Continuity errors are always going to happen because it’s impossible to catch every mistake before releasing a finished movie?
Answers
Yes, continuity errors are common in movies because it's challenging to catch every mistake before the film's release. While efforts are made to minimize them, some errors inevitably slip through.
Continuity errors occur when there is a lack of consistency in elements such as props, costumes, or settings within a movie. These inconsistencies can result from various factors, including human oversight, budget constraints, or time limitations during filming. Directors, editors, and script supervisors work together to maintain continuity throughout the production process, but even with their best efforts, some errors may still go unnoticed.
Several factors contribute to the prevalence of continuity errors:
1. Multiple takes: Actors perform scenes several times, which may cause slight variations in their positions or actions. Combining different takes in the editing process can lead to discrepancies.
2. Filming out of sequence: Movies are rarely shot in chronological order. Scenes may be filmed weeks or months apart, making it difficult to maintain perfect continuity.
3. Changes in script or set design: Alterations to the script or set during production can introduce inconsistencies if not carefully managed.
4. Human error: Despite having dedicated professionals working on set, mistakes can still happen.
5. Time and budget constraints: Limited resources may prevent filmmakers from reshooting a scene to fix a continuity error.
Ultimately, while filmmakers strive to achieve seamless continuity, it's nearly impossible to catch every single mistake before a movie's release. However, many viewers enjoy spotting these errors, and they rarely detract from the overall film experience.
Know more about the production process click here:
https://brainly.com/question/28313605
#SPJ11
Related Questions
To use an outline for writing a formal business document, what should you do
after entering your bottom-line statement?
OA. Move the bottom-line statement to the end of the document.
OB. Write a topic sentence for every detail.
C. Enter each supporting detail from the outline on a separate line.
D. Enter each major point from the outline on a separate line.
Answers
To enter your bottom-line statement you
C. Enter each supporting detail from the outline on a separate line.
How to add bottom-line statementAfter entering your bottom-line statement in an outline for writing a formal business document, you should enter each major point from the outline on a separate line This means that you should write down the key ideas that support your bottom-line statement and each idea should be placed on its own line to clearly differentiate them These major points will become the topic sentences for each section of your document
Once you have entered each major point on a separate line you can then enter each supporting detail from the outline on a separate line under its corresponding major point This helps to organize the information in a logical manner and allows you to expand on each major point in a structured and cohesive way
Learn more about bottom-line statement at
https://brainly.com/question/8630249
#SPJ1
What is a user data?
Answers
Answer: Any data the user creates or owns.
Explanation:
the user being the one on the otherside of the computer, usually a human.
but examples of user data are intalled programs, uploads, word documents created by user (computer user)
Describe a feature of a receptionist and explain how she deals with external customers.
Answers
Answer:
A receptionist is a (administrator) who deals with tasks such as, answering a phone call, and giving information to customers. They deal with external customers by letting them talk and not interrupting them..
which term refers to taking the hardware of the host system and segmenting it into individual virtual machines?
Answers
The term that refers to taking the hardware of the host system and segmenting it into individual virtual machines is virtualization.
Virtualization refers to the creation of a virtual version of something, such as hardware platform, operating system, a storage device, or network resources, among other things. The hardware of a host system is referred to as a physical machine.
Virtualization is the method of taking that hardware and dividing it into individual virtual machines.In the realm of computer systems, virtualization refers to the creation of a virtual machine that can run as if it were an actual computer. This virtual machine can operate its own software and applications, as well as run an independent operating system.
Virtualization is beneficial for many reasons, including security, cost savings, and ease of use.
To learn more about "Virtualization" visit: https://brainly.com/question/23372768
#SPJ11
What is the effect of small to moderate amounts of cortisol on structures involved in memory?
Answers
Significant increases in cortisol reactivity to a psychosocial stressor were associated with declarative memory deficits.
What is cortisol?Cortisol is a steroid hormone produced and released by your adrenal glands, which are located on top of your kidneys. Cortisol influences several aspects of your body, primarily regulating your body's response to stress.
Massive gains in cortisol excitability to a psychosocial stressor have been affiliated with declarative memory deficits.
Similarly, elevated cortisol levels have been linked to poor memory performance and decreased hippocampal volume in a sample of healthy older adults.
Thus, this is the effect of small to moderate amounts of cortisol on structures involved in memory.
For more details regarding cortisol, visit:
https://brainly.com/question/16288547
#SPJ4
How many screws secured the side panels
Answers
The answer to this question may significantly vary but normally there are two screws for each on each side of the panel on a mid-tower case.
What is the function of Screws?The function of screws is to tighten the parts which are arranged in a complex arrangement. A Screw is a type of simple machine which visualize like an inclined plane that wounded around a complex arrangement with a pointed tip.
According to this question, very frequently there are two screws that can be secured to the side panels but there can be anywhere from one to six screws for the case is also seen in some kinds of systematic arrangements.
Therefore, the answer to this question may significantly vary but normally there are two screws for each on each side of the panel on a mid-tower case.
To learn more about Screws, refer to the link:
https://brainly.com/question/9620666
#SPJ1
how to use a while loop in pascal for 36 students
Answers
The initial step is executed first and only.This step allows you to declare and initialize any loop control variables.
Next the conditions is evaluated.
After the body of the for-do loop executes the value of the variable is either increased or decreased.
The condition is now evaluated again.
Some one help pls will mark brainless !!!!!
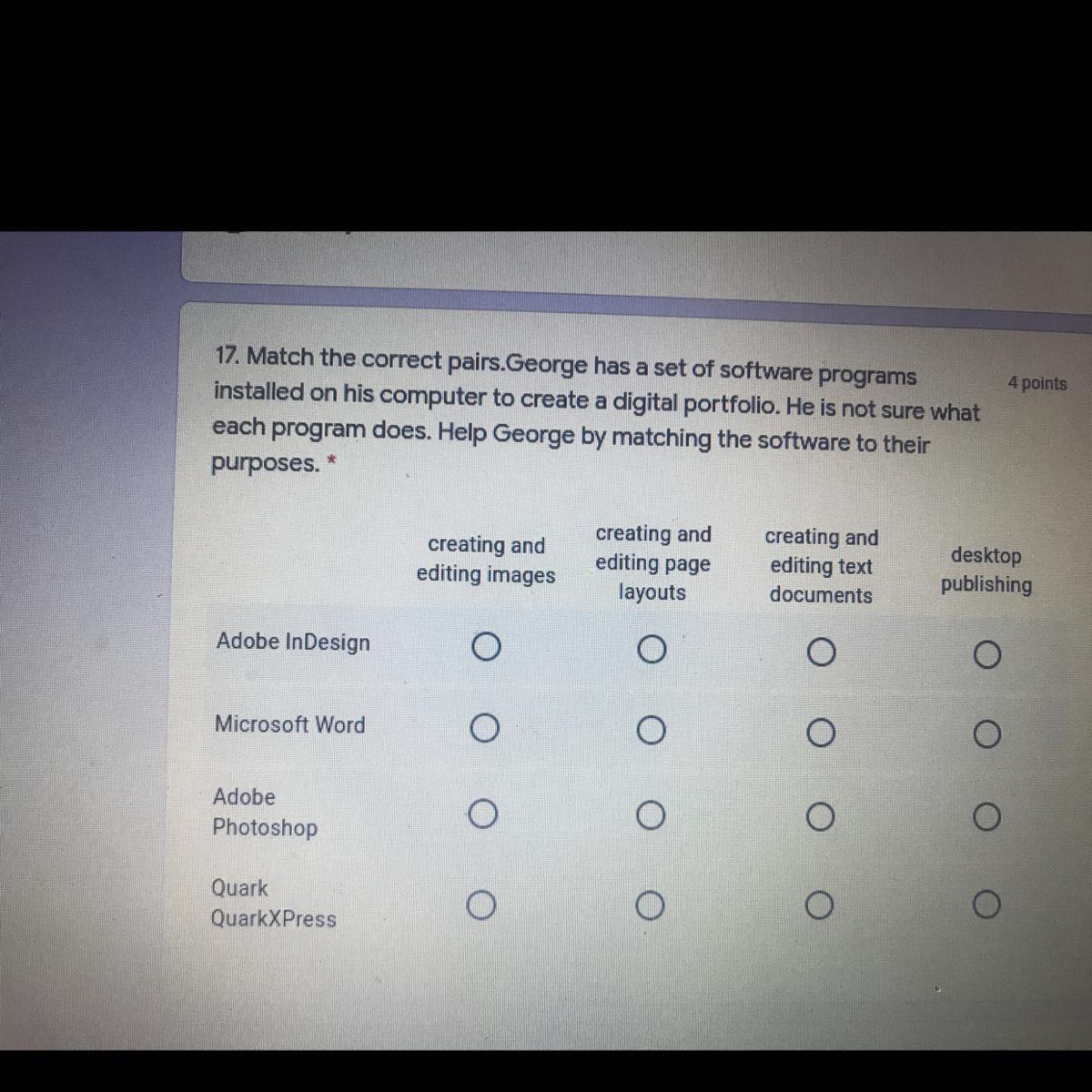
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
There isnt a photoshop catagory for this but I was wondering if anyone knows the answer to this. Thank you guys! ^-^

Answers
Answer:
Hi, there I'm currently certified in Photoshop and recently I pass Adobe Illustrator
Explanation:
The last one with red blue and yellow is primary
The first one Secondary
The second one is Tertiary
Hope this helps :)
Answer:
hey Lori its been a while I miss you. can we talk again?
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
Q4. Create an HTML page with following specifications:
1) Title should be about myCity
2) Place your City name at the top of the page in large text and in blue color
3) Add names of landmarks in your city each in a different color, style and typeface One of the landmark
4) Yourschool name should be blinking
5) Add scrolling text with a message of your choice
Answers
The example of an HTML page that meets your specificationsin regards to Title should be about myCity, and others is given in the code attached.
What is the HTML page?The <title> tag is used to tell the browser what name to show at the top of the page. The <style> tag is where you can put rules for CSS, which is used to style things on your HTML page.
Therefore, The <h1> tag with the class name "city-name" is used to show the city name at the top of the webpage. The text says that in the CSS section, there is a class which has a big font size of 32 and blue color.
Learn more about HTML page from
https://brainly.com/question/4056554
#SPJ1


VM sprawl is a general term describing the propagation of virtual systems across the enterprise in an uncontrolled way. Rogue machines can consume resources and bandwidth as well as present new vulnerabilities with virtual machines that are not being patched and monitored. Forensics cannot be conducted in the virtual environment in which these machines aren't even visible to the organization. Should an event occur, organizations need to not only know what part of the network is affected, but also be able to roll back network and system records in time to determine what happened.:
Answers
VM sprawl refers to the uncontrolled propagation of virtual systems in an organization, leading to resource consumption, security vulnerabilities, and difficulties in conducting forensics. To address this issue, organizations should implement proper management practices, including provisioning and decommissioning policies, centralized monitoring tools, and regular patching. Logging and auditing mechanisms should be in place to enable effective forensics and investigation in the event of an incident.
By maintaining control over virtual systems and implementing proactive management, organizations can mitigate the risks associated with VM sprawl and ensure the stability and security of their network. Additionally, adopting virtualization management tools and implementing automated processes can help organizations track and manage virtual machines more effectively, reducing the chances of sprawl and ensuring better resource utilization and security.
Learn more about VM sprawl here
https://brainly.com/question/32679969
#SPJ11
What is the 1st operation that is calculated in a formula?

Answers
Answer:
i think the second one
These are used to section the hair to make application of the color easier.
Answers
Answer:
Sectioning Clips
Explanation:
These are used to make segments or sections in the hair so that applying the color will be easier
data analyst is working with a data frame named salary data. they want to create a new column named wages that includes data from the rate column multiplied by 40. what code chunk lets the analyst create the wages column? 1 point mutate(salary data, wages
Answers
The Data analyst can use the modify() function to add a new column named hourly salary that represents hourly wages divided by 40. Without altering any already-existing columns, the modify() function can add a new column.
In R programming, we can add additional variables to the supplied data frame by using the mutate() method. By carrying out the actions on the current variables, these new variables are added.
You must to install the dplyr library before using the mutate() function. The mutate() function allows you to add new variables while keeping the current variables in a data frame intact. The basic syntax for mutate() is as follows.
data <- mutate(new_variable = existing_variable)
new variable: the name of the new variable data: the new data frame where the new variables will be placed existing The current data frame variable that you want to change to create a new variable is denoted by the symbol _variable.
To learn more about Data analyst click here:
brainly.com/question/29516581
#SPJ4
The negotiation process involves several steps such as: preparing for negotiation; knowing your walk-away point; and working towards a common goal.
Answers
Answer:
TRUE
Explanation:
Negotiation may be defined as the process or a method with the help of which people try to settle their differences or they try to come to a conclusion in a matter of differences. Here an agreement or a compromise is reached without any dispute and arguments. It is a skill.
It involves preparing for the negotiation with other person, understanding and knowing when one needs to walk out of the negotiation process to avoid arguments and working towards the common goal of achieving an agreement.
Therefore, the answer is true.
Why would you get the error, "InnerHTML" cannot be defined as null. In the developer console?
Answers
Answer:
you have not defined your innerHTML
Explanation:
you need to define it in order for it to work
Answer:
you have not defined your innerHTML
Explanation:
you need to define it in order for it to work
Write a program that creates a 4 x 5 array called numbers. The elements in your array should all be random numbers between -30 and 30, inclusive. Then, print the array as a grid.
For instance, the 2 x 2 array [[1,2],[3,4]] as a grid could be printed as:
1 2
3 4
Sample Output
18 -18 10 0 -7
-20 0 17 29 -26
14 20 27 4 19
-14 12 -29 25 28
Note: the numbers generated in your program will not match the sample output, as they will be randomly generated.
I cant seem to get this code..
Answers
Here's an example Python code that generates a 4 x 5 array of random numbers between -30 and 30 and prints it as a grid:
python
Copy code
import random
# create a 4 x 5 array called numbers
numbers = [[random.randint(-30, 30) for j in range(5)] for i in range(4)]
# print the array as a grid
for i in range(4):
for j in range(5):
print(numbers[i][j], end=' ')
print()
This code first imports the random module to generate random numbers. It then creates a 4 x 5 array called numbers using a nested list comprehension that generates random integers between -30 and 30 for each element of the array. Finally, it prints the array as a grid using nested loops, with each element separated by a space and each row on a new line.
Learn more about python here:
https://brainly.com/question/14378173
#SPJ11
I need help with this question. asap please

Answers
Answer:
what are you talking about
Explanation:
can you help me with my question

james needs to log all kernel messages tha have a severity level or warning or higher to separate log file. what faciiltiy and priority setting should he use
Answers
To log all kernel messages with a severity level of warning or higher to a separate log file, James should use the "kern" facility and "warning" priority setting. This will ensure that only relevant messages are logged in the separate file.
To log all kernel messages with a severity level of warning or higher to a separate log file, James should configure the syslog daemon to use the "kern" facility and a priority level of "warning" or higher.The facility is used to specify the type of system message that is being logged, and the "kern" facility is used specifically for kernel messages. The priority level determines the severity of the message, with levels ranging from "emergency" (highest severity) to "debug" (lowest severity). James needs to log messages with a severity level of "warning" or higher, so he should set the priority level to "warning" or above.
Learn more about kernel here
https://brainly.com/question/17162828
#SPJ11
Under what circumstances will the indented line of code immediately after an if statement be executed?
if the condition is false
if the condition is true
if the line begins with a #
if the line contains a variable
Answers
Answer:
The answer is "if the condition is true ".
Explanation:
In this question, the third choice is correct because the IF statement will help in making decisions, and it also controls a judgement of the program according to the attribute specified. The IF statement operates a collection if a provided condition is fulfilled or FALSE are assessed by some other set of protocols.
Answer:
The answer is B i did the test got it right so he/she is correct
have a good day hope this helped :)
Explanation:
you have been given a laptop to use for work. you connect the laptop to your company network, use the laptop from home, and use it while traveling. you want to protect the laptop from internet-based attacks. which solution should you use? answer vpn concentrator
Answers
If you've been given a laptop to use for work, connected it to your company network, and plan to use it while traveling and from home, it's crucial to protect the laptop from internet-based attacks. A VPN concentrator is a solution that you can employ to achieve this protection.
A VPN concentrator is a type of device that is employed to provide remote access to a company's private network. It allows for secure access to the network via an encrypted VPN tunnel. Remote users may use a VPN concentrator to connect to the company's network via the internet.
To provide secure access to the network, the VPN concentrator requires authentication, encryption, and additional security features. As a result, using a VPN concentrator can help to protect the laptop from internet-based attacks.
You can learn more about VPN concentrators at: brainly.com/question/12751054
#SPJ11
Select a good design recommendation for text hyperlinks.
a. Create the entire sentence as a hyperlink.
b. Include the works "Click here" in your text.
c. Use a key phrase as a hyperlink.
d. none of the above
Answers
The good design recommendation for text hyperlinks is to use a key phrase as a hyperlink (Option C).
Using a key phrase as a hyperlink is more descriptive and informative to users than just generic text such as "click here" or an entire sentence as a hyperlink. It also helps with search engine optimization by making the link more relevant to the content it points to.
Creating the entire sentence as a hyperlink (Option A) can be overwhelming and distracting for users. Including "Click here" in your text (Option B) can also be confusing and lacks context. None of the above (Option D) is not a good design recommendation as there is a clear answer to the question.
Option C is correct answer.
You can lerrn more about hyperlinks at
https://brainly.com/question/17373938
#SPJ11
Omar wants to research additional information about asteroids. Complete the sentences to describe how he should use the Smart Lookup feature in PowerPoint. Step 1: He should ____________ the word asteroid. Step 2: He should navigate to the _________ tab. Step 3. He should go to the __________ command group. Step 4: He should turn on the Intelligent Services of PowerPoint in the pane. Step 5: He should click the ________ option to open links that contain information about asteroids. Please answer quickly! It is quite urgent
Answers
Answer:
Step 1: He should
✔ select
the word asteroid.
Step 2: He should navigate to the
✔ Review
tab.
Step 3. He should go to the
✔ Insights
command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the
✔ Explore
option to open links that contain information about asteroids.
Explanation:
Edg2020
Omar should use the Smart Lookup feature in PowerPoint in several steps 1. Select, 2. Review, 3. Insights, 4. Explore.
What is the Smart Lookup feature in PowerPoint?The new Smart Lookup feature in PowerPoint 2016 for Windows is an option that shows up definitions, images, and other results from various online platforms about a word or phrase, right within PowerPoint.
There are four steps to use the Smart Lookup feature in PowerPoint:
Step 1: He should select the word asteroid.
Step 2: He should navigate to the Review tab.
Step 3. He should go to the Insights command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the Explore option to open links that contain information about asteroids.
Therefore, he should use 1. Select, 2. Review, 3. Insights, 4. Explore.
Learn more about PowerPoint, here:
https://brainly.com/question/19238885
#SPJ2
It is the job of the ____ to enable reliable transmission of data through the physical layer at the sending end. group of answer choices
Answers
Answer:
The statement is true
Explanation:
It is the job of the data link layer to enable reliable transmission of data through the physical layer at the sending end.
What is meant by the data link layer?The data link layer, or layer 2, is the second tier of the seven-layer OSI model of computer networking. This layer is the protocol layer that transports data between nodes on a network segment by crossing the physical layer.
The data link layer is the protocol layer in a program that manages data transfer into and out of a physical link in a network. The data link layer is Layer 2 in the Open Systems Interconnection (OSI) architecture model for a collection of communication protocols.
At the data connection layer, data bits are combined into entities known as frames. Network topologies such as Ethernet exist at the data connection layer. The most commonly used network hardware at the data link is a switch.
To learn more about the data link layer refer to:
https://brainly.com/question/13131540
#SPJ4
For this writing assignment, select a bitcoin wallet provider. You may choose from the list from bitcoin.org, or find another one from your own research. Then, write a
one- to two-page paper describing and evaluating the wallet. What are the wallet's unique features? What does the wallet's website say about its security? What
platform (out of the 5 described in the module) does this wallet fit under?
Answers
You can transfer, receive, and store bitcoin through your online browser using web wallets. Although some types of web wallets offer options for you to maintain control over your private keys.
What does a wallet address look like?Between 26 to 35 characters are used for wallet addresses, and both letters and digits are used. They begin with "1," "3," or "b1," respectively. A sample address is provided. Hexadecimal addresses have 42 characters.
Is digital a provider of wallets?A provider of financial services, l primarily serves as a digital wallet and money transfer platform. Even if your business is primarily online, you can use invoice customers and accept payments. The platform is typically used for sending money to friends and family.
to know more about wallets here:
brainly.com/question/29627571
#SPJ1
The National Archives is part of the federal government, which means that its content:
-belongs to everyone.
-is off limits to the public.
-comes with extreme licensing fees.
-is outdated and useless.
Answers
Answer:
its A
Explanation:
the national archives is open to anyone who visits
(Java) What, in your opinion, is wrong with this nested for loop?
for(int x = 0; x < 10; x++){
for(int x = 10; x > 0; x--){
System.out.println(x);
}
}
Answers
The issue with this nested for loop in Java is the declarationof the second loop variable.
Why is this so?Both loops use the same variable name"x" for iteration. This creates a conflict because the inner loop re-declares the "x" variable, leading to a compilation error.
Each loop should have a unique variable name to avoid naming conflicts and ensure proper loop execution.
The corrected code will be --
for (int x =0; x < 10; x++) {
for (int y = 10;y > 0; y--) {
System.out.println(y);
}
}
Learn more about Java at:
https://brainly.com/question/25458754
#SPJ1
what is an open port and why is it important to close ports on a system that are not being used?
Answers
An open port is a communication endpoint on a device, such as a computer or router, that allows data transmission between different systems or networks.
It enables various services and applications to establish connections and communicate efficiently. Open ports are essential for smooth communication and functionality of internet-based services like web browsing, email, and file transfers. It is crucial to close unused ports on a system to prevent potential security risks. Leaving unused ports open can expose the system to cyber-attacks, as hackers can exploit these entry points to gain unauthorized access, steal sensitive data, or inject malware. Closing unused ports minimizes the attack surface and reduces the chances of a successful breach.
Regularly monitoring and managing open ports can help maintain network security and system stability. By limiting the number of open ports, organizations can better control the flow of data and track potential threats. Closing unused ports is a fundamental step in establishing robust cybersecurity practices and safeguarding valuable digital assets.
Learn more about cybersecurity here: https://brainly.com/question/31928819
#SPJ11
pr professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person.
Answers
PR professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person is true.
What is webcasts?
Webcasts is defined as a media presentation delivered via the Internet that makes use of streaming media technologies to give access to a single content source to numerous listeners and watchers at once.
A kind of strategic communication that strengthens connections between corporations and their audiences. To build, preserve, and safeguard the company's reputation, increase its status, and offer a positive picture.
Thus, PR professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person is true.
To learn more about webcasts, refer to the link below:
https://brainly.com/question/9165574
#SPJ1