 4 between 3 and 150 inclusive. Print the sum.
Answers
#include<stdio.h>
int main()
{
int sum_3=0, sum_4=0; //Variable to store the sum of multiples of 3 and 4
for(int i=3; i<=150; i++) //Iterating from 3 to 150
{
if(i%3==0) //Checking if i is a multiple of 3
sum_3 += i; //Adding i to the sum of multiples of 3
if(i%4==0) //Checking if i is a multiple of 4
sum_4 += i; //Adding i to the sum of multiples of 4
}
printf("Sum of multiples of 3: %d\n", sum_3); //Printing the sum of multiples of 3
printf("Sum of multiples of 4: %d\n", sum_4); //Printing the sum of multiples of 4
return 0;
}
HELP!!! 30 POINTS
CHOOSE THE TERM THAT MATCHES THE DEFINITION.
: a device that converts one voltage to another
: communication of binary data via the voltage level for each time interval
: the push that makes electrons move in a wire
: a device that uses voice recognition to provide a service
VOICE ASSISTANCE
VOLTAGE
ADAPTER
DIGITAL SIGNAL
Answers
Voice assitanc: a device that uses voice recognition | adapter: a device that converts one voltage to another | digital signal: communication of binary data via the voltage level | voltage: the push that makes electrons move in a wire
Explanation:
Answer:
Adapter: a device that converts one voltage to another
Digital signal: communication of binary data via the voltage level for each time interval
Voltage: the push that makes electrons move in a wire
Voice assistant: a device that uses voice recognition to provide a service
Explanation:
edge 2022

You do not have to move your fingers to click the top row reach keys.
1. True
2. False
Answers
Which is NOT a valid sparkline type?
Answers
Where are the types we are supposed to be choosing from?
Identify the causes of installation problems. (Choose all that apply)

Answers
Answer:
the last one
Explanation:
please mark brainliest
Answer: The answers are: A,B,D
edg.
In a needs assessment project, a charter often specifies how a project's success will be measured or evaluated.
true or false?
Answers
The statement is false. In a needs assessment project, a charter typically does not specify how a project's success will be measured or evaluated.
A needs assessment project primarily focuses on identifying and analyzing the needs, requirements, and gaps within an organization or a specific area. It aims to understand the current state and define the desired future state. The purpose of a needs assessment is to gather information and data to make informed decisions about potential solutions or interventions. While a project charter provides a high-level overview of the project's goals, objectives, scope, and stakeholders, it typically does not include detailed information about how the project's success will be measured or evaluated. Measuring success and establishing evaluation metrics is usually part of the project planning and implementation phase, where specific goals and performance indicators are identified and defined.
The success measurement and evaluation criteria are usually developed in collaboration with stakeholders during the project planning stage. These criteria help track progress, assess the effectiveness of the project, and determine whether the identified needs have been met. In summary, while a project charter is important for outlining the project's scope and objectives, it does not typically specify how a project's success will be measured or evaluated. That aspect is addressed during the planning and implementation phase of the project.
Learn more about project planning here:
https://brainly.com/question/30187577
#SPJ11
subscribe to twomad or you are cringe for the rest of your life kid
Answers
Answer:
What if I don't want to?..........
what is the working principle of computer?
Answers
Answer:
input, process, output, storage
you plan to deploy the following azure web apps: webapp1, that uses the .net 6 runtime stack webapp2, that uses the asp.net v4.8 runtime stack webapp3, that uses the java 17 runtime stack webapp4, that uses the php 8.0 runtime stack you need to create the app service plans for the web apps. what is the minimum number of app service plans that should be created?
Answers
Since you need to create the App Service plans for the web apps, the minimum number of App Service plans that must be created is option A-1.
How does Azure webapp work?Without needing to deploy, set up, and maintain your own Azure VMs, you may create an app in Azure using the platform offered by Azure Web Apps. The ASP.NET, PHP, Node. js, and Python may all be used to create web applications. Additionally, they incorporate well-known coding environments like GitHub and Visual Studio.
Microsoft developed and maintains Azure Web Apps, a platform for hosting websites based on cloud computing. It is a platform as a service that enables the publishing of Web apps using several frameworks and different programming languages, including proprietary ones from Microsoft.
Therefore, You can support up to 10 Web Apps by creating one App Service Plan. Any additional use of the other resources is unnecessary and not specified as a prerequisite.
Learn more about azure web apps from
https://brainly.com/question/28813133
#SPJ1
See full question below
You plan to deploy the following Azure web apps:
WebApp1, which uses the .NET 5 runtime stack
WebApp2, which uses the ASP.NET V4.8 runtime stack
WebApp3, which uses the Java 11 runtime stack
WebApp4, which uses the PHP 8.0 runtime stack
You need to create the App Service plans for the web apps.
What is the minimum number of App Service plans that must be created?
A-1
B-2
C-3
D-4
How many doors in the arsenic and old lace
Answers
In the play "Arsenic and Old Lace" by Joseph Kesselring, there are multiple doors that are used throughout the story to create comedic and suspenseful moments. The setting of the play is the Brewster family home, which is a large and old-fashioned house in Brooklyn.
There are a total of seven doors mentioned in the play, including the front door, the door to the parlor, the basement door, the door to the living room, the door to the dining room, the door to the kitchen, and the door to Teddy's room. Each of these doors is used for different purposes in the play, such as providing entrances and exits for the characters, hiding bodies, and creating confusion and chaos.
The door to Teddy's room is particularly significant, as it is used to create the illusion that Brewster's insane nephew, who believes he is President Theodore Roosevelt, is actually digging the Panama Canal in the basement. This leads to some of the play's funniest moments and helps to add to the overall absurdity of the story.
Overall, the doors in "Arsenic and Old Lace" are an essential part of the play's setting and contribute to the comedic and suspenseful tone of the story.
You can learn more about Theodore Roosevelt at: brainly.com/question/29359038
#SPJ11
Jason needs to fill the position of cost evaluator at his company but realizes there isn't anyone in the organization qualified to take this job. jason would be advised to use _____ in this situation.
a. an internal source.
b. an external source.
c. a temporary source.
d. offshoring.
Answers
Answer: B. An external source.
Write output of the given program:

Answers
Answer:
program 655555555555555
Hope wants to add a third use at the end of her nitrogen list.
What should Hope do first?
What is Hope’s next step?
Answers
Answer:the first answer is put it at the end of 2b
the second answer is press enter
Explanation:
Answer:
1, put it at the end of 2b 2, press enter key
Explanation:
Question # 4
Multiple Select
Which of the following statements are true regarding abstraction? Select 3 options.
Abstraction provides a way to see a complex situation more clearly.
Creating a model must occur before abstraction.
Abstraction is a process where details are added to further define the problem.
Refinement is the opposite of abstraction.
The level of abstraction needed depends on the situation and your goals.
Answers
Answer:
B: the level of abstraction needed depends on the situation and your goals
C: refinement is the oppostie of abstraction
E: abstraction provides a way to see a complex situtation more clearly
Explanation:
I just completed the assignemnet and was checking it while I made this answer.
Answer:
the level of abstraction needed depends on the situation and your goals
refinement is the oppostie of abstraction
abstraction provides a way to see a complex situtation more clearly
Explanation:
What are components of the network effect in social media engagement? (choose every correct answer.) multiple select question. the exp
Answers
The components of the network effect in social media engagement are:
InformationNetworkDynamicWhat is social media engagement?The Definition of the term Social media engagement is known to be a term that acts to measures all issues in regards to the public shares, the likes as well as the comments for any kind of online business as well as its social media efforts.
Note that the Engagement is one that is seen as a form of historical common metric that is known to be used for the examination of social media performance but it is one that do not need to translate to sales.
Therefore, based on the above, one can say that The components of the network effect in social media engagement are:
InformationNetworkDynamicLearn more about social media engagement from
https://brainly.com/question/8360107
#SPJ1
Information
Network
Dynamic
Player
Required Information Ch 02 Sec 2 Ex 35 MAIN - Find Unlon and Intersectlon of Sets NOTE: This is a multy-part question. Once an answer is submitted, you will be unable to retum to this port Let A
l
be the set of all nonempty bit strings (l.e., blt strings of length at least one) of length not exceeding l h 02 Sec 2 Ex 55(b) - Find Intersectlon of Sets entify ⋂
i=1
n
A
i
Mutiple Choice (1) {0,1} {O}
Answers
The multiple-choice question in Chapter 2, Section 2, Exercise 35 asks to find the intersection of sets ⋂(i=1 to n)Ai, where Ai represents the set of nonempty bit strings of length not exceeding l. The choices provided are {0,1} and {O}.
To find the intersection of sets ⋂(i=1 to n)Ai, we need to identify the common elements that are present in all sets Ai. In this specific exercise, the choices given are {0,1} and {O}. The set {0,1} represents the set containing the elements 0 and 1. Since the problem statement mentions that the sets Ai consist of nonempty bit strings, which typically include binary digits 0 and 1, the choice {0,1} is a plausible answer. On the other hand, the set {O} contains a single element, which is the uppercase letter "O." This choice seems unrelated to the problem at hand, as it does not correspond to the common elements found in the sets Ai. Based on the information provided, the more reasonable choice for the intersection of sets ⋂(i=1 to n)Ai would be {0,1}.
Learn more about intersection of sets here:
https://brainly.com/question/31246943
#SPJ11
define a method named swapvalues that takes an array of four integers as a parameter, swaps array elements at indices 0 and 1, and swaps array elements at indices 2 and 3. then write a main program that reads four integers from input and stores the integers in an array in positions 0 to 3. the main program should call function swapvalues() to swap array's values and print the swapped values on a single line separated with spaces. ex: if the input is: 3 8 2 4 function swapvalues() returns and the main program outputs: 8 3 4 2 the program must define and call a method: public static void swapvalues(int[] values)
Answers
Answer:
Explanation:
e
Can someone help me with this using the template?
Answers
Answer:
over
Explanation:
due now 2 weeks ago thats it
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
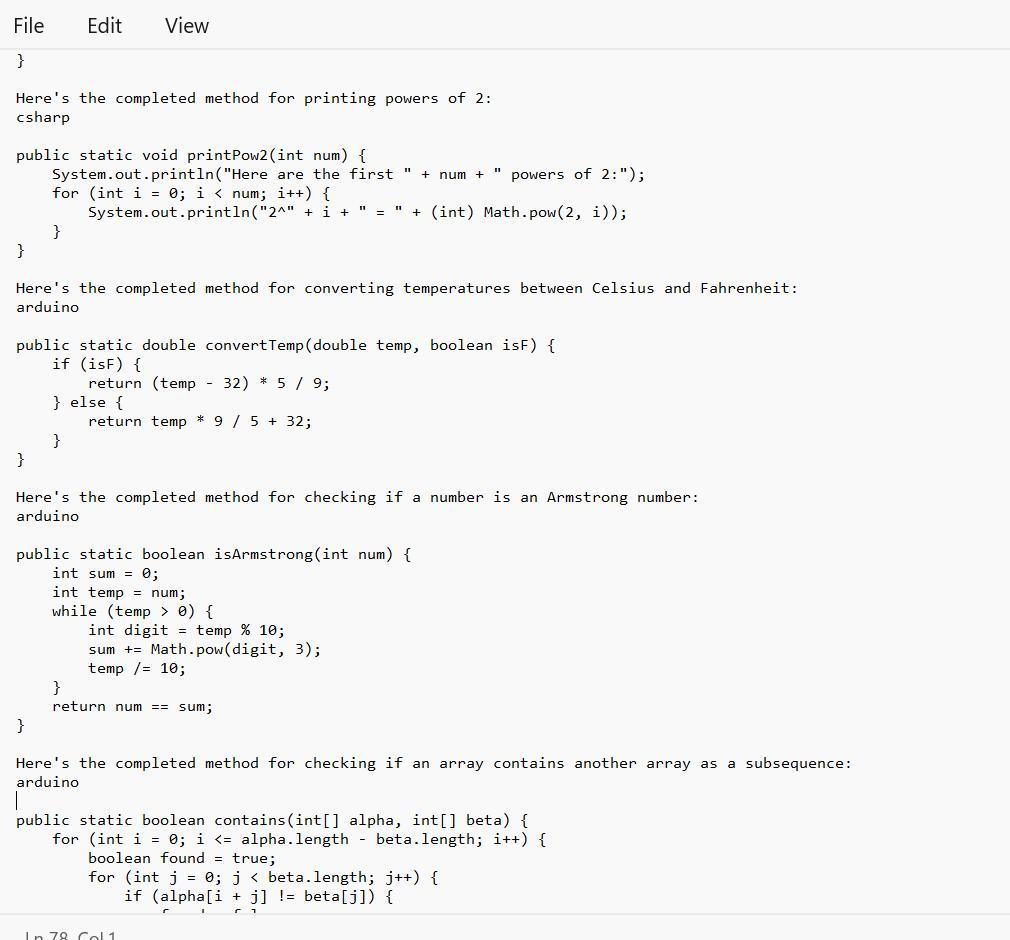
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


The high-level program instruction a = b + c is most likely to be translated to which assembly instruction?
Answers
The high-level program instruction a = b + c is most likely to be translated to which assembly instruction is option c. Add M[4], M[5], M[6].
What is high-level program referred to as?High-level languages are set up to act or be close to be used by the human operator or any kind of programmer.
Note that they are seen to as "closer to humans." based on the fact that their context is easier to know and implement and as such, The high-level program instruction a = b + c is most likely to be translated to which assembly instruction is option c. Add M[4], M[5], M[6].
Learn more about high-level program from
https://brainly.com/question/22695199
#SPJ1
See full question below
The high-level program instruction a = b + c is most likely to be translated to which assembly instruction?
a. Add M[4]
b. Add M[4], M[5]
c. Add M[4], M[5], M[6]
d. Add M[4], M[5], M[6], M[7]
In Chapter 20 you read all about different types of private networks -- VLANs, NAT, PAT, and network segmentation. Additionally, the chapter covered virtual networks. Network virtualization has changed computing for the better. It saves money, allows for more scalability in networks, provides a more rich training environment since students or new hires are able to go out and "play" with the virtual machines and really get some hands-on experience! Some of you may not have really heard too much about virtual networks or how to use a virtual computer. For this discussion board, I want you to share with the class what experience (if any) you have with VMs. Initial Response Guidelines:
In roughly 100-150 words, describe to the class your experience with virtual networks or virtual computers. Virtual reality does not really count, but if it's all you have to discuss it will work. I want you to describe not only your experiences but also your thoughts on using virtual machines to save money, learn new techniques and any other aspects of VMs you want to share.
Answers
I have extensive experience with virtual networks and virtual machines (VMs). I have worked with various virtualization platforms like VMware, VirtualBox, and Hyper-V, both for personal use and in professional settings.
Virtual networks have been an integral part of my work and learning environment. They offer several advantages, including cost savings and increased scalability. By running multiple virtual machines on a single physical server, resources can be utilized more efficiently, reducing hardware costs. Moreover, VMs can be easily cloned, allowing for quick deployment and replication of complex network setups.
Using virtual machines has also enhanced my learning experience. I have been able to experiment with different operating systems, software configurations, and networking scenarios without the need for additional physical hardware. This hands-on approach has enabled me to gain practical skills, troubleshoot issues, and explore new techniques in a safe and isolated environment.
Overall, virtual machines have been invaluable tools for me. They have provided cost-effective solutions, facilitated learning opportunities, and allowed for the exploration of diverse network setups. The ability to create and manage virtual networks has not only saved money but also enriched my understanding of networking concepts and technologies.
To know more about virtual machines ,visit:
https://brainly.com/question/31674424
#SPJ11
Look in the nec® index and find uses permitted for ac cable. the code reference for this is ___.
Answers
If one Look in the nec® index and find uses permitted for ac cable. the code reference for this is installed in wet locations.
Where is the index located in the NEC?The index is known to be one that is seen or located in the back of the NEC and this is known to be one that is said to be organized in alphabetical order ranging from keywords seen within the electrical code.
Note that The index is seen to be the best reference for knowing multiple occurrences of a particular words and phases inside a lot of articles and sections of code.
Hence, If one Look in the nec® index and find uses permitted for ac cable. the code reference for this is installed in wet locations.
Learn more about code reference from
https://brainly.com/question/25817628
#SPJ1
Using a recursion tree, show the process how to solve the following recurrence in terms of the big O representation. Use the substitution method to prove your conclusion.
T(n) = 2T(n/3) + cn
Answers
To utilize a recursion tree in solving the recurrence relation T(n) = 2T(n/3) + cn.
The Recursion TreeCommence by initializing the topmost node that symbolizes T(n).
The initial node bifurcates into a pair of offsprings, symbolizing T(n/3).
The child nodes divide into two additional child nodes that depict T(n/9).
Carry out this procedure repeatedly until you arrive at the leaf nodes, which signify T(1).
The accumulated work completed at every stage is equivalent to cn.
The tree's height is determined by log base three of n.
To determine the overall work accomplished, the individual work executed at every level needs to be added together. This individual work is represented as cn multiplied by 2 raised to the power of log base 3 of n.
We can express it in a simpler form as cn multiplied by n raised to the power of the logarithm of 2 with a base of 3.
Let us consider the substitution method and suppose that T(n) does not exceed kn raised to the power of log base 3 of 2, where k is a constant.
By inserting this supposition into the sequence formula, we obtain T(n) ≤ 2(k(n/3)^(log₃(2))) + cn.
To make it more concise, we can write the upper bound for T(n) as (2/3)kn^(log₃(2)) + cn.
By selecting an appropriate value for k such that (2/3)kn^(log₃(2)) is less than or equal to cn for sufficiently large n, we can establish that T(n) is no greater than kn^(log₃(2)) for all values of n.
Consequently, the time complexity for T(n) can be expressed as O(n^(log₃(2))) based on this information.
Through the utilization of both the substitution method and the recursion tree, we have cleverly demonstrated that T(n)'s time complexity is bounded by O(n^(log₃(2))).
Read more about recursion tree here:
https://brainly.com/question/30425942
#SPJ4
How can I learn programming in mobile?
Answers
Answer:
You sadly cannot use your coding knowledge to complete things on mobile, but you can learn through YouTuube and Gooogle and such, and simple type it out in Gooogle docs or something. There are sadly no mobile friendly coding websites.
Hope This Helped!
how do you get your winkey wet??
Answers
Answer:
what
Explanation:
what
sorry but what
Answer:
what is a winkey.
Explanation:
How to block text messages from email addresses iphone?.
Answers
Answer:
Go to Settings -> Messages, scroll down to "Message Filtering" section and click into "Unknown & Spam". Enable "Filter Unknown Senders" and SMS Filtering.
Explanation:
This should turn off iMessage notifications if the text comes from addresses that are not in your contacts, unless you have replied to it.