Question 4 of 20
most applications will ask you to provide all of the following information
except
a. the date you can start work
b. the dates and hours you are available to work.
c. your desired salary or wage.
d. which of your previous jobs you didn't like.
Answers
Most applications will ask you to provide all of the following information except (d) which of your previous jobs you didn't like. The correct option is D.
Job applications typically require information such as your availability to start work, your preferred work schedule, and your desired salary or wage, as these are relevant to the employer's needs and decision-making process. However, they do not generally ask for personal opinions or preferences about previous jobs, as this is not relevant to the current application.
When filling out job applications, focus on providing the necessary information, such as your availability and desired compensation, and avoid discussing any negative experiences with previous jobs. The correct option is D.
To know more about decision-making process visit:
https://brainly.com/question/29772020
#SPJ11
Related Questions
How can data consolidation be helpful? Check all that apply
•It can set up automatic updating of data within one worksheet.
•it can summarize data from worksheets in different workbooks.
•it helps to summarize data from worksheets that are not identical.
•it combines data from multiple sheets to create one concise table.
• it summarizes data based on how many rows and columns have values.
Answers
Answer:2,3, and 4
Explanation:
Answer:
2,3,4
Explanation:
the four levels of FBLA membership
Answers
Answer:
Future Business Leaders of America (FBLA) for high school students; FBLA-Middle Level for junior high, middle, and intermediate school students; Phi Beta Lambda (PBL) for post secondary students; and Professional Division for those not enrolled in school or post secondary school
Explanation:
What is the difference between an open network and a secure network?
Answers
An open network is a network that allows any device to connect to it without any restrictions or authentication, while a secure network is a network that has some level of security measures in place to prevent unauthorized access.
An open network is convenient because it allows anyone to easily connect to it, but it can also be vulnerable to security risks because it lacks any protection against unauthorized access. In contrast, a secure network uses various security measures such as encryption, authentication, and access controls to prevent unauthorized access and protect the data transmitted over the network. As a result, secure networks are generally more secure than open networks, but they may require additional setup and configuration.
Column is invalid in the select list because it is not contained in either an aggregate function or the group by clause.
a. True
b. False
Answers
The output should have two rows, one with a=1 and one with a=2.
There are three options in each scenario, and nothing in the query indicates which value to use for b in each group. It's unclear.
This exemplifies the single-value rule, which prevents undefined results from occurring when you execute a GROUP BY query and include any columns in the select-list that are neither part of the grouping criterion nor present in aggregate functions (SUM, MIN, MAX, etc.).
select loc.LocationID, emp.EmpID
from Employee as emp full join Location as loc
on emp.LocationID = loc.LocationID
group by loc.LocationID
Learn more about output here-
https://brainly.com/question/18133242
#SPJ4
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
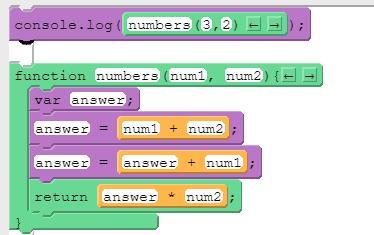
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
Why do companies collect information about consumers? A. Because they want to meet new friends on social networks B. Because they take consumers' best interests to heart C. Because they want to effectively advertise to consumers D. Because they are looking for good employees to hire
Answers
Answer:
C. Because they want to effectively advertise to consumers.
Explanation:
Companies collect info for more accurate advertisements, which are designed to make people interact with them more commonly.
1. Pick two Halloween-related words and search for them using AND in Google search *
Example: Oct.31 AND candy (do not use this combination of words as your answer. These are the example words. Please use your own)
Answers
Answer:
Here are a few to choose from:
candy and costumespumpkins and candyspooky and scarywitches and spellsnight and frightzombies and skeletonsThere you go! Just pick two.
The options on the Ribbon will____:
Answers
replace both the traditional menu bar and toolbars.
Hopefully, It's Correct... (ノ◕ヮ◕)ノ
people who use a/an ________________ design logic believe that the given context determines what type of communication is appropriate.
Answers
People who use a/an contextual design logic believe that the given context determines what type of communication is appropriate.
Contextual design logic emphasizes the importance of considering the specific situation, environment, and audience when determining the most effective and appropriate means of communication. It recognizes that different contexts require different communication strategies and channels to convey information effectively.
By adopting a contextual design logic, individuals or organizations take into account factors such as cultural norms, social dynamics, communication goals, and the characteristics of the intended recipients. This approach helps ensure that the communication is tailored to the specific context, taking into consideration factors such as language, tone, medium, and level of formality.
Contextual design logic encourages a more nuanced and adaptable approach to communication, recognizing that what may be suitable in one context may not be effective or appropriate in another. It promotes sensitivity and responsiveness to the context in order to achieve clear, meaningful, and impactful communication.
learn more about "communication ":- https://brainly.com/question/28153246
#SPJ11
The Ruiz twins saw that they earned $324.55 this month and made the decision to put in more time next month. In this situation, the number $324.55 functions as _____. data information knowledge input
Answers
Answer:
knowledge
Explanation:
The correct option is - knowledge.
Reason -
Knowledge is facts, information, and skills acquired by a person through experience or education
Also knowledge is the theoretical or practical understanding of a subject.
Which of these expressions is used to check whether num is equal to value?
num ? value
num = value
num – value
num == value
Answers
Answer:
num-value
Explanation:
is should equal to zero if it is correct.
Answer:
It is num - value
Explanation:
I got it right on the test
Which practice represents the trait of effective communication
Answers
Answer:
The answer is B. speaking clearly
Explanation:
I hope it's correct sorry if not.
if you have a class defined in separate files, and change the main program, which files need to be re-compiled?
Answers
The application and implementation files must be recompiled if a class is declared in separate files and the main program is changed.
What version of the class file is it?We designate the class file's version as M.m, where M stands for the major version and m for the minor version. Note: Compiler developed by lower version. High version JVM may run class files, but higher version compiler created. Class files cannot be run by JVM versions below that.
What do you name the process of joining the implementation and application files to create an executable file?Linking is the process of combining the implementation and application files to create an executable file.
To learn more about Java class visit:
brainly.com/question/14615266
#SPJ4
The registers are the communication channels inside the computer.( true or false)
Answers
Registers are storage, not channels
What question should you ask yourself before you enter a metaverse experience?
Answers
1. How will the metaverse unfold and transform enterprises?
While converging technologies are unlocking the path to the metaverse, fully connected 3D immersive experiences present a rich opportunity landscape across industries. Enterprises are asking themselves how they should think about the metaverse as they shape future strategy. What investments should they make today to be ready for the metaverse when it arrives?
Just as digital transformation continues to compel companies toward evolving every aspect of their business, similarly an immersive or metaverse transformation will be required. A new field of competitors will open up alongside new markets, new customer preferences and new business models. What new innovation models will emerge? What new skill sets will be required? How will it impact talent management?
Although the pervasive use of the metaverse as the main customer engagement interface is likely a few years away, enterprises need to start factoring it into their short-term and long-term vision today.
Answer:
Am I mentally ready to enter? Are there any ways this device makes me feel uneasy and/or nauseous?
Explanation:
This isn't perfect but I feel this is a solid answer.
also answered so the guy above can get brainliest
The gig economy offers ________.
Answers
Answer:
The number of people in the economy who have full-time employment jobs. The total availability of employment and labor in the economy.
Explanation:
Data analytics tools and methods fall into the following categories—descriptive, predictive, prescriptive, and.
Answers
Data analytics tools and methods are necessary for businesses to analyze their data, gain insights, and make informed decisions.
Descriptive, predictive, and prescriptive are three of the four main categories of data analytics methods, but what is the fourth category? The fourth category of data analytics methods is called "diagnostic."Diagnostic analytics is the method of discovering why a problem happened by examining data and investigating its root cause. It is used to identify patterns in data, diagnose issues, and find potential solutions.
Diagnostic analytics is an essential tool for any business looking to improve its operations, as it allows companies to identify problems before they become critical issues. In summary, the four categories of data analytics methods are descriptive, predictive, prescriptive, and diagnostic. These methods are used to help businesses gain insights from their data and make informed decisions based on their findings.
To know more about methods visit:
https://brainly.com/question/5082157
#SPJ11
The algorithm you worked to train can be used to distinguish more realistic images than the hand-written digits example from the previous module. While distinguishing between animals or vehicles may not pose a serious ethical dilemma, it’s important to consider what other types of images an algorithm such as this could be trained on. For example, could such an algorithm eventually be used to distinguish people’s faces? If so, what are the ethical and privacy implications? Create a Markdown cell in your Jupyter Notebook after your code and its outputs. In this cell, analyze the ethical and privacy implications of the algorithm you just created. You are expected to include resources to support your answers, and must include citations for those resources.
...CODE...
from keras.datasets import cifar10
from keras.utils import np_utils
from keras.models import Sequential
from keras.layers.core import Dense, Dropout, Activation, Flatten
from keras.layers.convolutional import Conv2D, MaxPooling2D
from keras.optimizers import SGD, Adam, RMSprop
import matplotlib.pyplot as plt
# CIFAR_10 is a set of 60K images 32x32 pixels on 3 channels
IMG_CHANNELS = 3
IMG_ROWS = 32
IMG_COLS = 32
#constant
BATCH_SIZE = 128
NB_EPOCH = 20
NB_CLASSES = 10
VERBOSE = 1
VALIDATION_SPLIT = 0.2
OPTIM = RMSprop()
#load dataset
(X_train, y_train), (X_test, y_test) = cifar10.load_data()
print('X_train shape:', X_train.shape)
print(X_train.shape[0], 'train samples')
print(X_test.shape[0], 'test samples')
# convert to categorical
Y_train = np_utils.to_categorical(y_train, NB_CLASSES)
Y_test = np_utils.to_categorical(y_test, NB_CLASSES)
# float and normalization
X_train = X_train.astype('float32')
X_test = X_test.astype('float32')
X_train /= 255
X_test /= 255
# network
model = Sequential()
model.add(Conv2D(32, (3, 3), padding='same',
input_shape=(IMG_ROWS, IMG_COLS, IMG_CHANNELS)))
model.add(Activation('relu'))
model.add(MaxPooling2D(pool_size=(2, 2)))
model.add(Dropout(0.25))
model.add(Flatten())
model.add(Dense(512))
model.add(Activation('relu'))
model.add(Dropout(0.5))
model.add(Dense(NB_CLASSES))
model.add(Activation('softmax'))
model.summary()
# train
model.compile(loss='categorical_crossentropy', optimizer=OPTIM,
metrics=['accuracy'])
model.fit(X_train, Y_train, batch_size=BATCH_SIZE,
epochs=NB_EPOCH, validation_split=VALIDATION_SPLIT,
verbose=VERBOSE)
score = model.evaluate(X_test, Y_test,
batch_size=BATCH_SIZE, verbose=VERBOSE)
print("Test score:", score[0])
print('Test accuracy:', score[1])
#save model
model_json = model.to_json()
open('cifar10_architecture.json', 'w').write(model_json)
#And the weights learned by our deep network on the training set
model.save_weights('cifar10_weights.h5', overwrite=True)
model = Sequential()
model.add(Conv2D(32, (3, 3), padding='same',
input_shape=(IMG_ROWS, IMG_COLS, IMG_CHANNELS)))
model.add(Activation('relu'))
model.add(Conv2D(32, (3, 3), padding='same'))
model.add(Activation('relu'))
model.add(MaxPooling2D(pool_size=(2, 2)))
model.add(Dropout(0.25))
model.add(Conv2D(64, (3, 3), padding='same'))
model.add(Activation('relu'))
model.add(Conv2D(64, 3, 3))
model.add(Activation('relu'))
model.add(MaxPooling2D(pool_size=(2, 2)))
model.add(Dropout(0.25))
model.add(Flatten())
model.add(Dense(512))
model.add(Activation('relu'))
model.add(Dropout(0.5))
model.add(Dense(NB_CLASSES))
model.add(Activation('softmax'))
from keras.preprocessing.image import ImageDataGenerator
from keras.datasets import cifar10
import numpy as np
NUM_TO_AUGMENT=5
#load dataset
(X_train, y_train), (X_test, y_test) = cifar10.load_data()
# augumenting
print("Augmenting training set images...")
datagen = ImageDataGenerator(
rotation_range=40,
width_shift_range=0.2,
height_shift_range=0.2,
zoom_range=0.2,
horizontal_flip=True,
fill_mode='nearest')
xtas, ytas = [], []
for i in range(X_train.shape[0]):
num_aug = 0
x = X_train[i] # (3, 32, 32)
x = x.reshape((1,) + x.shape) # (1, 3, 32, 32)
for x_aug in datagen.flow(x, batch_size=1,
save_to_dir='preview', save_prefix='cifar', save_format='jpeg'):
if num_aug >= NUM_TO_AUGMENT:
break
xtas.append(x_aug[0])
num_aug += 1
#fit the dataget
datagen.fit(X_train)
# train
history = model.fit_generator(datagen.flow(X_train, Y_train,
batch_size=BATCH_SIZE), samples_per_epoch=X_train.shape[0],
epochs=NB_EPOCH, verbose=VERBOSE)
score = model.evaluate(X_test, Y_test,
batch_size=BATCH_SIZE, verbose=VERBOSE)
print("Test score:", score[0])
print('Test accuracy:', score[1])
Answers
The algorithm created here can indeed be used to distinguish more realistic images than hand-written digits.
It is possible for such an algorithm to eventually be trained to distinguish people's faces. However, there are ethical and privacy implications associated with using algorithms for facial recognition:
1. Consent: People may not be aware or have given consent for their images to be used in training or recognition tasks, which could infringe on their privacy rights.
2. Data protection: Ensuring the security of collected facial data is essential to protect people's privacy. If not properly protected, this data could be misused or stolen.
3. Bias: If the training dataset is not diverse, the algorithm could discriminate against certain groups of people, leading to unfair treatment or exclusion.
4. Surveillance: Widespread use of facial recognition technology may lead to excessive surveillance, affecting people's freedom and creating a "big brother" society.
5. Misidentification: False positives or negatives may lead to wrongful accusations, affecting people's lives and reputations.
To address these ethical and privacy concerns, developers should ensure transparency, accountability, and responsibility in the design and deployment of such algorithms. They should also adhere to local laws and regulations on data protection and privacy.
Learn more about security visit:
https://brainly.com/question/15278726
#SPJ11
what is a coding process that takes a digital map feature and assigns it an attribute that serves as a unique id (tract number, node number) or classification (soil type, zoning category)?
Answers
Answer:
Geocoding in spatial databases
Explanation:
This is a coding process that assigns a digital map feature to an attribute that serves as a unique ID (tract number, node number) or classification (soil type, zoning category).
Hope this helps!
Create a method addVehicle which takes fields of Vehicle in the order of number,name,price and adds the same to Vehicle list if there is no object present in the list with same value of number. The above method should throw the exception.Handle the exception in the main method. Return -1 if there is an object with the same value of number else return the total count of Vehicle objects in the list. Create a class CustomerDemo with a main method.Create an object of Customer and call the above method from the main method.
Answers
The method add Vehicle in the class Customer Demo should be called from the main method of the Customer Demo class.
How can the add Vehicle method be implemented to fulfill the given requirements?To implement the add Vehicle method, you can follow these steps:
1. Create an ArrayList to store the Vehicle objects.
2. Define the add Vehicle method with the required parameters: number, name, and price.
3. In the add Vehicle method, iterate through the list of vehicles and check if any vehicle object already has the same value of the number field. If found, throw an exception.
4. If no vehicle object is found with the same number, create a new Vehicle object using the provided fields and add it to the list.
5. After the loop, check the size of the vehicle list. If it has increased, return the new count of Vehicle objects.
6. If the size remains the same, return -1 to indicate that a vehicle with the same number already exists in the list.
Learn more about Customer Demo
brainly.com/question/10678770
#SPJ11
¿Quién recibe la orden de ejecución de un programa enviada por el usuario?
Answers
Answer:
El sistema operativo.
Explanation:
En ciencias de la computación, una orden es una instrucción a un sistema operativo de computadora para realizar una tarea específica. Generalmente, una orden se emite a través de una interfaz de línea de órdenes de otro programa. Así, se trata de una instrucción a un programa de computadora para que actúe como intérprete para resolver un problema.
Por ejemplo, podemos pedir a través de una orden que muestre el contenido de una carpeta, buscar un archivo en particular y especificar mediante parámetros adicionales cómo se debe realizar esta acción (por ejemplo, utilizando expresiones regulares para realizar una búsqueda).
which two definitions accurately describe the associated application layer protocol? (choose two.)
Answers
The associated application layer protocol can be accurately described as the rules and formats for exchanging data between applications over a network, as well as the set of services and functionalities that enable applications to communicate with each other.
How can the associated application layer protocol be accurately described?To accurately describe the associated application layer protocol, two possible definitions are:
The application layer protocol defines the rules and formats for exchanging data between applications over a network. It specifies the structure of messages, the order of message exchange, and the actions to be taken upon message reception.The application layer protocol provides a set of services and functionalities that enable applications to communicate with each other. It abstracts the underlying network complexities and provides a standardized interface for application developers to interact with network resources.These definitions highlight the role of the application layer protocol in facilitating communication and providing a common framework for application-level interactions in a networked environment.
Learn more about application layer protocol
brainly.com/question/30156428
#SPJ11
LabConnection Skip This Step Show Me Reset instructions Which statement about file history is incorrect? . Can be used with a USB Flash drive • Can store data on network share • The backup folders create a system image All statements are correct.
Answers
The statement about the file history "The backup folders create a system image" is incorrect.
File history is a feature in Windows that allows users to automatically back up and restore their personal files. It provides an easy way to protect important documents, photos, and other files from accidental deletion, loss, or corruption.
While file history offers several useful capabilities, including the ability to use a USB flash drive for backup and store data on a network share, it does not create a system image through backup folders.
System image creation is a separate feature in Windows that creates a complete copy of the entire system, including the operating system, installed programs, settings, and files. It is typically used for system recovery purposes and allows for a full restoration of the system to a previous state.
This feature is not directly related to file history and is not part of the file history backup process.
It's important to note that file history focuses on backing up and restoring personal files, while system image creation is more comprehensive and involves capturing the entire system's configuration. Understanding the distinction between these features can help users choose the appropriate backup strategy based on their specific needs.
Learn more about system image
brainly.com/question/29972729
#SPJ11
If I replace this screen with these black spots go away?

Answers
Yes I'm sure they would, these black spots are being caused due to a broken screen!
Hope this helps!!
Dibuja una palanca e indica el nombre de los elementos que la componen
Answers
La palanca es una herramienta simple que se utiliza para aplicar una fuerza a un objeto, con el objetivo de moverlo o levantarlo. Está compuesta por tres elementos principales: el punto de apoyo (fulcro), la fuerza aplicada (fuerza motriz) y la carga (resistencia).
Para dibujar una palanca, dibuja una línea recta y horizontal para representar la barra de la palanca. Luego, dibuja un punto para representar el fulcro. La distancia entre el fulcro y la fuerza motriz (el punto donde se aplica la fuerza) se llama el brazo de la fuerza motriz. La distancia entre el fulcro y la carga se llama el brazo de la resistencia.La fórmula que se utiliza para calcular la relación entre la fuerza aplicada y la resistencia es: Fuerza motriz x brazo de la fuerza motriz = Resistencia x brazo de la resistencia.Por ejemplo, si la fuerza motriz es de 10 N y el brazo de la fuerza motriz es de 2 m, y la resistencia es de 20 N y el brazo de la resistencia es de 1 m, entonces la relación sería 10 N x 2 m = 20 N x 1 m.
To learn more about elementos click the link below:
brainly.com/question/16665980
#SPJ4
Applying a bug fix:
Addressing a security flaw:
Improving ease of use:
Adding new features:
<>
1.software update(patch)
2.software update(patch)
3.software upgrade(new version)
4.software upgrade(new version)
Answers
Addressing a security flaw: software update (patch)
Improve ease of use: Software Update (new version)
Adding features: Software Update (new version)
This is what I believe the answer is! Hope this helped!
The matching of item A with respect to item B is as follows:
Software update (patch): Applying a bug fix. Software update (patch): Addressing a security flaw.Software Upgrade (new version): Improve ease of use:Software Upgrade (new version): Adding features. What is a Software update?A software update may be characterized as a set of changes to the software to update, fix or improve it. It also changes to the software will usually either fix bugs, fix security vulnerabilities, provide new features or improve performance and usability. It is also known as a patch.
Software updates provide more than just security updates, they often offer new and improved features and speed enhancements to make the end-user experience better. Developers are constantly working on ways to improve the software, giving greater efficiency to users.
Therefore, the matching of item A with respect to item B is well described above.
To learn more about the Software update, refer to the link:
https://brainly.com/question/5057366
#SPJ2
Select the correct answers.
Which are the benefits of leveraging web technologies?
processing of large amounts of data
more manpower
better marketing and customer service
increased production costs
difficulty in handling customer complaints

Answers
Answer:
Explanation:
Select the correct answers.
Which are the benefits of leveraging web technologies?
1) Processing of large amounts of data
2) Better marketing and customer service
when c is working with an operator, it strives to convert operands to the same type. this is known as group of answer choices
Answers
D) Promotion. In C++, when working with an operator, the operands are typically converted to a common type, known as "promotion."
C++ is done to ensure that the operator can be applied correctly to the operands and to prevent any unnecessary loss of precision. For example, if an operator is applied to a short int and an int, the short int will be promoted to an int before the operator is applied. Code refers to a set of instructions or statements that a computer or machine can interpret and execute. It is written in a programming language, and is used to create software and apps.
The complete question is:
When C++ is working with an operator, it strives to convert operands to the same type. This is known as
A) type correction
B) type conversion
C) demotion
D) promotion
E) None of these. explain your answer
Learn more about C++, here https://brainly.com/question/497311
#SPJ4
a user called to inform you that the laptop she purchased yesterday is malfunctioning and will not connect to her wireless network. you personally checked to verify that the wireless worked properly before the user left your office. the user states she rebooted the computer several times but the problem still persists.
Answers
The user should enable the wireless radio by pressing the proper function keys, and then they should try to connect to the wireless network.
What should one do as soon as possible when using a computer for work?Turning on the computer is the first thing to do. Locate and push the power button to accomplish this. Every computer has a power button, albeit it is located differently on each one. Your computer takes a while to start up after being turned on.
What indicate a computer is about to fail?Your computer may start to lag, freeze, crash, or start to send error messages. If numerous programs are performing strangely and the issues continue even after rebooting, this is quite concerning.
To know more about wireless network visit:-
https://brainly.com/question/14921244
#SPJ4
Question:-
A user called to inform you that the laptop she purchased yesterday is malfunctioning and will not connect to the wireless network. You personally checked to verify that the wireless worked properly before the user left your office. The user states she rebooted the computer several times but the problem still persists. Which of the following is the first step you should take to assist the user in resolving this issue?
If a driver update creates a problem, you can __________________ the driver update if the previous drivers were working.
Answers
Answer:
rollback the driver update if the previous drivers were working