You need to identify the manufacturer of a network interface. Where will you look for this information?The first three octets of a Media Access Control (MAC) addressThe last octet of a Media Access Control (MAC) addressThe first octet of a Media Access Control (MAC) addressThe fourth octet of a Media Access Control (MAC) address
Answers
To identify the manufacturer of a network interface. We will look to the first three octets of a Media Access Control (MAC). The correct option is a.
What is a network interface?The first six digits of a MAC address, known as OUI, are typically used to identify the manufacturer (Organizational Unique Identifier).
An Ethernet or network adapter over any given network is given a media access control address (MAC address), which is viewed as a distinctive identifier of sorts.
It should be noted that any of their registered vendors have received these MAC prefixes from the IEEE Registration Authority Committee. The rightmost six numbers stands for the Network Interface Controller.
Therefore, the correct option is a, The first three octets of a Media Access Control (MAC).
To learn more about network interface, refer to the link:
https://brainly.com/question/28207436
#SPJ1
Related Questions
Which of the following is NOT among the six factors needed to create a risk analysis?Select one:a. threatsb. probabilitiesc. consequencesd. personnel profiles
Answers
The answer to this question is d. personnel profiles. When conducting a risk analysis, there are six key factors that need to be considered in order to accurately assess and manage risks.
The answer to this question is d. personnel profiles. When conducting a risk analysis, there are six key factors that need to be considered in order to accurately assess and manage risks. These factors are threats, probabilities, consequences, vulnerabilities, impacts, and countermeasures. Threats refer to potential sources of harm or danger, while probabilities refer to the likelihood of those threats occurring. Consequences are the potential impacts or outcomes of a threat, while vulnerabilities refer to weaknesses or gaps in security measures. Impacts refer to the overall effect of a risk event, while countermeasures are the steps taken to prevent or mitigate risks. Personnel profiles, on the other hand, are not typically considered a key factor in risk analysis, as they do not directly relate to potential threats, probabilities, or consequences.
To know more about vulnerabilities visit: https://brainly.com/question/30296040
#SPJ11
The way things are arranged on a publication is referred to as the _____.
style
guides
layout
scheme
Answers
python
how do I fix this error I am getting
code:
from tkinter import *
expression = ""
def press(num):
global expression
expression = expression + str(num)
equation.set(expression)
def equalpress():
try:
global expression
total = str(eval(expression))
equation.set(total)
expression = ""
except:
equation.set(" error ")
expression = ""
def clear():
global expression
expression = ""
equation.set("")
equation.set("")
if __name__ == "__main__":
gui = Tk()
gui.geometry("270x150")
equation = StringVar()
expression_field = Entry(gui, textvariable=equation)
expression_field.grid(columnspan=4, ipadx=70)
buttonl = Button(gui, text=' 1', fg='black', bg='white',command=lambda: press(1), height=l, width=7)
buttonl.grid(row=2, column=0)
button2 = Button(gui, text=' 2', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button2.grid(row=2, column=1)
button3 = Button(gui, text=' 3', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button3.grid(row=2, column=2)
button4 = Button(gui, text=' 4', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button4.grid(row=3, column=0)
button5 = Button(gui, text=' 5', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button5.grid(row=3, column=1)
button6 = Button(gui, text=' 6', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button6.grid(row=3, column=2)
button7 = Button(gui, text=' 7', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button7.grid(row=4, column=0)
button8 = Button(gui, text=' 8', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button8.grid(row=4, column=1)
button9 = Button(gui, text=' 9', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button9.grid(row=4, column=2)
button0 = Button(gui, text=' 0', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button0.grid(row=5, column=0)
Add = Button(gui, text=' +', fg='black', bg='white',command=lambda: press("+"), height=l, width=7)
Add.grid(row=2, column=3)
Sub = Button(gui, text=' -', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
Sub.grid(row=3, column=3)
Div = Button(gui, text=' /', fg='black', bg='white',command=lambda: press("/"), height=l, width=7)
Div.grid(row=5, column=3)
Mul = Button(gui, text=' *', fg='black', bg='white',command=lambda: press("*"), height=l, width=7)
Mul.grid(row=4, column=3)
Equal = Button(gui, text=' =', fg='black', bg='white',command=equalpress, height=l, width=7)
Equal.grid(row=5, column=2)
Clear = Button(gui, text=' Clear', fg='black', bg='white',command=clear, height=l, width=7)
Clear.grid(row=5, column=1)
Decimal = Button(gui, text=' .', fg='black', bg='white',command=lambda: press("."), height=l, width=7)
buttonl.grid(row=6, column=0)
gui.mainloop()
Answers
Answer:
from tkinter import *
expression = ""
def press(num):
global expression
expression = expression + str(num)
equation.set(expression)
def equalpress():
try:
global expression
total = str(eval(expression))
equation.set(total)
expression = ""
except:
equation.set(" error ")
expression = ""
def clear():
global expression
expression = ""
equation.set("")
if __name__ == "__main__":
gui = Tk()
equation = StringVar(gui, "")
equation.set("")
gui.geometry("270x150")
expression_field = Entry(gui, textvariable=equation)
expression_field.grid(columnspan=4, ipadx=70)
buttonl = Button(gui, text=' 1', fg='black', bg='white',command=lambda: press(1), height=1, width=7)
buttonl.grid(row=2, column=0)
button2 = Button(gui, text=' 2', fg='black', bg='white',command=lambda: press(2), height=1, width=7)
button2.grid(row=2, column=1)
button3 = Button(gui, text=' 3', fg='black', bg='white',command=lambda: press(3), height=1, width=7)
button3.grid(row=2, column=2)
button4 = Button(gui, text=' 4', fg='black', bg='white',command=lambda: press(4), height=1, width=7)
button4.grid(row=3, column=0)
button5 = Button(gui, text=' 5', fg='black', bg='white',command=lambda: press(5), height=1, width=7)
button5.grid(row=3, column=1)
button6 = Button(gui, text=' 6', fg='black', bg='white',command=lambda: press(6), height=1, width=7)
button6.grid(row=3, column=2)
button7 = Button(gui, text=' 7', fg='black', bg='white',command=lambda: press(7), height=1, width=7)
button7.grid(row=4, column=0)
button8 = Button(gui, text=' 8', fg='black', bg='white',command=lambda: press(8), height=1, width=7)
button8.grid(row=4, column=1)
button9 = Button(gui, text=' 9', fg='black', bg='white',command=lambda: press(9), height=1, width=7)
button9.grid(row=4, column=2)
button0 = Button(gui, text=' 0', fg='black', bg='white',command=lambda: press(2), height=1, width=7)
button0.grid(row=5, column=0)
Add = Button(gui, text=' +', fg='black', bg='white',command=lambda: press("+"), height=1, width=7)
Add.grid(row=2, column=3)
Sub = Button(gui, text=' -', fg='black', bg='white',command=lambda: press("-"), height=1, width=7)
Sub.grid(row=3, column=3)
Div = Button(gui, text=' /', fg='black', bg='white',command=lambda: press("/"), height=1, width=7)
Div.grid(row=5, column=3)
Mul = Button(gui, text=' *', fg='black', bg='white',command=lambda: press("*"), height=1, width=7)
Mul.grid(row=4, column=3)
Equal = Button(gui, text=' =', fg='black', bg='white',command=equalpress, height=1, width=7)
Equal.grid(row=5, column=2)
Clear = Button(gui, text=' Clear', fg='black', bg='white',command=clear, height=1, width=7)
Clear.grid(row=5, column=1)
Decimal = Button(gui, text=' .', fg='black', bg='white',command=lambda: press("."), height=1, width=7)
Decimal.grid(row=6, column=0)
gui.mainloop()
Explanation:
I fixed several other typos. Your calculator works like a charm!

How can a user change the range of cells that a Conditional Formatting rule applies to?
A: Clear the rule first and reapply it as it cannot be modified.
B: In the Conditional Formatting Rules Manager dialog box, edit the cell range for the rule in the Applies To section.
C: Clear all rules that have been applied to the worksheet or selected range by clicking on the Clear Rules button.
D: Right-click the cell range and select Update Conditional Formatting Rule from the menu list.
Answers
Answer:
B: In the Conditional Formatting Rules Manager dialog box, edit the cell range for the rule in the Applies To section.
Explanation:
Conditional formatting rule: The term "conditional formatting rule" is described as a technique that allows an individual to apply formatting automatically, for example, data bars, colors, and icons, etc., to one or more than one cells on the basis of the cell value.
Example: If the value is more than $3000, color the cell blue.
In the question above, the correct answer is option-B.
Answer:
B
Explanation:
lab 6 write a program to input names and addresses that are in alphabetic order and output the names and addresses in zip code order. you could assume maximum of 50 names. the program should be modalized and well documented. you must: 1. use a structure for names and address information 2. allocate storage dynamically for each structure (dynamic memory allocation) 3. use input/output redirection 4. use an array of pointers to structures; do not use an array of structures 5. use multiple file format; header file, multiple .c files 6. sort the zip codes in ascending order 7. use the data file assigned
Answers
Implementing this program requires detailed coding, handling file input/output, dynamic memory allocation, sorting algorithms, and proper error handling. It's recommended to consult programming resources, documentation, or seek guidance from a programming instructor or community to ensure accurate implementation.
Certainly! Here's a step-by-step explanation for implementing the program you described:
Define a structure to hold the name and address information, including the zip code.Use dynamic memory allocation to allocate memory for each structure as names and addresses are inputted from the file.Read the names and addresses from the input file, storing them in the dynamically allocated structures.Create an array of pointers to the structures, with each pointer pointing to a structure.Implement a sorting algorithm (such as bubble sort or merge sort) to sort the array of pointers based on the zip codes in ascending order.Use input/output redirection to read from the input file and write to the output file.Create separate header and source files for modularization, placing the structure definition, function prototypes, and shared constants in the header file, and the function implementations in separate .c files.Open the assigned data file, call the necessary functions to perform the sorting and outputting, and then close the files.Remember to include appropriate error handling, such as checking file openings and memory allocations, to ensure the program runs smoothly and handles potential errors gracefully.
For more such question on dynamic memory allocation
https://brainly.in/question/55000065
#SPJ8
which type of wireless network utilizes the 5 ghz frequency band and reaches speeds of up to 3.5 gbps? network
Answers
The type of wireless network that utilizes the 5 GHz frequency band and reaches speeds of up to 3.5 Gbps is known as 802.11ac.
802.11ac is a wireless networking standard that operates on the 5 GHz frequency band.
It is designed to provide faster data transfer rates, reaching speeds of up to 3.5 Gbps.
This makes it ideal for high-bandwidth applications such as video streaming and online gaming.
802.11ac uses multiple antennas and beamforming technology to improve signal strength and reliability.
It is backward compatible with older 802.11a/b/g/n standards but requires compatible hardware to achieve the full potential of its speed and range.
To know more about wireless network visit:
brainly.com/question/31630650
#SPJ11
Should I get the skull ranger skin?
Answers
Answer:
No, Skull Ranger was released in preparation for the 2018 Halloween and features some unlockable designs. ... It is worth noting that Skull Ranger does not unlock the Skull Trooper Challenges.
Explanation:
ITS NOT WORTH IT NO ONE PLAYS FORTNITE ANYMORE. FORTNITE IS DEAD, ITS A WASTE OF MONEY :)
Consider the following command:ip route 192.168.10.0 255.255.255.0 10.10.10.2 5Which route would have to go down in order for this static route to appear in the routing table?a static route to the 192.168.10.0/24 networkRefer to curriculum topic:
Answers
The command "ip route 192.168.10.0 255.255.255.0 10.10.10.2 5" adds a static route to the 192.168.10.0/24 network with a metric of 5. No other route needs to go down for this static route to appear in the routing table.
The given command adds a static route to the routing table with a metric of 5, which indicates the preference of the route. If there is already a route to the same network with a lower metric, it will take precedence over this static route. However, if there is no existing route to the 192.168.10.0/24 network or if the existing route has a higher metric, then this static route will appear in the routing table immediately without requiring any other route to go down.
Learn more about routing table here:
https://brainly.com/question/31605394
#SPJ11
you are configuring the local security policy of a windows system. you want to prevent users from reusing old passwords. you also want to force them to use a new password for at least five days before changing it again. which policies should you configure? (select two.)
Answers
Since you are modifying a Windows system's local security policy. The policies you need to set up are:
Password history enforcementMinimum age for passwords.Explain the local security policy for windows system?A system's local security policy is a collection of data on the safety of a local computer.
The following information is part of the local security policy: the trusted domains for logon attempt authentication. How and which user accounts can access the system.It is well known that Minimum Password Age policy defines the minimum amount of time that users must hold onto a password without changing it. Users won't be able to use a new password, change it to an old one, and afterwards bypass the password system if there is a minimum password age requirement.Thus, if you are changing the local security settings on a Windows system. The regulations you must establish are:
enforces the history of passwordsAge restriction for passwords.To know more about the windows operating system, here
https://brainly.com/question/1763761
#SPJ4
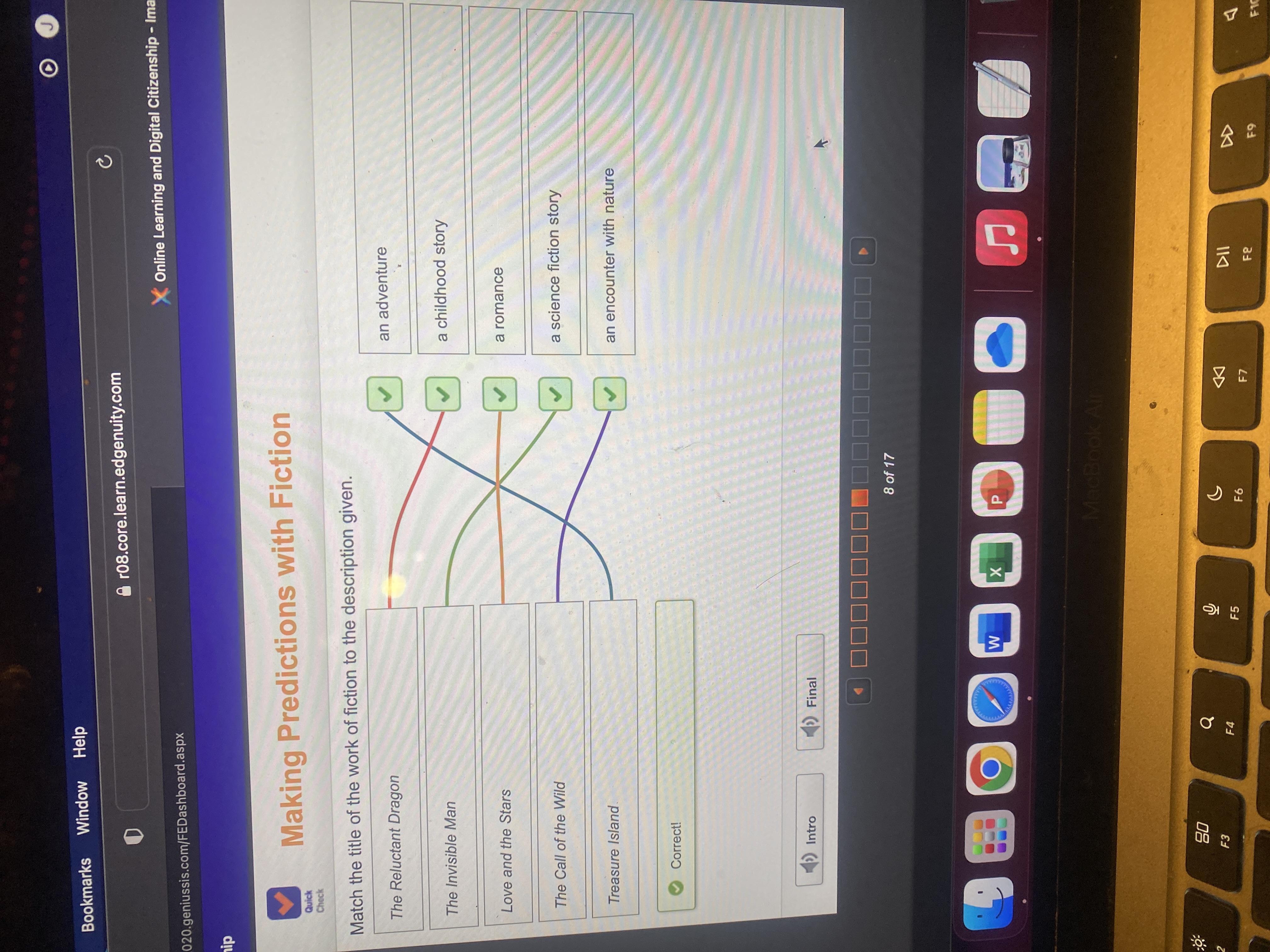
Match the title of the work of fiction to the description given.

Answers
Answer:
Explanation:
Let's get the ones that there is no dispute.
Love and the Stars Romance
The Invisible Man Science Fiction
Treasure Island An Adventure
Call of the Wild An encounter with Nature
Reluctant Dragon Childhood story.
Here's the problem.
Most ten year olds are children. They likely would like both Call of the Wild and the Reluctant Dragon as well as Treasure Island.
The Reluctant Dragon could be called science fiction.
Answer:
your welcomeee
Explanation:
Were the colonists loyal to the British king after the war began? WILL GIVE BRANLEST PLS ASAP
Colonists were loyal to the French once the American Revolution began.
Colonists were never loyal to the king, so the war didn’t change anything.
There was no more British loyalty in the American colonies once the war began.
The colonists still felt loyalty for their king even after the start of the war.
Answers
Answer:
There was no more British loyalty in the American colonies once the war began.
Explanation:
The American Revolution began in 1775 as a response to the absolutist policies imposed by King George of Great Britain, specifically in economic and political matters, on the Thirteen Colonies and their citizens.
During the reign of King George, many civil, political and economic freedoms were suppressed (through the Intolerable Acts and other similar regulations), with which popular support for the monarchy was gradually losing size. Thus, new liberal ideologies began to appear, based on the postulates of philosophers such as John Locke or Jean Jacques Rousseau, who promoted the freedom of the individual and the respect of their natural rights as the fundamental premises of social organization.
For this reason, at the time of the Revolution, most of the settlers were pro-independence, while small minorities continued to support Great Britain. Precisely, these minorities, after the advance of the armed conflict, began to move towards what is now Canada, which continued to be a British stronghold.
Answer:
The colonists still felt loyalty for their king even after the start of the war.
Explanation:
Loyalists were American colonists who remained loyal to the British Crown during the American Revolutionary War, often referred to as Tories, Royalists or King's Men at the time. They were opposed by the Patriots, who supported the revolution, and called them "persons inimical to the liberties of America."
Help this toddler┐(´ー`)┌

Answers
Mainframe Computer is the powerful supercomputer which is capable of great processing and huge data storing tasks.
Also note: they are pretty really huge in size and varies- contains many fast processors, storage space and operate banking sites and transactions.
Example of such computers - IBM
They are costly and operated by huge companies.
Answer:
mainframeExplanation:
hope it helps you
which of the following purposes do wireless site surveys fulfill? (select two.) answer identify the recommended 100 degree separation angle for alternating access points. document existing infrared traffic in the 5.4 ghz spectrum. determine the amount of bandwidth required in various locations. identify the coverage area and preferred placement of access points. identify existing or potential sources of interference.
Answers
The physical examination of a location where a wireless radio frequency (RF) network will be built is known as a wireless site survey.
What is a wireless site survey?In order to measure wireless coverage, data rates, network capacity, roaming capability, and service quality, the study evaluates the surrounding environment.In order to identify where your signal will be strongest and weakest, it is important to display the wireless coverage areas (often using heatmaps).Additional names include WLAN site surveys, wireless network surveys, RF site surveys, and networking site surveys.In other words, a survey is carried out to make sure your company makes the most of your wireless network and ultimately saves you money (and aggravation).Any setting, including a warehouse, office, hospital, hotel, or school, is suitable for site surveys.The two main goals are:identifying RF coverage and interference areasChoosing where to put access points.To Learn more About wireless site survey refer To:
https://brainly.com/question/15681936
#SPJ1
Who is famous for his three laws of robotics?
Answers
Answer:
The Correct answer is Isaac Asimov
Explanation:
Science fiction already envisioned this problem and has suggested various potential solutions. They were designed to prevent robots harming humans.
There are numerous strict and steadfast rules when it comes to composition.
answers:
true
false
Answers
Answer:
false
Explanation:
none ¯\_(ツ)_/¯
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive File Definition
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option. The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files athttps://brainly.com/question/15355917.
#SPJ4
in a windows environment what command would you use
Answers
Answer:
Basic CMD Commands
Explanation:
Some examples include:
1. Assoc
2. Cipher
3. File Compare
4. Ipconfig
5. Netstat
6. Ping
7. PathPing
8. Tracert
In a Windows environment, there are various commands you can use depending on what you want to accomplish. Here are a few commonly used commands:
dir: Lists the files and directories in the current directory.
cd: Changes the current directory.
mkdir: Creates a new directory.
copy: Copies files from one location to another.
del: Deletes files.
ren: Renames a file or directory.
ipconfig: Displays the IP configuration of the computer.
ping: Tests network connectivity to a specific IP address or domain.
tasklist: Lists all running processes.
shutdown: Shuts down or restarts the computer.
Learn more about commands, here:
https://brainly.com/question/30067892
#SPJ6
What is the most commonly used tab in the Filter dialog box?
x Advanced
O Messages
O More Choices
O SQL
Answers
The answer is Messages

Answer:
B. Messages
Explanation:
Just did the assignment
a router on the border of your network detects a packet with a source address from an internal client, but the packet was received on the internet-facing interface. which attack form is this an example of?
Answers
Attack form is this an example of spoofing.
What is Spoofing?A common spoofing scenario occurs when an email is sent from a spoofed sender address and the recipient is asked to provide confidential information. Recipients are typically asked to click a link to log into their account and update their personal and financial information. Spoofing is a cybercrime that occurs when someone pretends to be a trusted contact or brand to gain access to sensitive personal information while impersonating a trusted person. Spoofing attacks copy identity, the appearance of a name brand, or the address of a trusted website.
Learn more about spoofing: https://brainly.com/question/23021587
#SPJ4
Which range of cells represents the Lookup Table for finding which award each student received? Which lookup function would you use to fill C2:C7? What is your lookup value for student C?.
Answers
To find award of each student recieved we use VLOOKUP function.
What is VLOOKUP Function ?VLOOKUP stated as 'Vertical Lookup' is a simplest functional form that makes excel to search a certain value in the column ie. Table Array in order to return values from different columns in that same row.
We use VLOOKUP when we need to find values in table or a range by given row.
Learn more about VLOOKUP here :https://brainly.com/question/14042837
Answer: First one is A (E7:F12)
Second one is Vlookup
Third one is 6
Explanation:
Just did the class in Alt Ed, sorry im late
What is one way hackers can trick you into transmitting personal data over on a public network without your knowledge
Answers
You have an unsorted array of 1,000,000
people.
You are using a Linear Search to look for
someone who is not in the array at all.
How many people does the computer look at
before it realizes this person is not in the array?
O a
b
Ос
Od
(a)exactly 1
(b)about 500,000
(c)all 1,000,000
(d) it will search forever
(d)It will search forever.
Answers
What technology standard is commonly used today for hard drives to interface with the motherboard in a system? pasago po salamat ^_^
Answers
Answer:
Serial Advanced Technology Attachment (SATA).
Explanation:
The hardware component of a computer can be defined as the physical parts or peripherals that enables it to work properly. Thus, the hardware components of a computer are the physical parts that can be seen and touched. Some examples of hardware components are monitor, speaker, central processing unit, motherboard, hard-drive, joystick, mouse, keyboard, etc.
Digital storage of data refers to the process which typically involves saving computer files or documents on magnetic storage devices usually having flash memory. Some examples of digital storage devices are hard drives, memory stick or cards, optical discs, cloud storage, etc. A reliable storage such as a hard-disk drive ensures that computer files or documents are easily accessible and could be retrieved in the event of a loss.
Serial ATA (SATA) is a technological standard which is commonly used today for hard drives to interface with the motherboard in a computer system. Thus, it's simply a bus interface on computer systems that is typically used for connecting mass storage devices to host bus adapters such as motherboards.
Generally, SATA comprises of two ports and these are the power and data connector.
In cell a10 enter a formula using or to display true if net profit before tax in 2019 (cell b5) are greater than 750000(seven hundred, fifty thousand) or net profit before tax in 2020 (cell c5) are greater than 750000 (seven hundred, fifty thousand). use cell references where appropriate and enter the arguments exactly as described in this question.
Answers
The OR Excel function is a function that is used to test several conditions in one statement.
The Excel formula to display true based on the conditions in cell A10 is =OR(B5>750000,C5>750000)
From the question, we have:
Cell B5 represents the net profit before tax in 2019Cell C5 represents the net profit before tax in 2020The syntax of the OR logical function is: =OR([conditions])
So, the Excel formula to display true based on the conditions in cell A10 is =OR(B5>750000,C5>750000)
Read more about Excel formulas at:
https://brainly.com/question/14820723
once editing is complete, a file is normally:
A. saved as a raw file
B. converted to a PDF
C: exported
D: feathered
Answers
Answer:
I would guess C) Feathered
Explanation:
hope this helped!
have a great weekend
saved as a raw file.
Explanation:
How do you implement instruction level parallelism
Answers
Answer:
To obtain substantial performance enhancements, we must exploit ILP across multiple basic blocks.
Explanation:
the built-in object class . question 24 options: is the base class for most, but not all, classes defines multiple methods including tostring() and equals() is derived from class super defines tostring() and no additional methods
Answers
The base class for most classes, but not all, typically defines several methods, including toString() and equals(). It is derived from the superclass, which defines toString() and does not have any additional methods.
In object-oriented programming, a base class serves as a template or blueprint for other classes to inherit from. Most classes in a program usually derive from a common base class, although there may be exceptions. The base class often provides common functionality or attributes that are shared among its derived classes. One common practice in many programming languages is to include certain methods in the base class that are applicable to most derived classes. Two commonly included methods are toString() and equals(). The toString() method is responsible for providing a string representation of the object, which is useful for debugging or displaying the object's state. The equals() method is used to compare two objects for equality.
The base class, being the superclass, itself inherits from another class, known as the super. In this case, the superclass defines the toString() method but does not introduce any additional methods. Therefore, when the base class is derived from the superclass, it inherits the toString() method and does not have any extra methods of its own. It's important to note that the specifics may vary depending on the programming language and the design choices made in a particular system. However, the concept of a base class with common methods, derived from a superclass that provides the toString() method, is a common pattern in object-oriented programming.
To learn more about object-oriented programming, click here: brainly.com/question/28732193
#SPJ11
How many tens are there in the number 156?
A. 1
B. 15
C. 6
D. 56
Answers
Answer:
15
Explanation:
15 times 10 is 150, therefore there is 15 tens inside 156.
Answer:
15
Explanation:
Did you know, Death is the leading cause of Death?
There are many different risk factors that can drastically increase the likelihood of Death. Some risk factors can be: Jumping off cliffs, getting a heart attack, getting run over by a car, getting a stroke, and getting shot in the head.
2. In many jurisdictions a small deposit is added to containers to encourage people to recycle them. In one particular jurisdiction, containers holding one litre or less have a $0.10 deposit, and containers holding more than one litre have a $0.25 deposit. Write a Python script that reads the number of containers of each size from the user. The script should compute and display the refund that will be received for returning those containers. Format the output so that it includes a dollar sign and displays exactly two decimal places.
Answers
Answer:
Here is the Python program:
small_container = int(input("Enter the number of small containers you recycled?"))
large_container = int(input("Enter the number of large containers you recycled?"))
refund = (small_container * 0.10) + (large_container * 0.25)
print("The total refund for returning the containers is $" + "{0:.2f}".format(float(refund)))
Explanation:
The program first prompts the user to enter the number of small containers. The input value is stored in an integer type variable small_container. The input is basically an integer value.
The program then prompts the user to enter the number of large containers. The input value is stored in an integer type variable large_container. The input is basically an integer value.
refund = (small_container * 0.10) + (large_container * 0.25) This statement computers the refund that will be recieved for returning the small and larger containers. The small containers holding one litre or less have a $0.10 deposit so the number of small containers is multiplied by 0.10. The large containers holding more than one litre have a $0.25 deposit so the number of large containers is multiplied by 0.25. Now both of these calculated deposits of containers of each side are added to return the refund that will be received for returning these containers. This whole computation is stored in refund variable.
print("The total refund for returning the containers is $" + "{0:.2f}".format(float(refund))) This print statement displays the refund in the format given in the question. The output includes a $ sign and displays exactly two decimal places by using {0:.2f} where .2f means 2 decimal places after the decimal point. Then the output is represented in floating point number using. format(float) is used to specify the output type as float to display a floating point refund value up to 2 decimal places.

The required code which calculates the amount of refund made by returning the containers written in python 3 goes thus :
small_size = eval(input('Enter number of 1L or less containers to be returned: '))
#prompts user to enter the number of small sized containers to be returned
big_size = eval(input('Enter number of containers greater than 1L to be returned: '))
#prompts user to enter the number of big size containers to be returned
small_refund = (small_size * 0.10)
#calculates the total refund on small sized containers
big_refund = (big_size * 0.25)
# calculates the total refund on big size containers
total_refund = float((small_refund + big_refund))
#calculates the Cummulative total refund
print('Your total refund is $' + '{0:.2f}'.format(total_refund))
#displays the total refund rounded to 2 decimal places.
Learn more :https://brainly.com/question/14353514

complete the sentence: hexadecimal numbers use base ____
Answers
Hexadecimal numbers use base-16